Advanced malwares are extremely stealthy and attack targeted protocols and applications. In most cases, the attackers use these malwares to steal sensitive information from the governmental institutes financial institutes, especially the credit card service providers .
Major Concerns about Advanced Malware:
They are discovered after the attack has been taken place. So, you do not have a clue what is going on with your sensitive data unless you detect the presence of advanced malware in your system. When you are planning against advanced malware your primary target should be detect it as soon as possible. By using Garter’s 5 styles of advanced defence framework, you can apply the following five defence mechanism in your network:
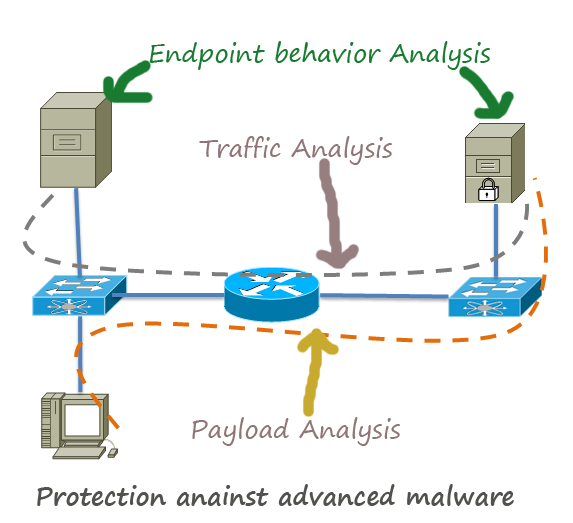
Traffic Analysis
Under normal circumstances, your network follows a specific traffic pattern which you can easily recognize when you analyse your traffic for a month or so. When you discover any unusual traffic signature, you can investigate the root cause of this pattern. For example, anomalous DNS traffic in a network is a good indicator of botnet activity. So, be familiar with the traffic pattern and flow of your network.
Tools: You can use any traffic capturing tool or even content capturing tool to analysis your network
Network Forensic
They capture full packets and store the traffic, which later can be analysed and generate report to find the existence of advance malware. Unlike any packet capture tools, network forensic tools can extract and retain metadata.
Payload Analysis
Payload can be considered as the cargo of data. In a packet, payload is the actual data that has real meaning to the end users. By analysing payload of normal traffic, you can create a profile of your network’s data. If anything does not match your normal payload can be investigated to detect malicious activity. Unfortunately, payload analysis cannot track the endpoint behaviour for a period of time after discovering a network compromise. To track post-compromise activity, you need to use endpoint forensic analysis.
Endpoint Behaviour Analysis
You can analyse your endpoints behaviour with more than one approach. One approach is the containment of the application. As you know that containment means restricting the something in order to curb its ability to do harm. The suspicious application is isolated from the other applications and kept in a virtual container. Thus it reduces the chances of spreading the malware in the network. Another approach used to analyse the endpoint behaviour is to monitor the system memory, configuration, processes and to use techniques to respond to any real-time threat events.
Endpoint Forensic Analysis
Normally, the incident response team uses endpoint forensic analysis as a tool to collect data from the computer for suspicious activities. This technique helps to specifically identify the compromised computer and to detect the behaviour of the malware program.
Depending on the size and sensitivity of your data you can implement any or all of the mentioned framework in your network. Unless you have significant number of IT security professionals in your organization, you may not be able to use all of the techniqes. For this reason you need to figure which framework or combination of framework works best for your network.
Always remember that there is no magic bullet to protect a network and no single defence mechanism and products has the ability to defend against all types of advanced malware attack. When you implement a malware defence framework, pay attention to educate your IT professionals and the end users about the common symptoms of a comprised network and systems. Besides, never underestimate the power of continuous monitoring. A person dedicated to monitoring may not find anything in months but when he will identify an early attack signature, you will save both reputation and money of your organization. So, do not always think about money when you need a dedicated network security monitoring team for your network.