Scenario: To create a private docker repository in your local machine for development purpose, you can deploy a Nexus3 docker image with a persistent volume in a minute. You can either install the docker in your host machine or you can install a Ubuntu virtual box and then install docker on it.
Step1:
At first create Ubuntu virtual machine and then install docker. Next, pull the nexus3 docker image .
docker pull sonatype/nexus3
Ref:https://hub.docker.com/r/sonatype/nexus3/
Step 2:
Create a docker volume and run the Nexus container
docker volume create –name nexus-data
Next, run the docker container. Remember that nexus container will be exposed on port 8081. You also need to expose another random port that we will use as a connector port. The connector will be used to push/pull docker image to the nexus reposition from a host machine.
docker run -d -p 8081:8081 -p 8083:8083 –name nexus -v nexus-data:/nexus-data sonatype/nexus3
Note: here, we will use port 8083 for docker repository connector.
Step 3: create a docker repository
Type a name for the repository and set the HTTP port 8083 that we have opened earlier on the container while running it.
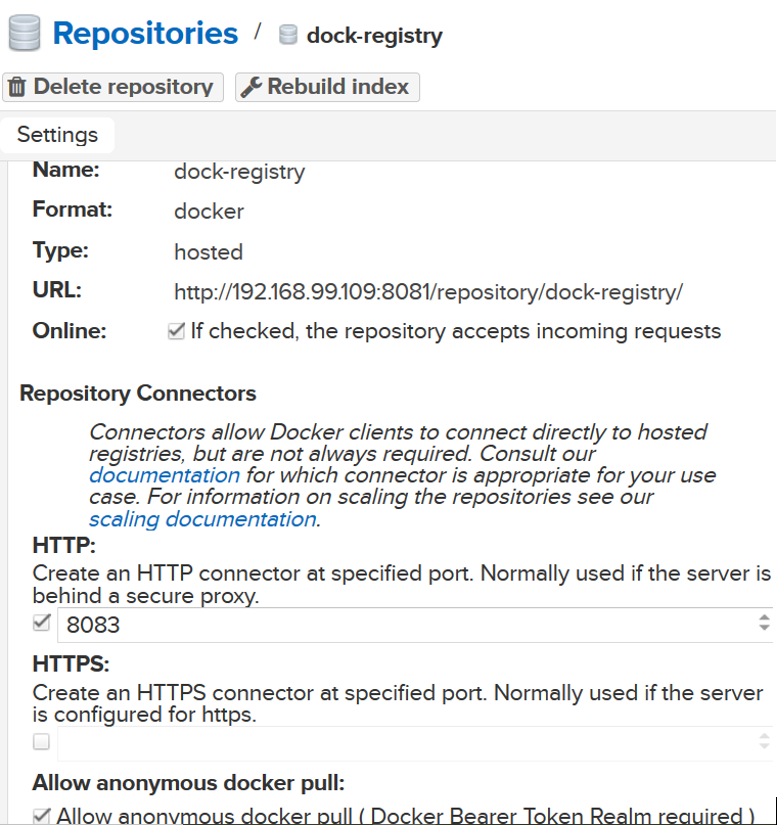
Step 4: Nexus login and user creation
The admin password is located in the /nexus-data/admin.password file in the container. Login to the nexus using http://vm-ip:8081. The default admin user name is admin. After logining in, you need to change the admin password and then create a role for the docker:
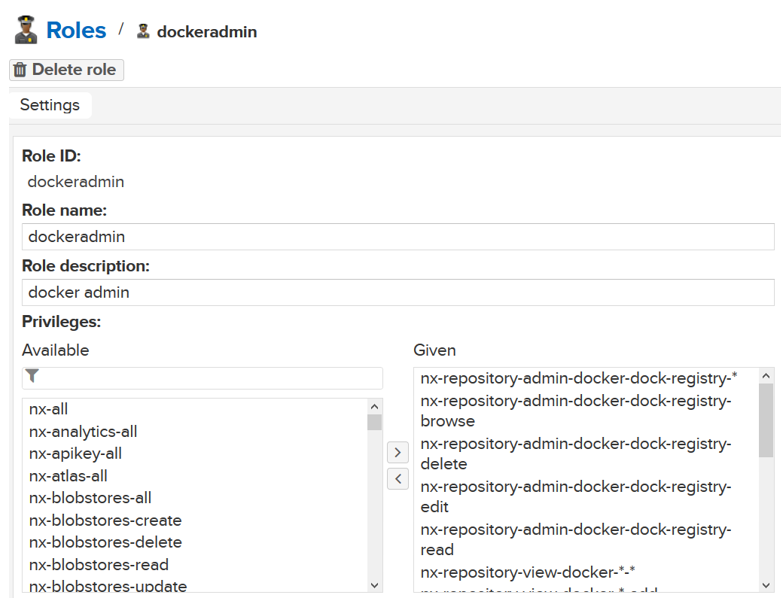
Create a user and add the username in the role.
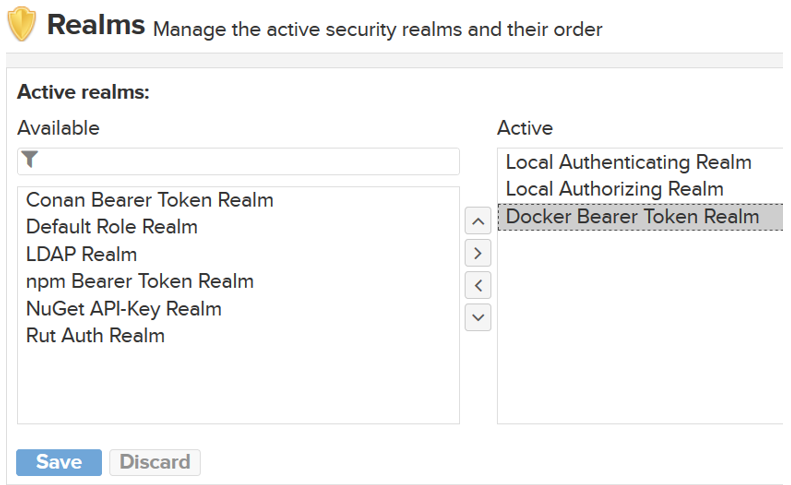
Next, click on ‘Realms’ under security and active the “Docker Bearder Token Realm” as shown below.
Test the connection from the host machine, assuming that password is Password123 the username is docker
docker login -u docker 192.168.99.109:8083 -pPassword123
Step 5: host machine
Create an VM that will simulate the client machine. Make sure the Nexus VM is reachable from this client machine. Next, install docker on it, and then create a daemon.json file in the /etc/docker location. Add the following lines into this file.
{
“insecure-registries” : [“192.168.99.109:8083”]
}
Note: 192.168.99.109 is the IP of the Nexus box. You can choose any private IP ad you like.
Restart the docker server
systemctl restart docker
Next, pull a Alpine image.
docker pull alpine:latest
Tag the docker image using your nexus IP as shown below:
docker tag alpine 192.168.99.109:8083/myalpine:latest
Push the image to your local Nexus repo
docker push 192.168.99.109:8083/myalpine:latest
If you want to pull the image, you can do so as well
docker pull 192.168.99.109:8083/myalpine
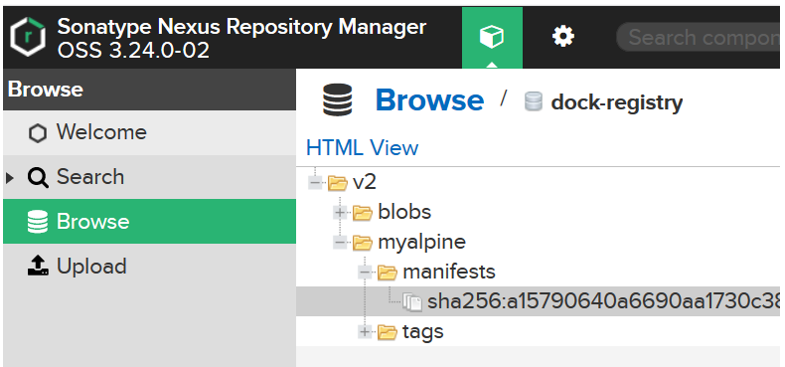
After pushing the image if you go to the browse section and click on your repository, you will see your docker image.