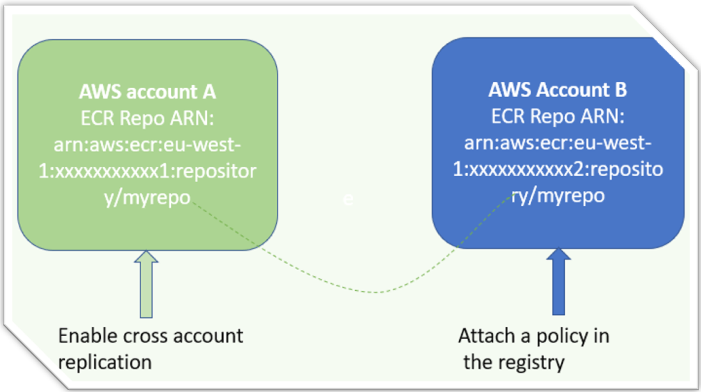
Docker image hosted in ECR in a AWS account can be replicated into another AWS account by enabling the cross account replication setup. For example, you host a docker image in AWS account A and you have a ECS cluster where you need to deploy the docker image. … [Read more...] about How to Enable AWS Cross Account ECR Image Replication
How to Permanently Auto-Mount EFF Volume to EC2 instance using User-Data
Amazon elastic file system( EFS) can be mounted automatically using user-data while spinning up the Instance. This post aims to show both auto and manual mount of EFS volume. Before you start mounting the EFS volume, make sure that you have the EFS ID with you and the EFS security group is open on port 2049 for the EC2 IP or subnets. … [Read more...] about How to Permanently Auto-Mount EFF Volume to EC2 instance using User-Data
3 Steps to setup SSH remote Access to EC2 from Cloud9
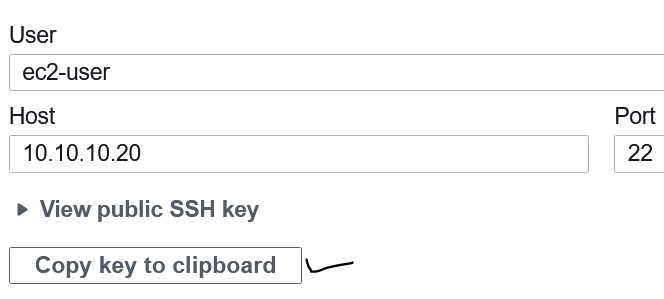
When you need to connect securely to an already running EC2 instance via SSH from a Cloud9, you need to prepare the instance for Cloud9. AWS Cloud9 generate a SSH public key to connect securely to your EC2 server. To start a secure connection from Cloud9 via SSH you need to setp the the SSH key, generated by Cloud9, to EC2. … [Read more...] about 3 Steps to setup SSH remote Access to EC2 from Cloud9
3 Steps to Setup EC2 EBS Volume Disk Space Monitoring using Cloudwatch
The default monitoring of Amazon EC2 does not track the EBS disk space. To monitor disk space in EC2 instance, you need can either manually installed Cloudwatch Agent or can use SSM to install the agent. After installing you Step 1. Instal cloudwatch agent sudo yum -y install amazon-cloudwatch-agent Step 2. create a config.json file in the following … [Read more...] about 3 Steps to Setup EC2 EBS Volume Disk Space Monitoring using Cloudwatch
3 Easy Steps to Create and Deploy AWS SAM Template
AWS SAM template is an abstraction layer, runs on the top of CloudFormation, for creating serverless resources. So, when you run a SAM template to create a Lambda function or an API gateway, it generates a CloudFormation stack behind the scene. The main purpose is ease-of-management of serverless resources in AWS. SAM Vs. CloudFormation: when to use AWS SAM instead of … [Read more...] about 3 Easy Steps to Create and Deploy AWS SAM Template
How to Create a Helm Chart in Windows for Minikube
Helm package manager is used to deploy applications in the Kubernetes cluster. By packaging your app using helm allows to deploy it with one command instead of using “kubectl create/apply” command. Another benefit of using helm is that you can easily upgrade and rollback your apps when required because helm uses version control. Follow the three simple steps creating … [Read more...] about How to Create a Helm Chart in Windows for Minikube
5 Steps to Setup a Nexus3 repository using Docker on Virtual Box.
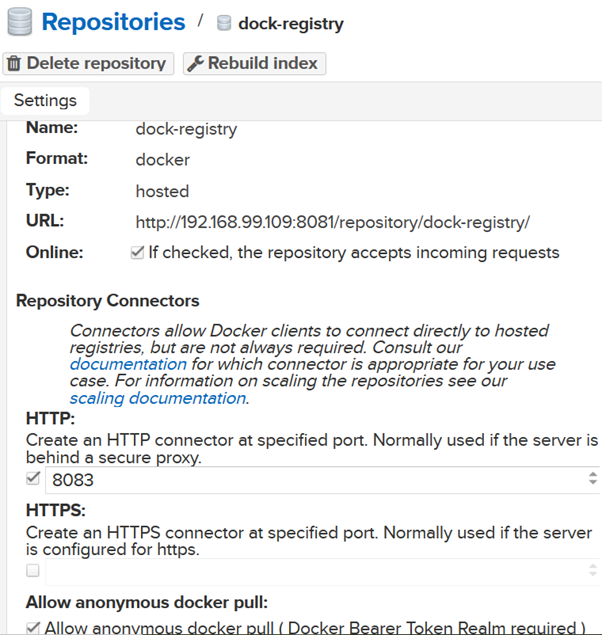
Scenario: To create a private docker repository in your local machine for development purpose, you can deploy a Nexus3 docker image with a persistent volume in a minute. You can either install the docker in your host machine or you can install a Ubuntu virtual box and then install docker on it. Step1: At first create Ubuntu virtual machine and then install docker. Next, pull … [Read more...] about 5 Steps to Setup a Nexus3 repository using Docker on Virtual Box.
9 Types of Digital Security Risks
Having an overall understanding of the existing digital security risk can help to design a decisive risk mitigation plan. Both small and large businesses are exposed to similar types of digital risk, which can cause serious damage to businesses unless handled carefully. The list below explains the nine types of digital risks you need to stay alert of. 1. Data risk- as you … [Read more...] about 9 Types of Digital Security Risks
5 Steps to Auto-Create Helm Charts and upload to S3 Using Jenkins
After packaging the helm charts, you need to store it in a repository so that it can be easily deployed using helm in the Kubernetes or Minikube. This post aims to show you how to set up the AWS S3 bucket as a Helm chart repository. Using the steps below you will be able to setup Helm S3 repo for both Minikube and KOPs created cluster hosted in AWS. Scenario: we will create … [Read more...] about 5 Steps to Auto-Create Helm Charts and upload to S3 Using Jenkins
3 Steps to Install Kubectl, Helm 3 and S3 Plugin in Ubuntu to Store Charts in S3 Bucket
This post aims to show you how to install Kubectl, Helm 3 and S3 plugin so that you can easily store the chart in a S3 bucket form your Ubuntu machine. Though I always use an automated approach to create and store the helm chart, I had to create a helm chart in Ubuntu in order to identify and Helm S3 plugin compatibility issue. 1. Install kubectl To install kubectl in … [Read more...] about 3 Steps to Install Kubectl, Helm 3 and S3 Plugin in Ubuntu to Store Charts in S3 Bucket
3 Steps to Install Minikube on Windows 10
Minikube helps to create the Kubernetes environment on a personal computer. This post aims to show you a few simple steps to install Minikube on Windows Machine. Before installing minikube, make sure you have installed kubectl. Step 1: Install kubectl Go to https://kubernetes.io/docs/tasks/tools/install-kubectl/#install-kubectl-on-windows and following the link under “Install … [Read more...] about 3 Steps to Install Minikube on Windows 10