By following windows server security best practices, you can ensure that your server is running under the minimum required security settings. Implementing security best practices does not mean that your systems do not have any vulnerability. But, it gives a sense of security that your system will not be easily compromised and it least will perform better when it has to fight … [Read more...] about Top 20 Windows Server Security Hardening Best Practices
Network Security Tips
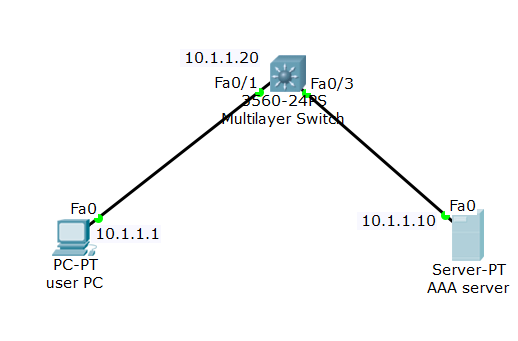
How to Configure AAA (TACACS+) on Packet Tracer for User Authentication
AAA functionality in Cisco switch can be used as a centralized solution to secure and control user access to switches. Cisco switches are capable of implementing AAA functionality with either TACACS+ protocol (Cisco proprietary) or RADIUS protocol. To use AAA you need to enable it and then connect it to an AAA service hosted in a server. … [Read more...] about How to Configure AAA (TACACS+) on Packet Tracer for User Authentication
How to Configure Cisco Private VLANs in 4 Easy Steps
Concept of private VLAN A VLAN allows unrestricted traffic flow among the hosts within the VLAN. When a packet is sent from a host to a destination machine within a VLAN, the switch sends that packet only to the destination host machine, not to every other host in the VLAN. But when a broadcast traffic is sent by a host machine, all other hosts in the VLAN receive the … [Read more...] about How to Configure Cisco Private VLANs in 4 Easy Steps
5 Open-Source Host Based IDS Software to Detect Intrusion
This post is to help you learn about five effective open-source host-based intrusion detection software.The success of a host-based intrusion detection system depends on how you set the rules to monitor your files integrity. So, while configuring you need to remember that if you do not include the directories that you want to protect, the IDS will not detect anyting and a … [Read more...] about 5 Open-Source Host Based IDS Software to Detect Intrusion
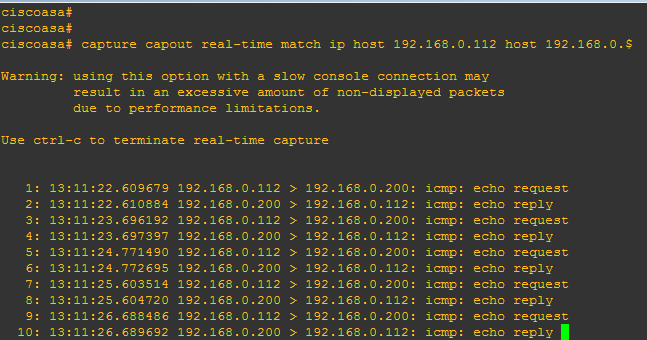
3 Simple Steps to Capture Cisco ASA Traffic with Command Line
Though many network engineers love using ADSM packet capture option, CLI(command line interface) mode is more useful and saves time if you want to customize your traffic capture command. Create a few customized capture commands in a text file and then paste it in the CLI of your ASA . use the following three generic steps: … [Read more...] about 3 Simple Steps to Capture Cisco ASA Traffic with Command Line
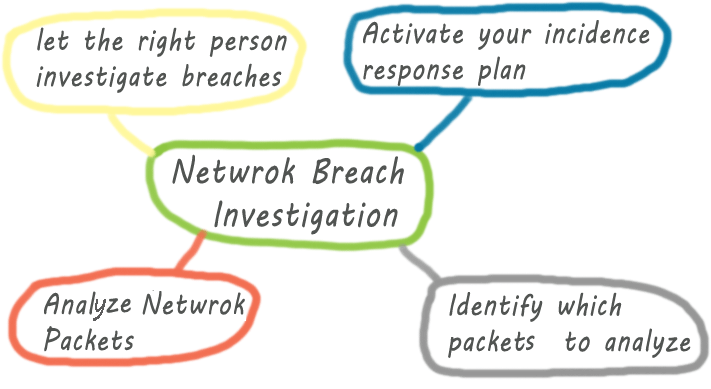
Tips for Network Security Breach Investigation
Investigating network security breach may seem to be a daunting task to someone who has no prior experience of security breach investigation. Like any other IT disciplines, you can handle and investigate network security breach better if you have are well-equipped with the necessary tools and techniques used by the professionals. No matter if you are a network engineer or a … [Read more...] about Tips for Network Security Breach Investigation
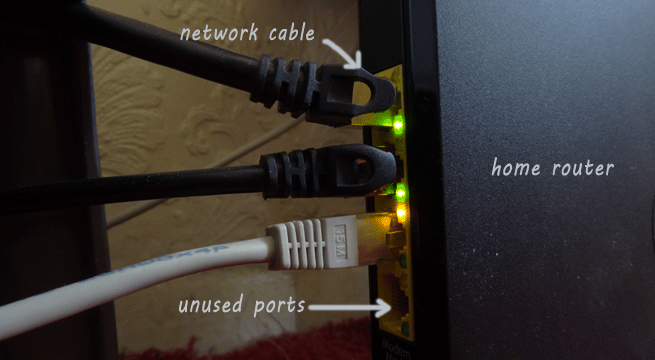
20 Ways to Secure Home Network
Almost every Internet user has their home network that every family member use to Internet access.For your home network security you can follow a few simple steps to eliminate the chances of your network being compromised. Before diving deep into the home network security issues, you may have a look at the vulnerability points in your network, including your client machine. … [Read more...] about 20 Ways to Secure Home Network
Top 15 Network Security Vulnerabilities that System Administrators Must Know
This post aims to help you familiarize with the top 15 commonly known network and system security vulnerablitis. If you are a new administrator, you can have a look at the following list. ACLs on the border router The ACLs you place in your router, especially in the border router, should not allow inadequate access to your other devices connected to your router. A few … [Read more...] about Top 15 Network Security Vulnerabilities that System Administrators Must Know
Top 10 Tips to Prevent Data Exfiltration
What do we mean by data exfiltration? First of all we need to realize that data breach and data exfiltration are two different things. In simple words, data exfiltration means unauthorized transfer of data Your data can be transferred without your knowledge using data exfiltration techniques used by both external and internal actors and tools used by companies. … [Read more...] about Top 10 Tips to Prevent Data Exfiltration
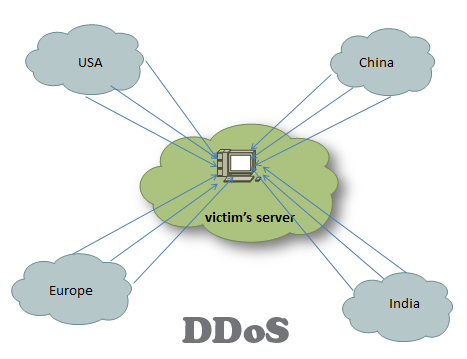
10 Major Types of DDoS Attacks and Prevention
Despite the differences in the mechanism, the purpose of the DDoS (distributed denial of service attack) is the same- to deplete the resources on the victim’s network. DDoS can be broadly divided into two types: bandwidth depletion and resource depletion. This post aims to give you a broad overview of the various types of DDoS attacks and their prevention techniques. … [Read more...] about 10 Major Types of DDoS Attacks and Prevention
15 Ways to Stop DDoS Attacks in your Network
To stop DDoS (distributed denial of service) attack, one needs to have a clear understanding of what happens when an attack takes place. In short, a DDoS attack can be accomplished by exploiting vulnerabilities in the server or by consuming server resources (for example, memory, hard disk, and so forth). … [Read more...] about 15 Ways to Stop DDoS Attacks in your Network
How to Respond to Network Intrusion Detection
When your intrusion detection system triggers an intrusion alarm, you need to respond quickly to minimize the effects of the intrusion. The longer it takes to respond the higher the chances that your system will be damaged severely. If you do not have proper plan and concepts of what you have to do when you detect or suspect an intrusion, you will only panic for nothing and … [Read more...] about How to Respond to Network Intrusion Detection
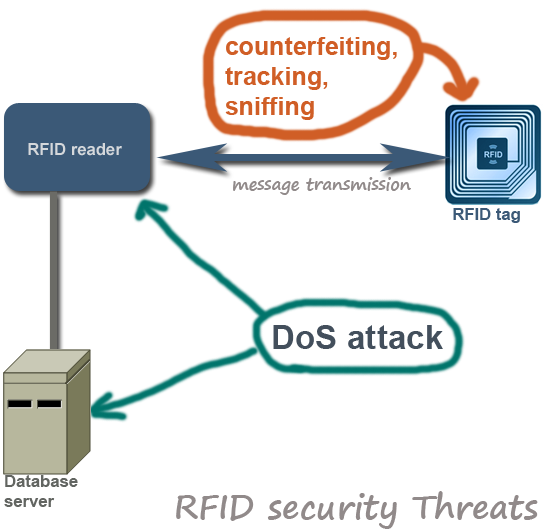
Top 10 RFID Security Concerns and Threats
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues. … [Read more...] about Top 10 RFID Security Concerns and Threats
63 Web Application Security Checklist for IT Security Auditors and Developers
As you know that every web application becomes vulnerable when they are exposed to the Internet. Fortunately, there are a number of best practices and coutner measures that web developers can utilize when they build their apps. This post will list some proven counter measures that enhance web apps security significantly. … [Read more...] about 63 Web Application Security Checklist for IT Security Auditors and Developers
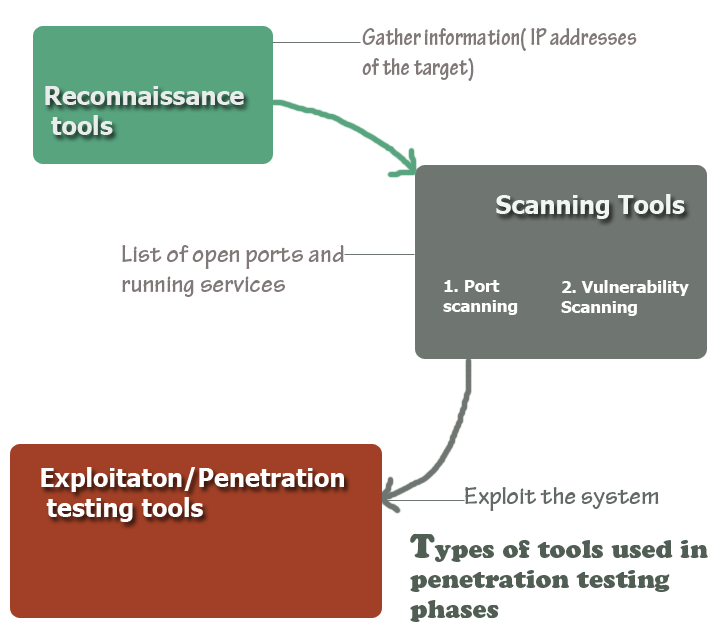
15 Penetration Testing Tools-Open Source
In footprinting or reconnaissance phase, a penetration tester collects as much information as possible about the target machine. The primary purpose of this phase is to gather intelligence so as you can conduct an effective penetration test. At the end of his phase, you are expected to have a list of IP of your target machine that you can scan later on. … [Read more...] about 15 Penetration Testing Tools-Open Source
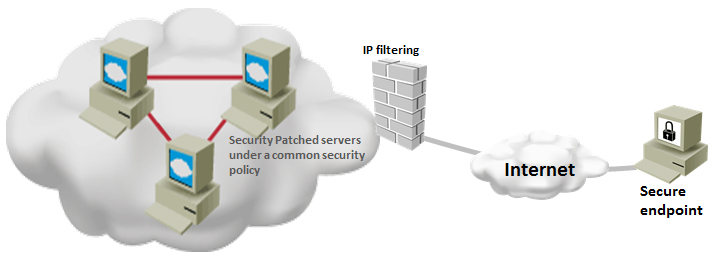
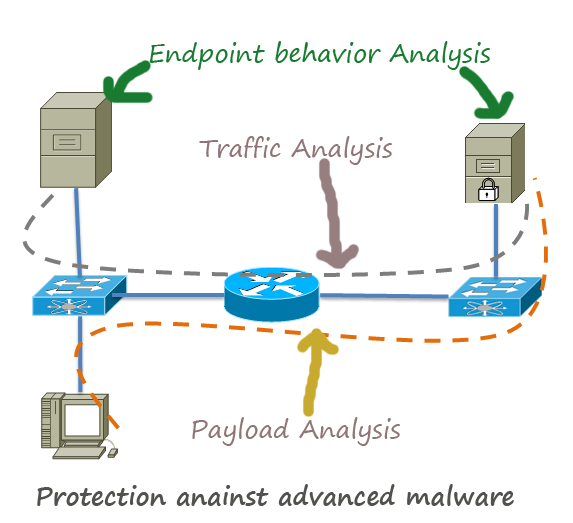
How to Protect Network Against Advanced Malware
Advanced malwares are extremely stealthy and attack targeted protocols and applications. In most cases, the attackers use these malwares to steal sensitive information from the governmental institutes financial institutes, especially the credit card service providers . Major Concerns about Advanced Malware: They are discovered after the attack has been taken place. So, … [Read more...] about How to Protect Network Against Advanced Malware
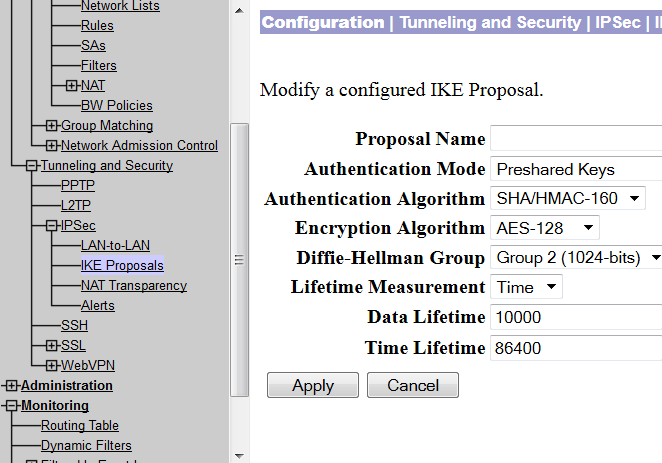
Site to Site VPN Between Cisco VPN Concentrator and Router
At times, it is economical to build a VPN tunnel with the available networking resources. For example, if you have a VPN concentrator and you need to connect a small office securely with your network, you can do so by installing a low priced Cisco router in the remote office. This post will demonstrate how you can build VPN using a VPN concentrator and a Cisco router. … [Read more...] about Site to Site VPN Between Cisco VPN Concentrator and Router
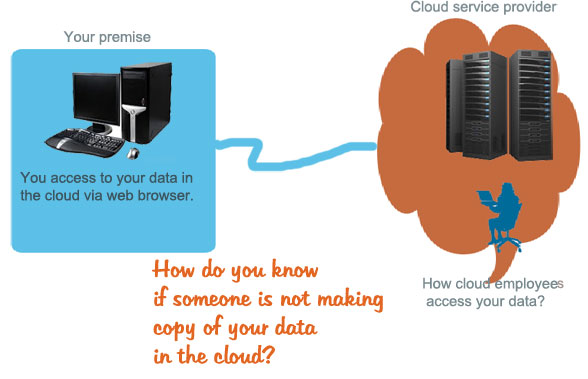
Top 10 Cloud Computing Security Issues
From security perspective, not all types of data of an organization are equally important for successful business operation. Depending on business criticality, some data need to be more secured. The enormous computing power of cloud attracts businesses to put their data in the cloud, but many of the businesses do not have any decisive policy that defines which data to put … [Read more...] about Top 10 Cloud Computing Security Issues
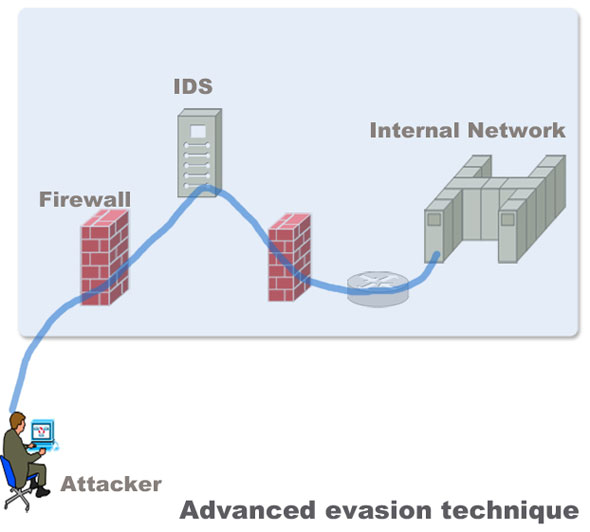
How to Protect Networks against Advanced Evasion Techniques(AET)
Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic. The strings used to evade the devices are not malicious themselves. Their main purpose … [Read more...] about How to Protect Networks against Advanced Evasion Techniques(AET)