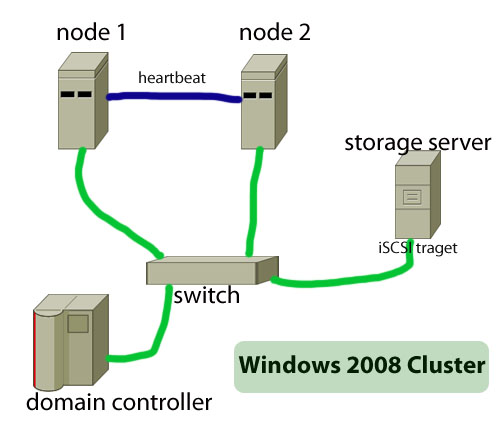
The main objective of a failover cluster is to ensure high availability of services. A failover cluster means that only one server--which is also known as active server--in the cluster will provide the service such as a file server or webserver. When this active server will go offline or will be out of service, another server in the cluster will provide the same service, … [Read more...] about How to Build Failover Cluster in Windows Server 2008
How to Pass CISA at the First Attempt?
Unlike most other vendor certification exams., CISA (certified information system auditor) is a paper-based test. Though, ISACA never publish any data about the passing rate of this exam., it is pretty easy-to-guess from available data in the Internet that you need to prepare systematically and carefully to pass this highly respected IT auditing exam. … [Read more...] about How to Pass CISA at the First Attempt?
Yahoo Mail Security Settings:How to Protect Your Account
To secure your Yahoo mail account you need to block the doors that are easy for anyone to get access to your account. This post will help you to modify your account settings to make your mailbox safer than ever. If you are a Yahoo mail user, then you are advised to use the following settings: Create a sign-in seal How to change password Monitor your account … [Read more...] about Yahoo Mail Security Settings:How to Protect Your Account
How Do I Know If My Computer Has Been Hacked?
If you know some simple and easy-to-use methods to check that if your computer has been hacked you can confidently work online or visit any site without much worrying about your data privacy. The good news is that there are some simple ways to check that if your system has been hacked, which works well in most of the cases.At first you need to know the ways that can be used to … [Read more...] about How Do I Know If My Computer Has Been Hacked?
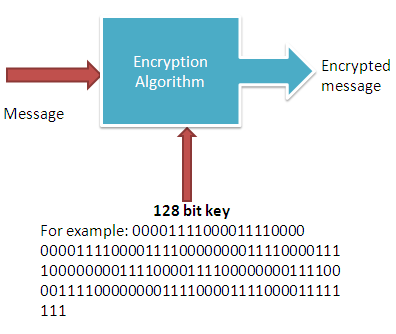
What is 128 Bit Encryption?Why the Length is Important?
The purpose of any cryptography is to ensure the confidentiality, authenticity, non-repudiation and integrity of the data. And all these goals are achieved with the use of cryptography keys. The 128 bit key is such a type of key that ensure all the intended objectives of using a crypto-system or cryptographic algorithm.it is the key which needs to be secret in order to keep … [Read more...] about What is 128 Bit Encryption?Why the Length is Important?
What is VPN and How it Works?
By reading this post you can learn about VPN and its workings. VPN is just a term we use to describe a system which makes communication between two computers, regardless of how far they are, within a secure channel. Here the secure channel means you can convert the public network secure. As you know that a public network is nothing but the Internet, where can have access to any … [Read more...] about What is VPN and How it Works?
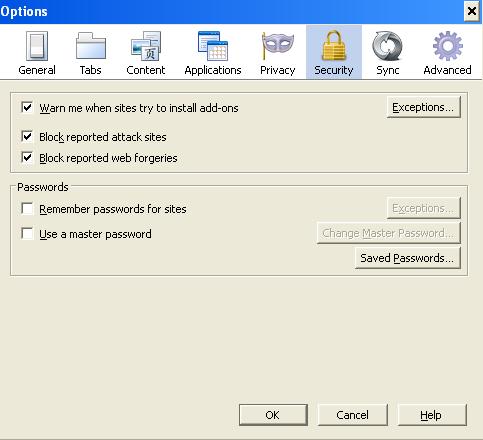
Firefox Security Settings and Features
There are certain security issues that would help you keep your browsing experience smooth and safe with Firefox.As you know that web browser work as a middle man between you and the webpages. When you request for a webpage from your computer by typing a web address (URL), all the underline works such as grabbing the pages and displaying it to you in human readable format is … [Read more...] about Firefox Security Settings and Features
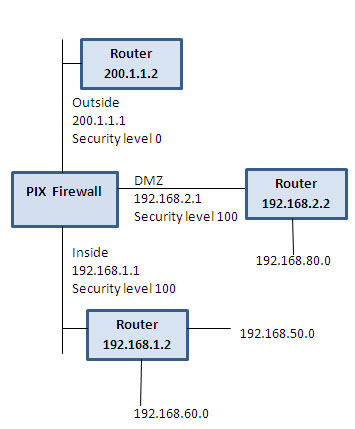
PIX Firewall Configuration Basics
This post intends to familiarize you with some of the basics skills that you need to configure a PIX firewall. The configuration commands will help you to assign name to a PIX interface to configure routing and to configure network address translation including PAT(port address translation). To erase configuration: write erase To save configuration: write terminal … [Read more...] about PIX Firewall Configuration Basics
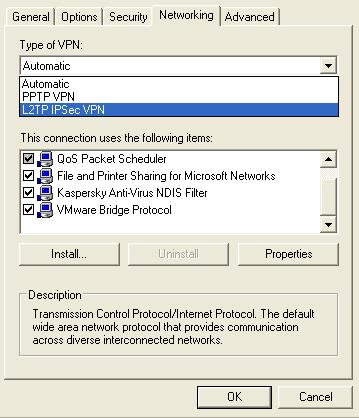
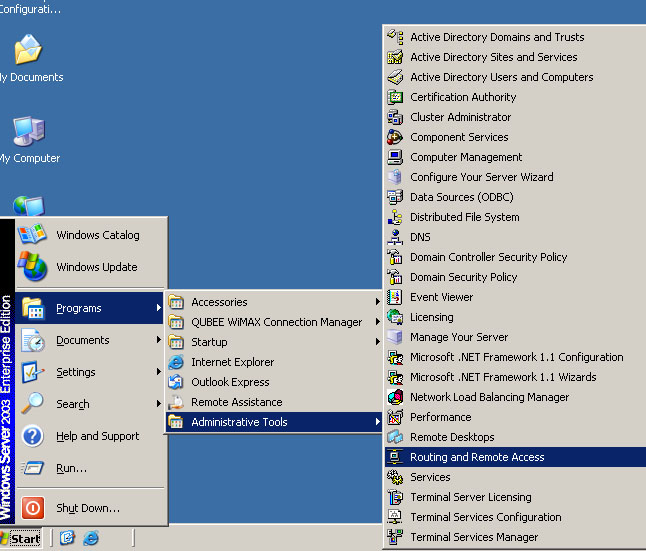
How to Configure VPN,RAS and IPSec Policy in Windows Server
VPN is a trusted and secure network, which use tunneling and protocol(PPTP,L2TPIPSec) to make data transmission through the public network. RAS: remote access service used to access server remotely from client terminal using dial-up connection. IAS:Internet authentication service is used to remotely and centrally manage all RAS server and keep remote access policy … [Read more...] about How to Configure VPN,RAS and IPSec Policy in Windows Server
Windows DNS Server Configuration
DNS or domain name system is one of the most important parts of client-server model. Without a DNS no client could be part of a domain and there will be no way you can convert domain name into the IP address of the server. In this post you will find basic procedures that you can use to configure DNS for your domain controller. Though the procedures described in this post is … [Read more...] about Windows DNS Server Configuration
Exchange Server 2003 Tutorial
Exchange server 2003 installation process: Before installing exchange server on windows server you need to have installed the following Windows components: ASP.NET IIS SMTP NNTP WWW To install the above mentioned components you need to insert your Windows server CD in your CD or DVD drive and then select those components from the add remove components … [Read more...] about Exchange Server 2003 Tutorial