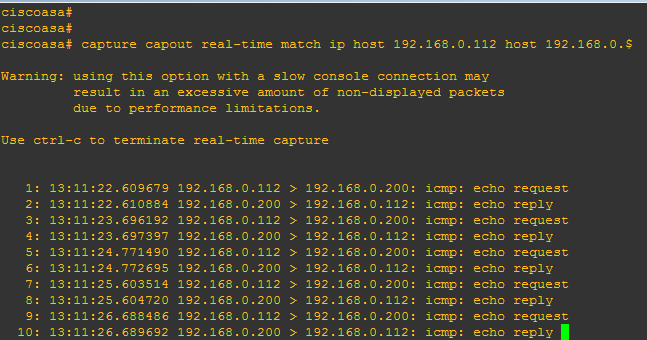
Though many network engineers love using ADSM packet capture option, CLI(command line interface) mode is more useful and saves time if you want to customize your traffic capture command. Create a few customized capture commands in a text file and then paste it in the CLI of your ASA . use the following three generic steps: … [Read more...] about 3 Simple Steps to Capture Cisco ASA Traffic with Command Line
9 Advantages and Disadvantages of Cloud Computing for Business
Deciding to move on to a cloud means moving your data into somebody’s computers. To develop your computing facilities without investing in hardware and infrastructure is what cloud computing all about. In an organization, you may be the decision maker thanking about whether to put your data in a third party cloud or in your own cloud. You can have a look at the following … [Read more...] about 9 Advantages and Disadvantages of Cloud Computing for Business
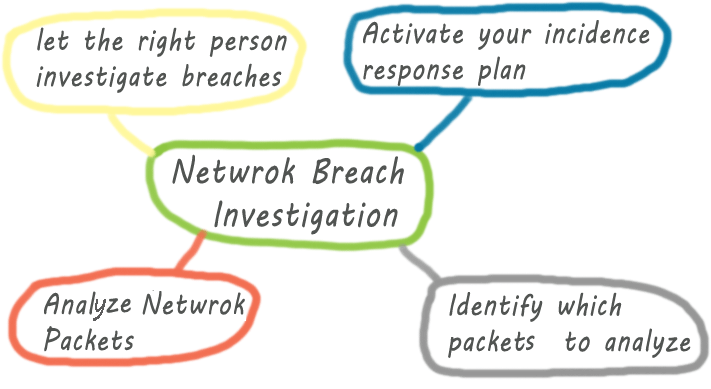
Tips for Network Security Breach Investigation
Investigating network security breach may seem to be a daunting task to someone who has no prior experience of security breach investigation. Like any other IT disciplines, you can handle and investigate network security breach better if you have are well-equipped with the necessary tools and techniques used by the professionals. No matter if you are a network engineer or a … [Read more...] about Tips for Network Security Breach Investigation
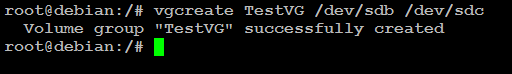
How to Extend Linux LVM by Adding a New Hard Disk
You may need to add new disk to your Linux LVM for various reasons such as for adding capacity for your existing applications or new applications. This post aims to show you how you can add a new disk to your existing LVM as well as to a new LVM. The difference between adding a new disk to a new LVM and to an existing LVM is that in the latter case you do not have to create a … [Read more...] about How to Extend Linux LVM by Adding a New Hard Disk
How to Renew Self-Signed SSL Certificate with OpenSSL Tool in Linux
OpenSSL is a free and open-source SSL solution that anyone can use for personal and commercial purposes. Although it is free, certificates created with it can expire, and you may need to renew them. This post will show you how to renew a self-signed certificate using the OpenSSL tool on a Linux server. If you are looking into creating a new self-signed certificate instead of … [Read more...] about How to Renew Self-Signed SSL Certificate with OpenSSL Tool in Linux
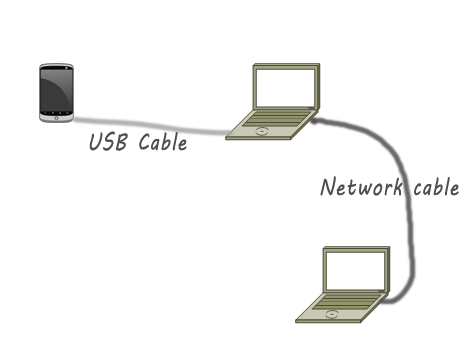
How to Share Internet Connection using Android Mobile Tethering
This post aims to help learn how to connect an android mobile to laptop for sharing Internet connection. For USB tethering, you must need to your mobile’s USB cable to connect to the computer or can use wireless connection. … [Read more...] about How to Share Internet Connection using Android Mobile Tethering
20 Ways to Secure Home Network
Almost every Internet user has their home network that every family member use to Internet access.For your home network security you can follow a few simple steps to eliminate the chances of your network being compromised. Before diving deep into the home network security issues, you may have a look at the vulnerability points in your network, including your client machine. … [Read more...] about 20 Ways to Secure Home Network
Effective Ways to Prevent Cross Site Scripting(XSS) Attacks
Not every developers pay equal importance to web security and vulnerabilities, especially about cross site scripting when they start coding. Their primary goal is to get the project finished Websites developed with unsecure coding can be easily exploited by the attackers. There is no way your browser will prevent XSS automatically unless you disable your browser’s ability to … [Read more...] about Effective Ways to Prevent Cross Site Scripting(XSS) Attacks
Top 15 Network Security Vulnerabilities that System Administrators Must Know
This post aims to help you familiarize with the top 15 commonly known network and system security vulnerablitis. If you are a new administrator, you can have a look at the following list. ACLs on the border router The ACLs you place in your router, especially in the border router, should not allow inadequate access to your other devices connected to your router. A few … [Read more...] about Top 15 Network Security Vulnerabilities that System Administrators Must Know
Top 10 Tips to Prevent Data Exfiltration
What do we mean by data exfiltration? First of all we need to realize that data breach and data exfiltration are two different things. In simple words, data exfiltration means unauthorized transfer of data Your data can be transferred without your knowledge using data exfiltration techniques used by both external and internal actors and tools used by companies. … [Read more...] about Top 10 Tips to Prevent Data Exfiltration
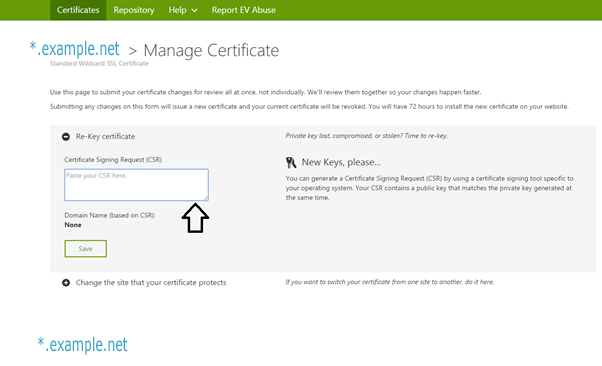
How to install a new Godaddy SSL Wildcard Certificate
This post has been intended for the first time users who want to install GoDaddy SSL certificate in their website. The procedures described here should work well with Apache server and with Nginx. Steps to take before installing GoDaddy SSL To install a digital certificate, you must first generate and submit a Certificate Signing Request (CSR) to the Certification … [Read more...] about How to install a new Godaddy SSL Wildcard Certificate