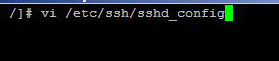
Having the option of logging in to your server with SSH is essential for some web administrators, but logging in your server with root credentials via SSH is always unsafe. By the word root credentials, I mean that you should not remotely login with your server with root user name, rather use a less privileged user to login to your server and then use the "su" command to login … [Read more...] about How to Disable Root Login Via SSH in Linux
Network Security Tips
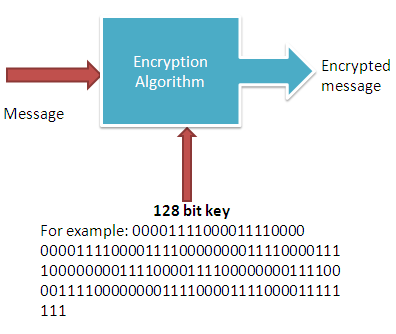
What is 128 Bit Encryption?Why the Length is Important?
The purpose of any cryptography is to ensure the confidentiality, authenticity, non-repudiation and integrity of the data. And all these goals are achieved with the use of cryptography keys. The 128 bit key is such a type of key that ensure all the intended objectives of using a crypto-system or cryptographic algorithm.it is the key which needs to be secret in order to keep … [Read more...] about What is 128 Bit Encryption?Why the Length is Important?
What is VPN and How it Works?
By reading this post you can learn about VPN and its workings. VPN is just a term we use to describe a system which makes communication between two computers, regardless of how far they are, within a secure channel. Here the secure channel means you can convert the public network secure. As you know that a public network is nothing but the Internet, where can have access to any … [Read more...] about What is VPN and How it Works?
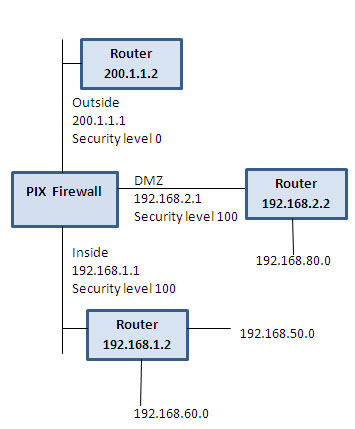
PIX Firewall Configuration Basics
This post intends to familiarize you with some of the basics skills that you need to configure a PIX firewall. The configuration commands will help you to assign name to a PIX interface to configure routing and to configure network address translation including PAT(port address translation). To erase configuration: write erase To save configuration: write terminal … [Read more...] about PIX Firewall Configuration Basics
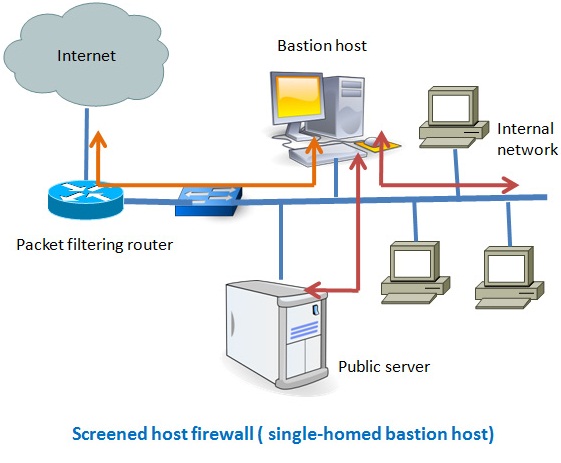
7 Different Types of Firewalls
There are several types of firewalls that work on different layers of the OSI model. Depending on the kind of service and security you need for your network, you need to choose the right type of firewall. The following are the list of seven different types firewalls that are widely used for network security. Screened host firewalls Screened subnet firewalls Packet … [Read more...] about 7 Different Types of Firewalls
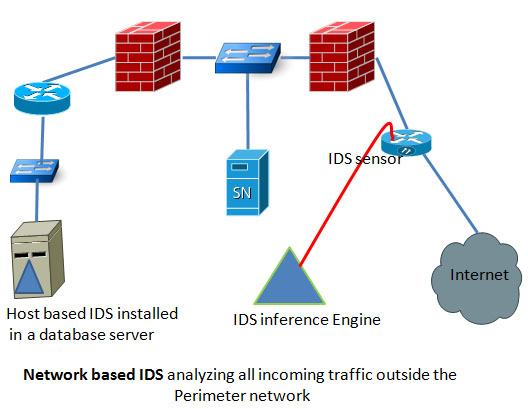
Host Based IDS vs Network Based IDS
Based on the location in a network, IDS can be categorized into two groups. One is host based IDS and the other is network based IDS. Both have its own advantages and distant ages. Before you decide which IDS suits your network environment the best you need to have a clear concept of both types of IDS. Network based IDS: these types of IDS are strategically positioned in a … [Read more...] about Host Based IDS vs Network Based IDS
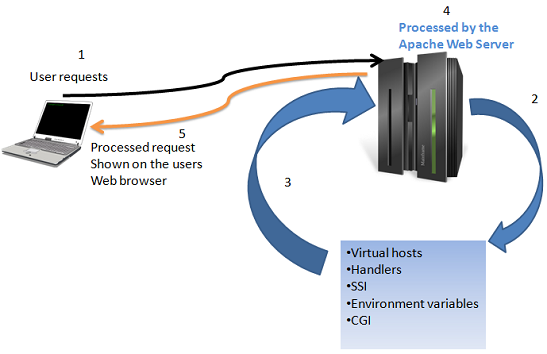
Apache Server Features with Vulnerabilities
Apache is one of the prevalent web servers because of its expandability with features, support community and cost. If you consider using Apache as a solution to your web server and want to implement the most basic security requirements, then you need to have clear understanding of some of the most ubiquitous features of Apache and those features are: Virtual hosts Server … [Read more...] about Apache Server Features with Vulnerabilities
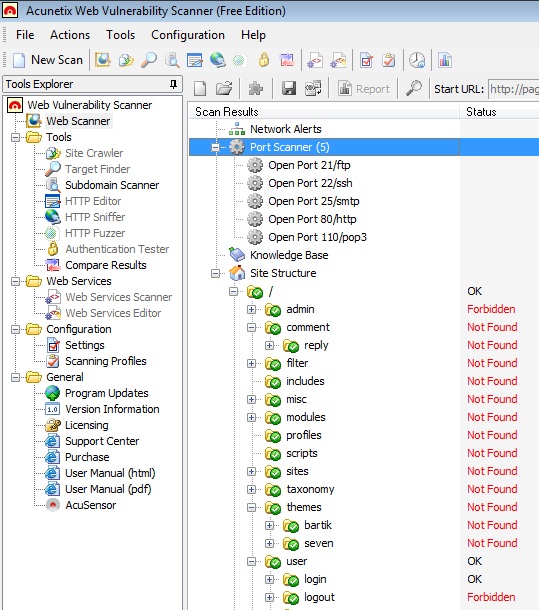
Acunetix Web Vulnerability Scanner to Detect your Website’s Security Loopholes
Acunetix web vulnerability scanner help to find vulnerability in a website so as you can make your site or blog as secure as possible. Acunetix has a free version that you can use to find some of the common vulnerabilities of a website.In this article I will show you how you can use the free version of acunetix to figure out how much secure you blog is.Although Acunetix has a … [Read more...] about Acunetix Web Vulnerability Scanner to Detect your Website’s Security Loopholes
Active Directory Security Checklists
As you know that in a Windows based domain system, active directory is the central management tool that provides access controls to users to the servers or to use any services offered by any specific servers. So, security in Windows based infrastructure should start with securing the active directory. Though most of the part of securing an active directory process focus on … [Read more...] about Active Directory Security Checklists
Linux Security Basics
The purpose of the Linux security checklist is to help the Linux users, entry-level, to become familiar with the most common security vulnerability of Linux operations systems. As you know security checking needs to be verified against well established practices, the following steps are necessary to following before starting your Linux security checking. Version number of … [Read more...] about Linux Security Basics
Physical Security of Information Assets
Without paying proper attention to the physical security of information asset your IT assets and infrastructure are always under security threats from known or unknown sources or from accidental hazards. An IT security manager or designer will always need to pay equal or even more attention to ensure that his all the information assets are physically secured. It is not … [Read more...] about Physical Security of Information Assets