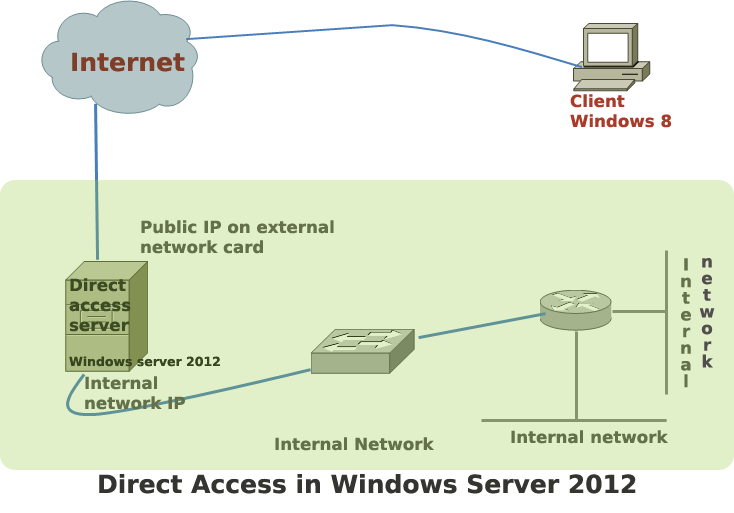
Direct access is the commercial name of Windows 2012 server’s remote access solution. In earlier versions of Windows, remote access offered limited features to the remote users. Windows 2012 is the first Microsoft server that makes remote access users feel like working within the corporate network. … [Read more...] about Steps to Configure Direct Access in Windows Server 2012
server
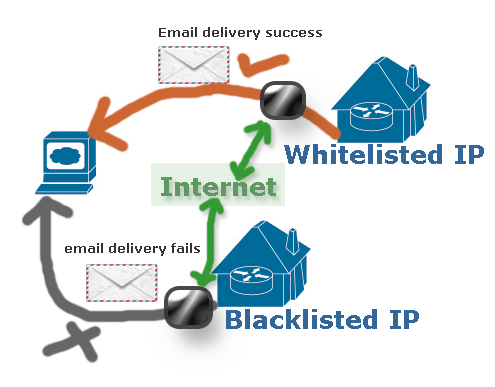
How to Check BlackListed IP of WebServer and Website
The purpose of this post is to show a layman how to check if a IP is in the blacklist of white list. You may need to buy a webhosting plan for your website, and after configuring your site you discovered that your site fails to deliver emails. If that is the case, you need to check if the IP address assigned to your site by your hosting provider is in white list or black … [Read more...] about How to Check BlackListed IP of WebServer and Website
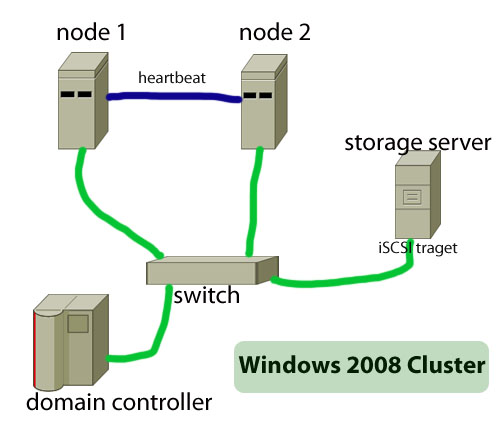
How to Build Failover Cluster in Windows Server 2008
The main objective of a failover cluster is to ensure high availability of services. A failover cluster means that only one server--which is also known as active server--in the cluster will provide the service such as a file server or webserver. When this active server will go offline or will be out of service, another server in the cluster will provide the same service, … [Read more...] about How to Build Failover Cluster in Windows Server 2008
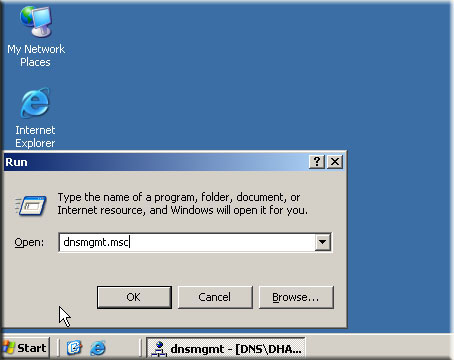
Windows DNS Server Configuration
DNS or domain name system is one of the most important parts of client-server model. Without a DNS no client could be part of a domain and there will be no way you can convert domain name into the IP address of the server. In this post you will find basic procedures that you can use to configure DNS for your domain controller. Though the procedures described in this post is … [Read more...] about Windows DNS Server Configuration