When a piece of information is crucial and can cause serious damage to the national security can be considered classified information. Based on the severity of the damage, classified information can be categorized as top secret (if leaked can cause highest level of damage), secret and confidential (will not cause significant damage if confidential information get leaked). … [Read more...] about 12 Things to Remember when Handling Classified Information
security tips
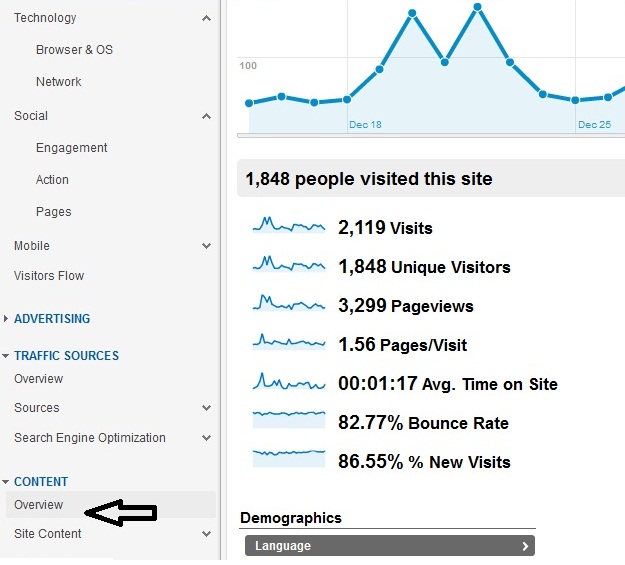
Google Analytics for IT Security Professionals
What is Google Analytics? In short Google analytics is a website statistics tracking tool that you can use to track how your users are interacting with your WebPages such as which pages are being visited the most and where the visitors came from or what keywords he used to find your pages. Who should use Google Analytics? IT professionals( both in operation and security) … [Read more...] about Google Analytics for IT Security Professionals
WordPress Security Best Practices
With every update, WordPress improves its security capabilities and fix the vulnerabilities. As you know that the default configuration is always risky. To secure a site you always need to customize your security settings, which means apply the best security practices for your blogging platform. If you are a new WordPress user, you might go through a steep learning curve … [Read more...] about WordPress Security Best Practices
Cisco Router Security Check for Auditor
Since router is the key to access an organization's network from the outside world, the maximum security priority should be given to routers that are connected to the Internet and to the important application servers. ISO-27001 has already defined standard router security checklist, which any organization can use to improve their router securities. This post aims to … [Read more...] about Cisco Router Security Check for Auditor
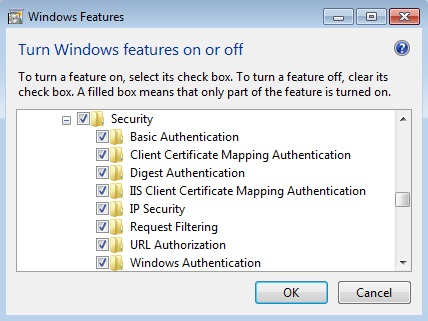
IIS Security Settings
The version of IIS is all about its modules and functions. If you are just learning IIS then before reading this article, it is better to take a closer look at the IIS manger on your server and then go through the following instructions. To secure your IIS server you need to put some extra care to the following settings of IIS server IIS authentication IPv4 and domain … [Read more...] about IIS Security Settings
Active Directory Security Checklists
As you know that in a Windows based domain system, active directory is the central management tool that provides access controls to users to the servers or to use any services offered by any specific servers. So, security in Windows based infrastructure should start with securing the active directory. Though most of the part of securing an active directory process focus on … [Read more...] about Active Directory Security Checklists
Linux Security Basics
The purpose of the Linux security checklist is to help the Linux users, entry-level, to become familiar with the most common security vulnerability of Linux operations systems. As you know security checking needs to be verified against well established practices, the following steps are necessary to following before starting your Linux security checking. Version number of … [Read more...] about Linux Security Basics
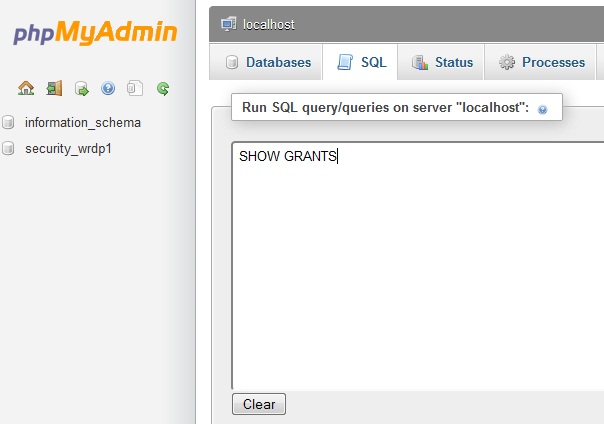
MySQL Security Settings Checklist and Issues
Securing MySQL requires not only hardening the security configuration of your database itself but also the web server along with the operating system. As you know that most of the web hosting provider love Linux and Apache as part of their web-hosting solution, you need to make sure that your host is taking proper security measures to ensure tighter control of Apache and OS. … [Read more...] about MySQL Security Settings Checklist and Issues
Physical Security of Information Assets
Without paying proper attention to the physical security of information asset your IT assets and infrastructure are always under security threats from known or unknown sources or from accidental hazards. An IT security manager or designer will always need to pay equal or even more attention to ensure that his all the information assets are physically secured. It is not … [Read more...] about Physical Security of Information Assets
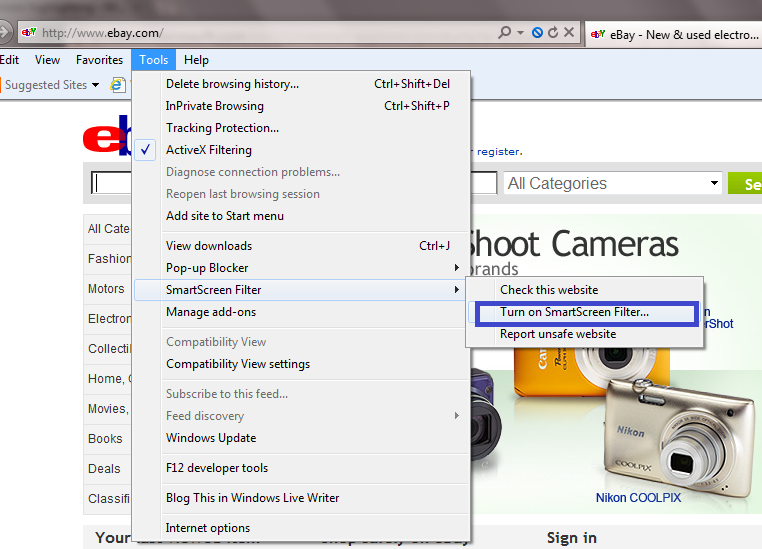
Internet Explorer Security Settings Configuration Guide
The foundation of safer browsing experience depends on how much secure your web browser is. When you install any web browser such as Internet Explorer, you get a default security setting, which may not be suitable for your web privacy and data integrity.This article aims to help you to learn a few useful security tips of Microsoft IE 9. With the new Internet explorer version 9 … [Read more...] about Internet Explorer Security Settings Configuration Guide
Gmail Security Settings Checklist for Secure Login
Whether you are new Gmail User or not, one thing is true that you don’t like to lose your privacy or don’t want to your email security be compromised by any third party or by your business competitors. For making sure that your Gmail account is fully secure and no one is snooping your private emails, you need to follow several steps which are also recommended by Gmail … [Read more...] about Gmail Security Settings Checklist for Secure Login
Computer Security Essentials
The major threats a computer user may expect are – the damage of his stored data or software and stealing of confidential information. A computer can get infected with malicious programs like virus, Trojan, crimeware, spyware, malware or anything else, but the main challenge in front of you is to keep your all the data safe and also to keep your confidential information private … [Read more...] about Computer Security Essentials
Screening Router Security Test
Much small-scale business does not use firewall as their first line of defense any web attacks to their internal network. Instead, they use a router between the Internet and Internal network to control incoming and outgoing traffic flow- this type of use of router is known as screening router. In fact, configuring ACLs inside a router can be a viable and effective solution … [Read more...] about Screening Router Security Test