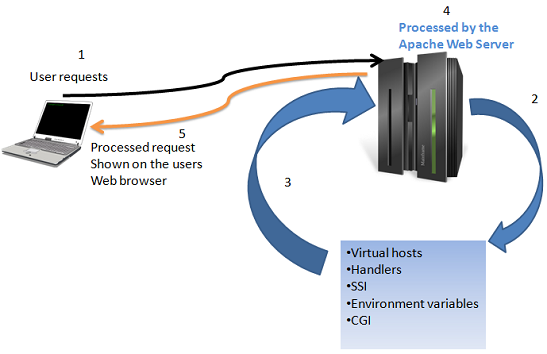
Apache is one of the prevalent web servers because of its expandability with features, support community and cost. If you consider using Apache as a solution to your web server and want to implement the most basic security requirements, then you need to have clear understanding of some of the most ubiquitous features of Apache and those features are:
- Virtual hosts
- Server side includes or SSI
- Dynamic content with CGI
- Handlers
- Environmental variables
- URL mapping
Virtual host
This feature of Apache has made possible to host thousands of web sites in a single server. In a shared hosting environment, Apache serve up Webpages via virtual host with the help of two mechanisms:
- Name based mechanism
- IP based mechanism
In name based mechanism, all the websites in as single server use the same IP address. When a user type the domain name of a site in his web browser and the web server finds the specific domain name base on the CNAME in the DNS. A CNAME makes a physical machine or server with an IP address to be known to the others with a range of hostname, not a single domain name. Web hosting companies creates CNAME in their DNS servers, which means that a number of domains will be directed towards a single IP address of the server that is working as virtual hosts for all the hosted sites.
In name based mechanism you cannot enter a site’s name with its server IP address since all the sites are sharing the same IP. In the server level all the site are recognized by the combination of an IP and a part number.
To check if a site is being hosting in a name based mechanism you can use the reverse IP look up sites in the Internet.
IP based virtual hosting: in this type of hosting each website residing in the server has its unique IP address. To accommodate each site an IP, the server needs to create IP aliases. Each IP address should have a distinct DNS record in the DNS. Like the name based mechanism, they will not have the CNAME. Using Apache’s virtual host and httpd.conf file, each IP must be mapped with its web server.
The main problem with virtual hosting is that if one site is compromised in a server then all other sites on that server can also be compromised.
Server side includes (SSI)
Generally, SSI is used for generating dynamic content or pages on a website. By default, they remain disabled in Apache server. In case you are running SSI for your site, you need to keep the “exec cmd” directive disabled, which you can do with the options directive in the httpd.conf file. SSI has file extension of .shtml, .shtm, .stm and the signature mark of their opening statement is ( <!–>) and the ending statement with ( — >).
CGI (common gateway interface)
CGI is basically a set of guidelines which helps to create server-side scripting in order to generate dynamic contents. You can create a CGI program with the help of C/C++ , Perl, Java, sh, csh, ksh, visual basic. Since Apache depends on various languages to implement server-side scripting, the vulnerabilities of that language need to be realized fully to implement any CGI in a web server.
Handlers
The handlers are a server-side mechanism that tells the server about which action to take on specific files such as .JSP, .ASP and so on. A handler allows a web developer to map the service required by a non-standard file name. In order to specify a specific file extension to be handled by a particular script or CGI, you need to add a handler to your httpd.conf with an action directive. For instance, you want to handle you .ASP file with a particular script, you would need to add the following handlers in your httpd.conf file.
AddHandler file-type .ASP
Action file-type /cgi-bin/ASP.pl
Environmental variables
They are basically the channels to maintain the communication between the web servers and the CGI programs. The main purpose of environmental variable is to collect the web servers’ information. Some examples of environmental variables are: SERVER_NAME, SERVER_SOFTWARE, SERVER_PORT, REMOTE_ADDR etc. as you can see that these variables has all the potential to open up a number of vulnerabilities to the attacker, you need to be care while choose your environmental variables.
