Though many network engineers love using ADSM packet capture option, CLI(command line interface) mode is more useful and saves time if you want to customize your traffic capture command. Create a few customized capture commands in a text file and then paste it in the CLI of your ASA . use the following three generic steps:
- Create a capture command
- Use the show capture command or real time capture command
- Use ‘no capture’ command to stop it.
In the global configuration mode, type the following to start capturing traffic:
# capture capout interface outside match ip 192.168.0.112 255.25.255.255 any
The above command will capture traffic from any host to the outside interface. Similarly, you can capture traffic sent to the inside interface. Just replace the name outside by inside or any other name of your interface traffic that you want to capture.
To capture traffic from a specific host such as 192.168.0.112 use the following command
#capture capout interface outside match ip 192.168.0.112 255.255.255.255 host 192.168.0.200
Or
# capture capout interface outside match ip host 192.168.0.112 host 192.168.0.200
ASA Real time traffic Capture Commands
#capture capout real-time match ip host 192.168.0.112 any
To capture real time traffic sent from a specific host:
#capture capout real-time match ip host 192.168.0.112 host 192.168.0.200
Note: capout is a name used to label the traffic.
To see the captured traffic, use the command given below
#show capture name_of_capture
#show capture capout
To clear captures:
#clear capture name_of_capture
#clear capture capout
How to stop the capture
“no capture name_of_capture” is used to stop the capture. Never forget to stop the capture when you are done with the capture; otherwise, your firewall will keep capturing the traffic.
Here is an example of how to stop capture.
#no capture capout interface inside
#no capture capout interface outside
How to capture Ethernet traffic
#capture arp1 ethernet-type arp interface outside
Note: here, arp1 is just a name to label the capture traffic. You can write any name of your choice to label your captured traffic.
To see the captured traffic use the following command:
# show capture arp1
Note: all the capture command need to be typed in the global configuration mode.
How to captured Cisco ASA traffic in real time
To see the real time traffic you need to use the following command
#capture capture_name interface outside real-time
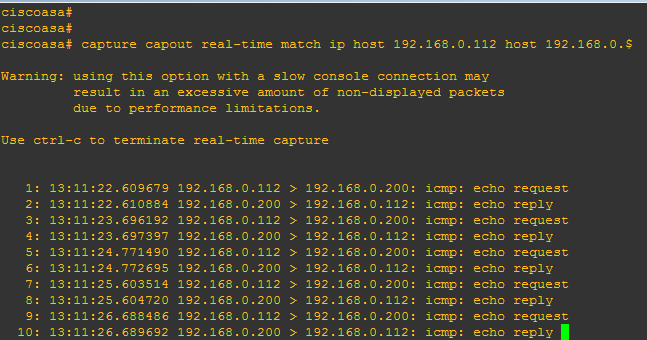
For example, you want to see real-time IP traffic sent from a host 192.168.0.112 to the outside interface of your ASA firewall. The IP address of the outside interface of ASA is 192.168.0.200. Type the following command to see real time traffic from a specific host(192.168.0.112)
ciscoasa# capture capout real-time match ip host 192.168.0.112 host 192.168.0.200
To terminate real time traffic capture press ‘CRTL+C’.
To clear the buffer for all captured traffic, use the following command:
#clear capture capture_name ( replace the capture_name with the name that you used to label the traffic)
To clear the buffer from all captures, use the following command.
# clear capture /all