The demand for professional IT auditors is greater than ever due to the increasing digitalization of every aspect of business and industry. Starting a career as an IT auditor involves a combination of education, experience, and strategic planning. Here are ten tips to help you begin and succeed in this field: … [Read more...] about Top 10 Tips to Start a Career as an IT Auditor
IS Audit
32 Proven VOIP Security Best Practices
VOIP saves money if you can deploy and manage it properly, but there are certain risks that you need to take into account. As you know that VOIP is ip based voice solution and IP network is always vulnerable and point of interest to the intruders. … [Read more...] about 32 Proven VOIP Security Best Practices
12 Things to Remember when Handling Classified Information
When a piece of information is crucial and can cause serious damage to the national security can be considered classified information. Based on the severity of the damage, classified information can be categorized as top secret (if leaked can cause highest level of damage), secret and confidential (will not cause significant damage if confidential information get leaked). … [Read more...] about 12 Things to Remember when Handling Classified Information
List of Popular IT Security Standards
The good news for IT security professionals is that there are a number of IT security standards that they can use as a guideline when developing or implementing IT projects. Remember that these standards are well thought out and proven practices that can improve information security goals of your organization. Only the popular and globally recognized IT security standards have … [Read more...] about List of Popular IT Security Standards
Data Breach Insurance Explained
What is data breach insurance? As more and more people are getting accustomed to cyber life, the more money is pouring into the Internet and internet-related business. As a result, we are witnessing more incidents of data breach incidents each year. The fact about Internet security is that no business is secure when they go online and the threat landscape is getting more … [Read more...] about Data Breach Insurance Explained
20 Forensic Investigation Tools for Windows
To investigate Windows system security breach for any potential security breach, investigators need to collect forensic evidence. Microsoft has developed a number of free tools that any security investigator can use for his forensic analysis. This post will give you a list of easy-to-use and free forensic tools, include a few command line utilities and commands. … [Read more...] about 20 Forensic Investigation Tools for Windows
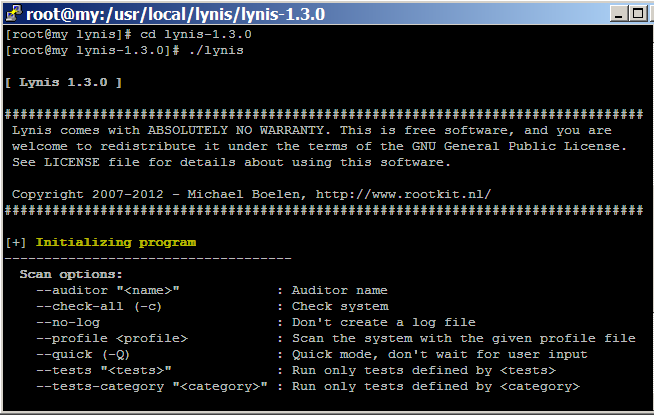
How to audit Linux CentOS Security with Lynis
Hardening Linux security may seem to be a daunting task for new Linux administrator and security auditor if they try to do it manually. Lynis automates the process of Linux security audit, which is widely used by system administrator, IT security auditor and security specialists. When you run Lynis to scan a system, it generates a report and suggestions that helps to patch up … [Read more...] about How to audit Linux CentOS Security with Lynis
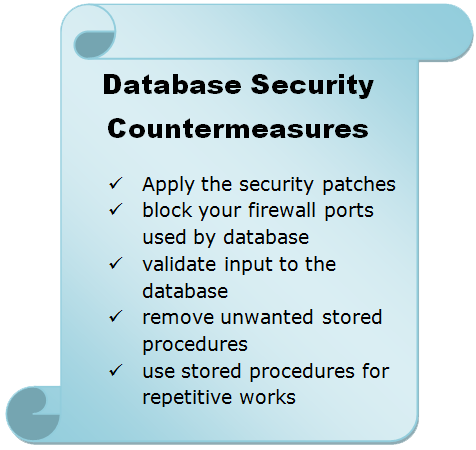
Database Security Issues and Countermeasures
One of the least prioritize part in data base security is not taking countermeasures against database access. Some solid measures that you can take to secure the access methods in your database are: Whether you use Oracle database or Microsoft SQL database, both the organization releases their security patch almost regular basis. So, make sure that you visit the security … [Read more...] about Database Security Issues and Countermeasures
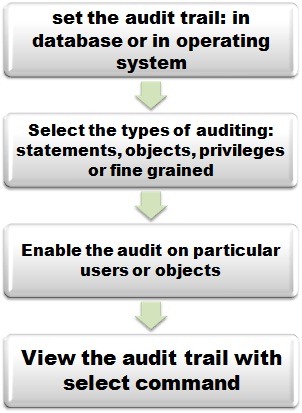
Oracle Audit Setting Commands
An auditor needs to check the Oracle database in order to gather some useful and important information to conduct his audit. In fact, an auditor will ask the system administrator to run the commands and collect the information on behalf of him. The following are the basic commands that you need to know before starting the proper audit of the audit trail. To get a list of all … [Read more...] about Oracle Audit Setting Commands
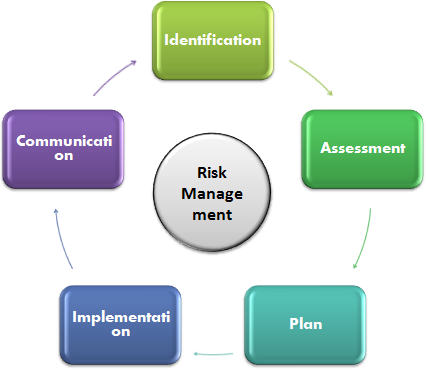
Risk Management Process Simplified
Risk is the possibility of happening unknown or known events that can affect the main objectives of a project. It is not necessary that all the risk will cause disruption in achieving objectives of a goal because a risk can come in the form of a threat or an opportunity. If it comes as an opportunity that it will help the project to get benefit out of it. If you want to keep … [Read more...] about Risk Management Process Simplified
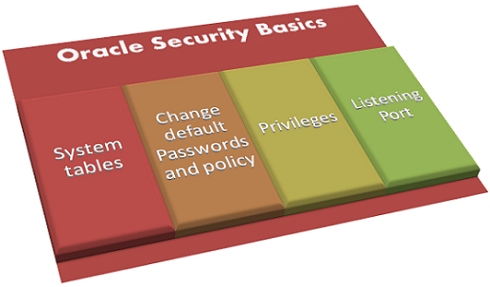
Oracle Security Basics
Popularity has a price to pay since everything on this world has its face value. And Oracle database software is no different than that. In this post, you may expect to have some basic idea on Oracle security and its risks. The features of Oracle that has security risks are: System tables Passwords Privileges Oracle Listener … [Read more...] about Oracle Security Basics
Audit Charter Explained
What is an Audit charter? An audit charter is the base of an audit because every auditor starts his audit with an audit charter. In simple words, an audit charter defines the responsibilities, authority and accountability of an auditor along with the scope of the audit. Normally, a charter also specify the management’s responsibility and their delegation of authority to the IS … [Read more...] about Audit Charter Explained
11 Essential Skills of an IT Auditor
Without proper knowledge of the information technology and systems that you are going to assess, it is almost impossible to audit IT systems.to find the flaws in a system you must know, at least, how it works and its potential vulnerabilities. So, the essential skills an IT auditor need are database, operating systems, web technologies, networking and business processes. The … [Read more...] about 11 Essential Skills of an IT Auditor
What is IDS?Basics of Intrusion Detection Systems
The full form of IDS is: Intrusion Detection System. How many of you have heard about burglary? I guess everyone including children. How the burglar is so successful in intruding men's safe heaven? The answer is when there is no system exists to control the access to your house or office, and then ample of opportunities might arise to misuse or steal your valuable belongings. … [Read more...] about What is IDS?Basics of Intrusion Detection Systems