This post is to help you learn about five effective open-source host-based intrusion detection software.The success of a host-based intrusion detection system depends on how you set the rules to monitor your files integrity. So, while configuring you need to remember that if you do not include the directories that you want to protect, the IDS will not detect anyting and a … [Read more...] about 5 Open-Source Host Based IDS Software to Detect Intrusion
ids
How to Respond to Network Intrusion Detection
When your intrusion detection system triggers an intrusion alarm, you need to respond quickly to minimize the effects of the intrusion. The longer it takes to respond the higher the chances that your system will be damaged severely. If you do not have proper plan and concepts of what you have to do when you detect or suspect an intrusion, you will only panic for nothing and … [Read more...] about How to Respond to Network Intrusion Detection
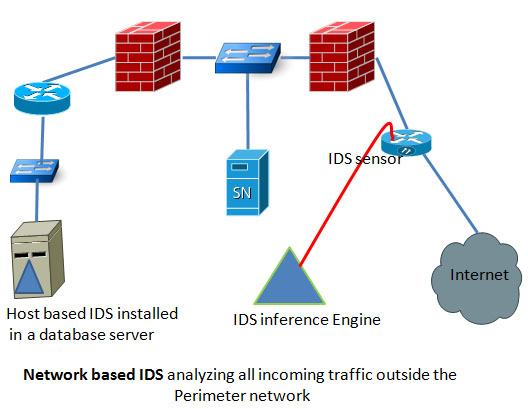
Host Based IDS vs Network Based IDS
Based on the location in a network, IDS can be categorized into two groups. One is host based IDS and the other is network based IDS. Both have its own advantages and distant ages. Before you decide which IDS suits your network environment the best you need to have a clear concept of both types of IDS. Network based IDS: these types of IDS are strategically positioned in a … [Read more...] about Host Based IDS vs Network Based IDS
What is IDS?Basics of Intrusion Detection Systems
The full form of IDS is: Intrusion Detection System. How many of you have heard about burglary? I guess everyone including children. How the burglar is so successful in intruding men's safe heaven? The answer is when there is no system exists to control the access to your house or office, and then ample of opportunities might arise to misuse or steal your valuable belongings. … [Read more...] about What is IDS?Basics of Intrusion Detection Systems