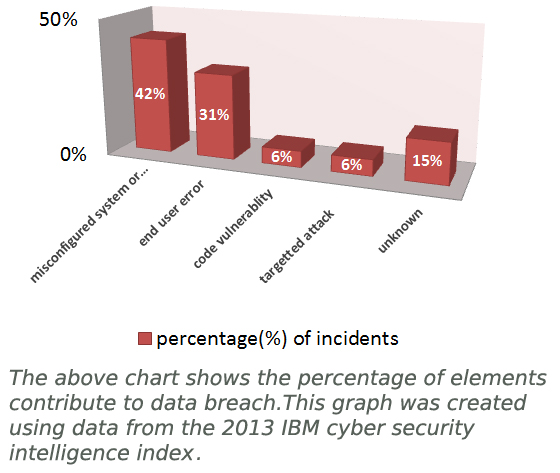
What do we mean by data exfiltration?
First of all we need to realize that data breach and data exfiltration are two different things. In simple words, data exfiltration means unauthorized transfer of data
Your data can be transferred without your knowledge using data exfiltration techniques used by both external and internal actors and tools used by companies.
Who can exfiltrate your data?
In general, there are three types of threat actors motivated by various reasons.
State: your own county or any foreign states can exfiltrate data for espionage, influence and strategic geo political advantages.
Organized criminal groups: they are motivated by financial gains. One of the common targets is credit card industries, banks, e-commerce sites.
Hackers group: hacktivists group like anonymous can exfiltrate data in order to gain social influence.
What are the primary targets of data exfiltrators?
- Database
- Sensitive files in the file server
- Emails and other communictions methods
- Source codes of your custom application
What are the data transport mechanisms used to exfiltrate data?
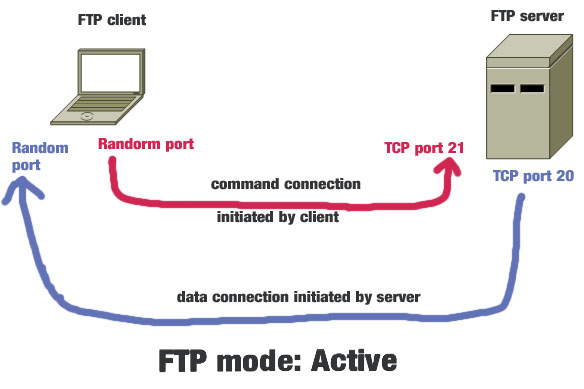
- FTP
- HTTP/HTTPS
- SMTP
- Remote Desktop
- DNS
- VPN
Types of file formats used to transport data?
Microsoft word, excel, PowerPoint, pdf, xml, images, videos and the other file format.
Types of information targeted by perpetrators
In the majority cases, a data exfiltrators will target for your customer and employess’ personal identification information. The second most vulnerable data is the PCI information.
At first data exfiltration will target your data. The next step is to find a way to transport that data. You need to identify the exit path of your data from your organization. Do you allow your employees to carry USB drives in your organization? What about https/ssl, ftp and other method of remote data transfer facility.Keep in mind that lots of data can be transferred via email in word files or plain text files or csv files.
Before transferring your data via FTP the attacker can encrypt and compress your data in order to avoid detection system.
What can you do to stop data exfiltration?
- At first identify your data sources.
- Determine data flows.
- Identify regulatory requirements
- Classify your data according to sensitivity
- Assign data owner
- Apply protection
- Review that who has access to the important data
- Program review
Make a simple plan to prevent exfiltration
When you make a data protection plan, you need to develop a clear understanding of the location of your data and how they exists( encrypted or unencrypted) and find out the strength of your data access control mechanism and management system.
Once you make a list of your critical data, you need to realize the business impact of data breach and to identity the parties who are interested in your data. Most important of all is to have a clean understanding of what exfiltration technique can be used to move data from your organization. You do not need to be a data breach expert in order to protect your data, start with a small step at first and that is classify your data. The next step is to assess the existing controls.
Our Top 10 Tips are:
- Classify your data based on business criticality.
- Make of list of impacts of data breach
- Identity the people who may need your data to get competitive advantage
- Run an Assessment on your data access control mechanism.
- Identity the list physical and logical access (FTP, SSH, VPN etc.) route that can be used to exfiltrate your data.
- Identify how data resides in your systems( encrypted or unencrypted)
- Identify the file formats of your data and how you can protect
- Assess the data owner’s and data manager’s accountability. Don’t neglect the fact that you are more vulnerable to the insiders.
- Run regular (monthly or quarterly) review on your data protection plan and modify your plan if you need to depending on the situation and technological changes.
- Increase data program awareness in your organization.