How to Configure VPN in Cisco Routers
Virtual private network can be configured with most of the Cisco routers( 800 to 7500 series) with IOS version 12 or higher.VPN can be implemented in a number of ways–with various level of security measures and configuration. To determine the right VPN configuration for your network, you need to have a solid understanding in cryptographic system and encryption algorithm.Besides, one needs to know which type of VPN is suitable for remote clients and which type of VPN is used to create secure site-to-site connection. This article explains the necessary steps with configuration script to setup VPN in Cisco routers. This configuration can be simulated in Cisco packet tracer software as well.
Types of VPN
- Remote access VPN
- Site to site VPN
- Business partner vpn
VPN implementation methods
The two methods that can be used to implement any of the above mentioned three types of VPN are:
- IPsec based VPN
- SSL based VPN
Both types of VPN implementation method has its advantage and disadvantages. If you choose to implement an IPsec based VPN, you need to install client software on every remote host or devices that need to access the VPN. On the other hand, SSL VPNs can directly establish connection between two machines without the need of installing any client software; it is possible because SSL basically a web browser based VPN solution. Most of the site-to-site and business partner types VPNs are IPsec based, whereas SSL is widely used for remote client access VPNs
IPsec VPN
The main purpose of IPsec is to provide communication security while your data pass through the public network such as Internet. To establish IPsec connection, you need to have IPsec compliant devices such as Cisco IOS based routers. The following cryptographic technology is used with IPsec
- Diffie-Hellman key exchange
- Public key cryptography
- Data encryption algorithm-it helps to validate the identity of the sender and
- Hashing algorithm– it verifies authenticity and intergrity of data. Hash algorithms used are HMAC,SHA-1,MD5
- Digital certificate– a way to validate the identity of the sender. Digital certificate contains the identity details of a public key holder and it is issued by a CA.
VPN Design Process
When you decide to set up a VPN, you need to design a VPN implementation plan. The VPN implementation plan needs to consider the following aspects.
1. Identify the type of VPN (SSL or IPsec) you need to implement and what the computer systems or network equipments need to be protected by VPN connection.
2. Design VPN-choose the type of authentication methods, filtering and cryptographic policy
3. Testing- it is better to try to test your design in a test environment before you deploy the VPN in your organization.
4. Deployment-once you are satisfied with the test result, you can start deploying your VPN as per your design
5. Monitoring- monitor the traffic activity at the VPN end points and always check out the security warnings or updates with your VPN equipment vendors.
IPsec Protocols
IPsec protocol is basically a combination of two different protocols with two different purposes. These two protocols are collection of security protocols are: packet protocols and service protocols. There are two major packet protocols: ESP (encapsulating security payload) and Authentication Header (AH).The service protocol of IPsec is known as IKE-Internet Key Exchange.
ESP-its encrypts entire IP data portion of the packets and adds ESP header and trailer at the end of the packet.ESP provides confidentiality, authentication and integrity to a data packet.
AH– authentication header adds to the IP packet to provide the data packet validation.AH does not offer any encryption service, unlike ESP.
IKE-it uses Diffie Hellman key exchange process to offer key management and security association.
So, as you see that IPsec mainly provides two type of service – packet authentication and encryption- by using ESP and AH. IPsec can provide these two services in two modes- tunnel modes and transport mode. Tunnel mode provides the encryption and authentication for the entire data packet, where as transport mode provides only the transport layer data security and authentication. Thus transport mode IPsec generates lower overhead and is faster than tunnel mode IPsec. The disadvantage of transport mode IPsec is the any attacker may perform traffic analysis of this packet since the header information is not encrypted.
Now, you understand the basics of IPsec and let’s see how we can implement IPsec based VPN in a Cisco router.
This configuration is for a site to site type VPN, where all traffic from router A to router B will be encrypted with IPsec.
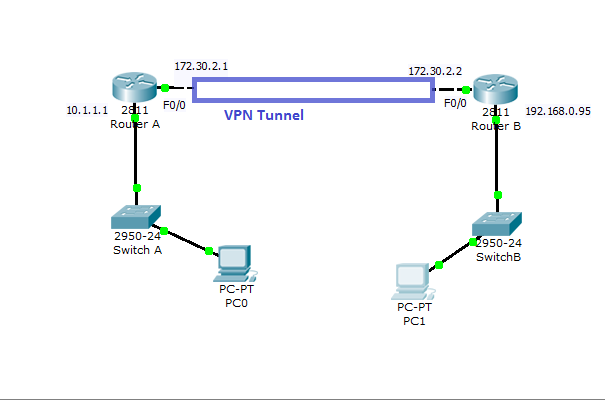
Configuration on Router A
RouterA#configure terminal
RouterA(config)#crypto isakmp policy 1
RouterA(config-isakmp)#authentication pre-share
RouterA(config-isakmp)#encryption aes 128
RouterA(config-isakmp)#group 2
RouterA(config-isakmp)#exit
RouterA(config)#lifetime 96400
RouterA(config)#end
RouterA#copy run start
Now create a transform set name and give it a name as you like.For example, name the set as ciscoset
RourterA#conf term
RouterA(config)#crypto ipsec transform-set ciscoset esp-aes esp-sha-hmac
RouterA(cft-crypto-trans)#exit
RouterA(config)#access-list 101 permit ip 10.1.1.0 0.0.0.255 192.168.0.0 0.0.0.255
RouterA(config)#crypto map router1torouter2 10 ipsec-isakmp
RouterA(config-crypto-map)#set peer 172.30.2.2
RouterA(config-crypto-map)#match address 101
RouterA(config-crypto-map)#set transform-set ciscoset
RouterA(config-crypto-map)#exit
Next, you have to apply the crypto map to the external interface of router A
RouterA(config)#interface fastethernet0/0
RouterA(config-if)#crypto map route1torouter2
RouterA(config-if)#end
RouterA(config)#ip route 192.168.0.0 255.255.255.0 172.30.2.2
RouterA(config-if)#end
Now, you can configure the router B with similar configuration just by changing the peer IP, IP router and access list IP with for router A.
