Having an overall understanding of the existing digital security risk can help to design a decisive risk mitigation plan. Both small and large businesses are exposed to similar types of digital risk, which can cause serious damage to businesses unless handled carefully. The list below explains the nine types of digital risks you need to stay alert of. 1. Data risk- as you … [Read more...] about 9 Types of Digital Security Risks
Internet Security and Safety
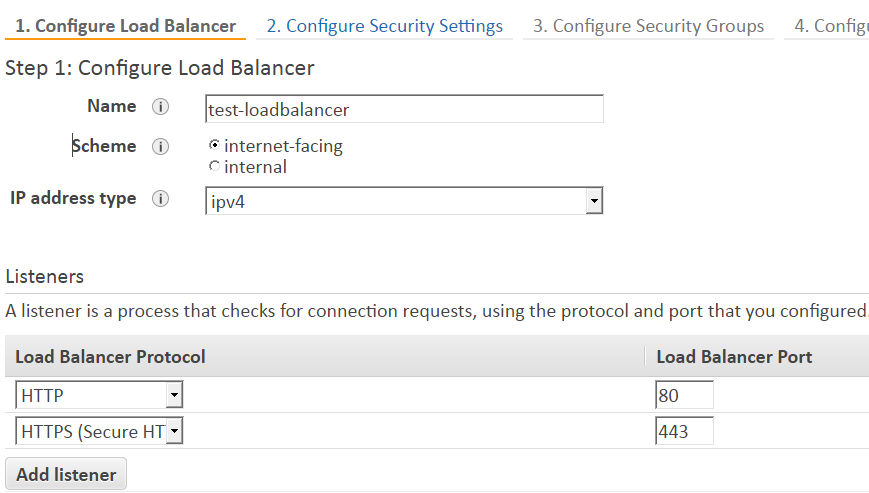
How to Setup SSL in AWS application load balancer for WordPress
How to setup SSL in AWS application load balancer for WordPress. AWS application load balance helps to off load the web server by taking the responsibility of encrypting and decrypting the SSL connection. To implement SSL in WordPress you need to apply the SSL certification only on the load balancer. However, you still need to add the certificate in the server if you want … [Read more...] about How to Setup SSL in AWS application load balancer for WordPress
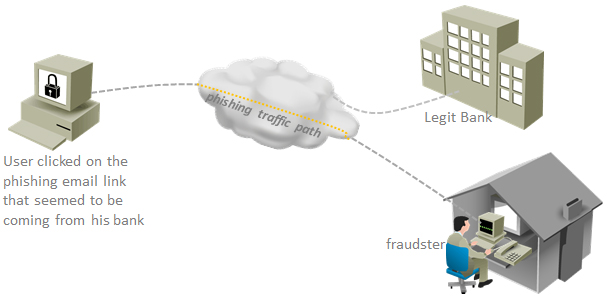
5 Ways to Prevent Online Banking Fraud
If you are a frequent user of online banking, you may take a few necessary steps to protect against online banking fraud. Online banking fraud is all about gaining access to your online bank account by stealing sensitive information. The most important element to protect your online account is to become aware of the ways your account information may fall into the hand of the … [Read more...] about 5 Ways to Prevent Online Banking Fraud
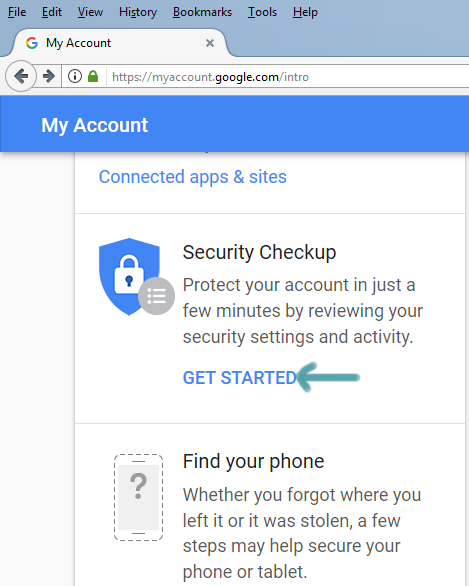
3 Simple Steps to Secure Gmail Account from Hackers
There can be various reasons why hackers want to gain access to your account. Once they gain access to your Gmail account, hackers can use it for various purpose and they post aims to help you secure Gmail account so that you can regain access to your Gmail even if your account password get compromised. … [Read more...] about 3 Simple Steps to Secure Gmail Account from Hackers
Top 12 Effective Ransomware Protection Tips
What is ransomware? Ransomware belongs to the family of malware used to take control of users’ machines and the users get back control of the machine when the victim pays a ransom to the attackers. There are a number of preventive steps that a user can take to avoid ransomware attacks. But before delving depth into the ransomware prevention techniques, you need to know a bit … [Read more...] about Top 12 Effective Ransomware Protection Tips
Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
Both children and adults are vulnerable to various types of cybercrimes. If you ever become a victim of such crime you may do a number of things, from reporting to the stop using online activities unless the threat is neutralized, in order to deal with the problem. The ways to deal with cybercrime has been given below: … [Read more...] about Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
11 Symptoms to Identify if Someone has Internet Addiction
Only a handful of research has been undertaken so far about the symptoms of Internet addiction. I have gathered a few major points that may give you a clear signal if someone is addicted to the Internet. You can use the following points as a reference to identify if you, your kids or anyone you care about have fallen victim to the Internet addiction. … [Read more...] about 11 Symptoms to Identify if Someone has Internet Addiction
Top 6 Side Effects and Health Risk of Gaming Addiction for Kids
If you are a parent, it is essential for you to be aware to the consequence of excessive using of computer playing games.This post aims to highlight a number of major issue that may cause harm to your kids if they play video games too long. … [Read more...] about Top 6 Side Effects and Health Risk of Gaming Addiction for Kids
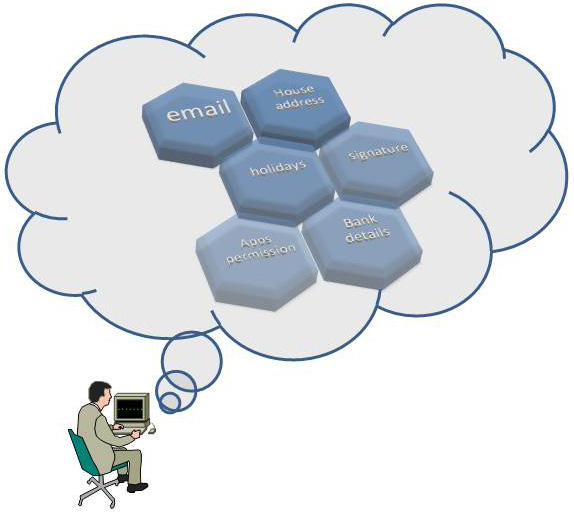
Top 10 Things You Should not Post and Share Online via Social Media
Interesting contents shared in the social media attracts everyone and that is one of the reasons of social media’s popularity. But if you want to stay safe online you need to know which information is not safe sharing on social media and on others websites, forums etc. The following are the list of things you should not share online via social networking websites or any other … [Read more...] about Top 10 Things You Should not Post and Share Online via Social Media
20 Types of Database Security to Defend Against Data Breach
In today’s cyber security, landscape database is considered to be the most important asset of an organization, which holds sensitive information about the business and employees . Having installed and configured firewalls, IDS and end point security, one should not expect that the database is secure and there is no way anyone can breach data. Most of the major data breach … [Read more...] about 20 Types of Database Security to Defend Against Data Breach
How to Renew Self-Signed SSL Certificate with OpenSSL Tool in Linux
OpenSSL is a free and open-source SSL solution that anyone can use for personal and commercial purpose. Though it is free, it can expire and you may need to renew it. This post will you how to renew self- signed certificate with OpenSSL tool in Linux server. … [Read more...] about How to Renew Self-Signed SSL Certificate with OpenSSL Tool in Linux
Effective Ways to Prevent Cross Site Scripting(XSS) Attacks
Not every developers pay equal importance to web security and vulnerabilities, especially about cross site scripting when they start coding. Their primary goal is to get the project finished Websites developed with unsecure coding can be easily exploited by the attackers. There is no way your browser will prevent XSS automatically unless you disable your browser’s ability to … [Read more...] about Effective Ways to Prevent Cross Site Scripting(XSS) Attacks
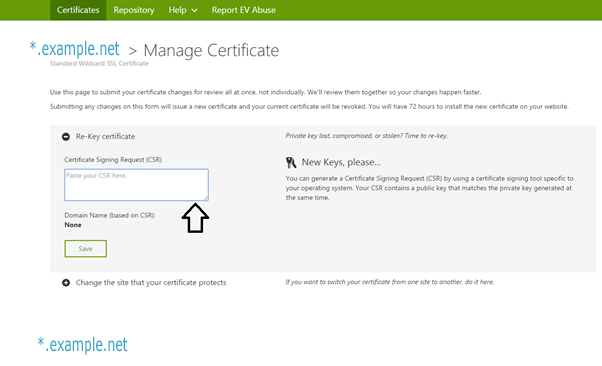
How to install a new Godaddy SSL Wildcard Certificate
This post has been intended for the first time users who want to install GoDaddy SSL certificate in their website. The procedures described here should work well with Apache server and with Nginx. Steps to take before installing GoDaddy SSL To install a digital certificate, you must first generate and submit a Certificate Signing Request (CSR) to the Certification … [Read more...] about How to install a new Godaddy SSL Wildcard Certificate
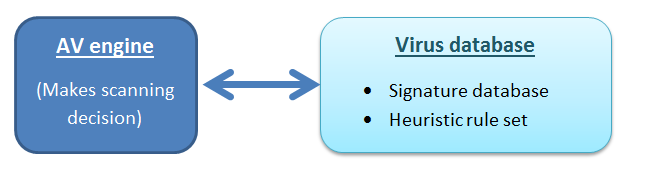
Why Antivirus Software Fails to Detect Latest Viruses and Malwares
We use antivirus software in the hope of having a secure system. Though any virus detecting software can detect viruses, we need to know that there are instances when viruses and malware remain undetected. The post aims to give you a brief idea on the situation when your antivirus may fail to detect the presence of malware in your computer. … [Read more...] about Why Antivirus Software Fails to Detect Latest Viruses and Malwares
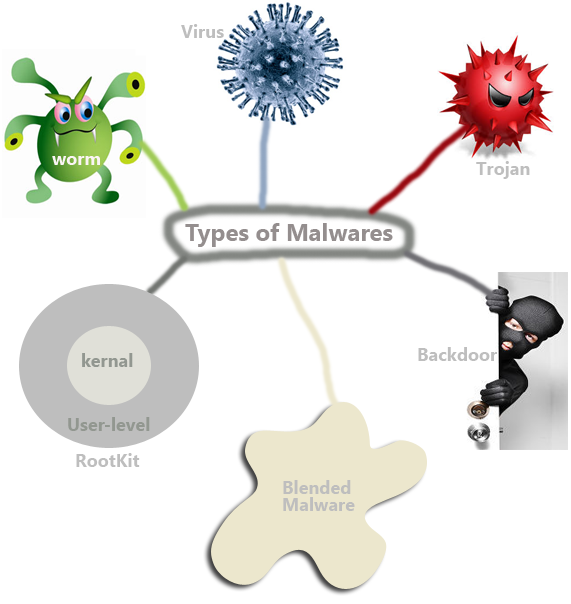
Definition of 7 Types of Malware
Though malware may take many forms, they have only one purpose to -disturb your computing environment. We can broadly classify malware depending on how the replicate and function. Remember that any codes that have evil intentions can be called a malware. That is why a virus, worm or even a backdoor program can be considered as a malware. But there is a distinct difference … [Read more...] about Definition of 7 Types of Malware
Top Antivirus Buying Tips for Home Users
Just like the viruses, antivirus software is also very competitive. There are fierce battle among the premium antivirus makers such as Norton, Kaspersky, McAfee, Trend Micro system, Bit defender and a few more to increase their market share. People easily get caught up when they decide to buy a premium antivirus because they cannot differentiate between two vendors. … [Read more...] about Top Antivirus Buying Tips for Home Users
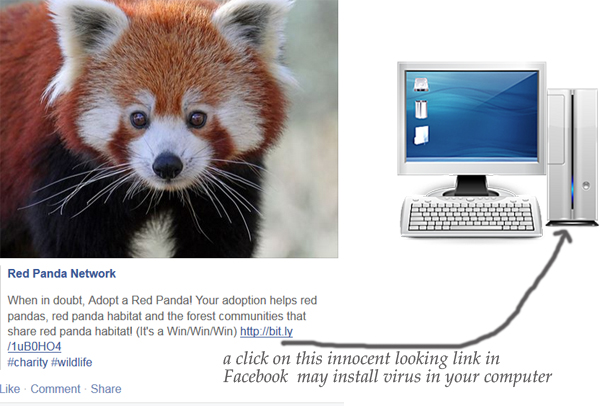
How to Remove Annoying Facebook Virus
What is Facebook virus?Facebook virus is just like any other virus that gets installed in a computer when a user clicks on a link shared from his friends’ news feeds or shares. So, the two most common ways that can infect your computer from Facebook viruses are: … [Read more...] about How to Remove Annoying Facebook Virus
Top 10 PHP Security Tips
This is a list of top 10 PHP secuirty tips that you can follow when developing your PHP based web applications. Restrict access to administrative page Most of the web based software have administrative page that is used to configure and to manage the software. When you install PHP based software, remember to change the script’s default directory name and also remove the … [Read more...] about Top 10 PHP Security Tips
How to Create SSH key login with PuTTY in Windows
Though it is always possible to login in your server using username and password, but you always remain vulnerable to brute force attack. You will always feel that someone may break your password and get privileged access to your server. Are there any better ways to make your server access more secure? The answer is positive. You can make your server access more secure by … [Read more...] about How to Create SSH key login with PuTTY in Windows