Web application security testing might seems intimidating and esoteric to many web administrator, especially to the new ones. Have you ever asked yourself why so many IT professionals ignore the security aspects of the applications? We seem to have a tendency to ignore things that is unperceivable. You become concern when something breaks or any security breach occurs in our IT … [Read more...] about 8 Open Source Web Application Security Testing Tools
Android Security Issues and Prevention
This post about android security intends to give the Android users as holistic view of the phone security. Apps: since android is an open platform and anyone can write apps and publish it in Google apps, the apps itself can contain malicious which may steal data and sensitive tips from your phone. So, when installing any app, try to check if the app has any security issues. … [Read more...] about Android Security Issues and Prevention
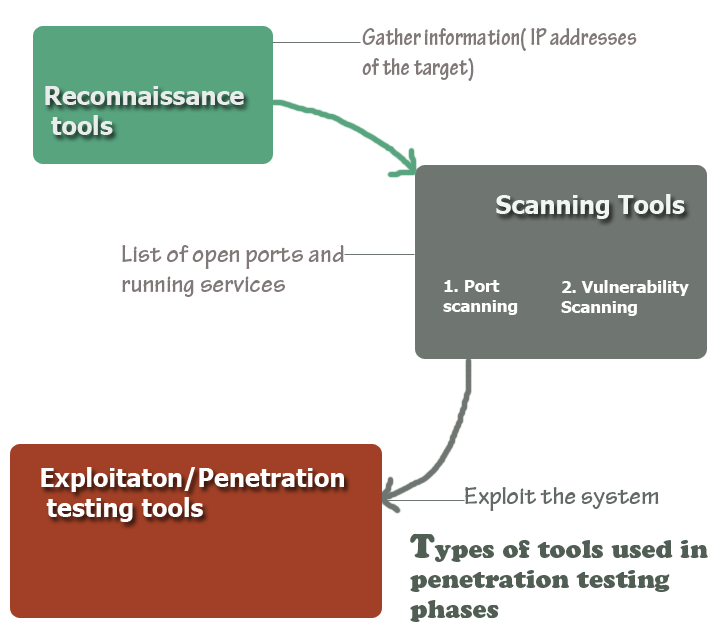
15 Penetration Testing Tools-Open Source
In footprinting or reconnaissance phase, a penetration tester collects as much information as possible about the target machine. The primary purpose of this phase is to gather intelligence so as you can conduct an effective penetration test. At the end of his phase, you are expected to have a list of IP of your target machine that you can scan later on. … [Read more...] about 15 Penetration Testing Tools-Open Source
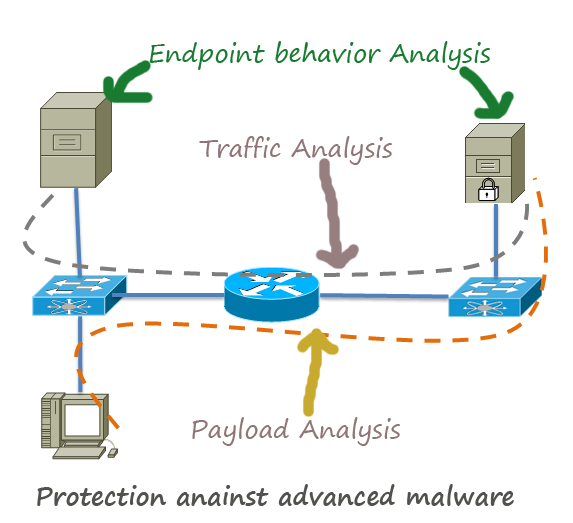
How to Protect Network Against Advanced Malware
Advanced malwares are extremely stealthy and attack targeted protocols and applications. In most cases, the attackers use these malwares to steal sensitive information from the governmental institutes financial institutes, especially the credit card service providers . Major Concerns about Advanced Malware: They are discovered after the attack has been taken place. So, … [Read more...] about How to Protect Network Against Advanced Malware
Is It Worth Doing Online Master Degree in Information Security?
As online degrees is getting recognised and accepted by the employers, many students prefer to take online courses. If you are from IT background and considering to take an online master degree in IT security, this post may help you determine whether taking online master degree help you achieve your goal. If you put yourself in an employer's shoes and think about recruiting an … [Read more...] about Is It Worth Doing Online Master Degree in Information Security?
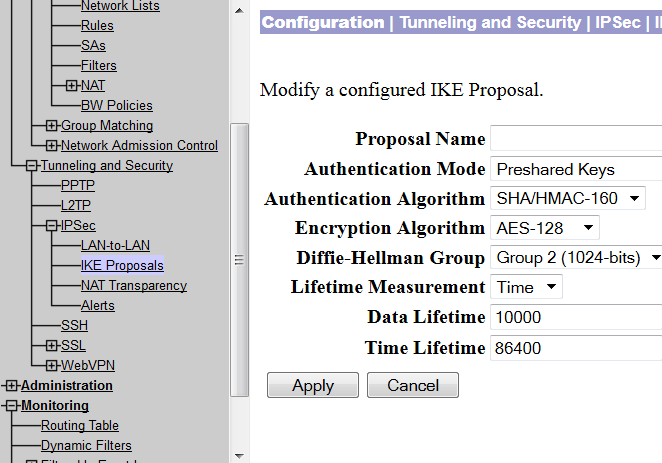
Site to Site VPN Between Cisco VPN Concentrator and Router
At times, it is economical to build a VPN tunnel with the available networking resources. For example, if you have a VPN concentrator and you need to connect a small office securely with your network, you can do so by installing a low priced Cisco router in the remote office. This post will demonstrate how you can build VPN using a VPN concentrator and a Cisco router. … [Read more...] about Site to Site VPN Between Cisco VPN Concentrator and Router
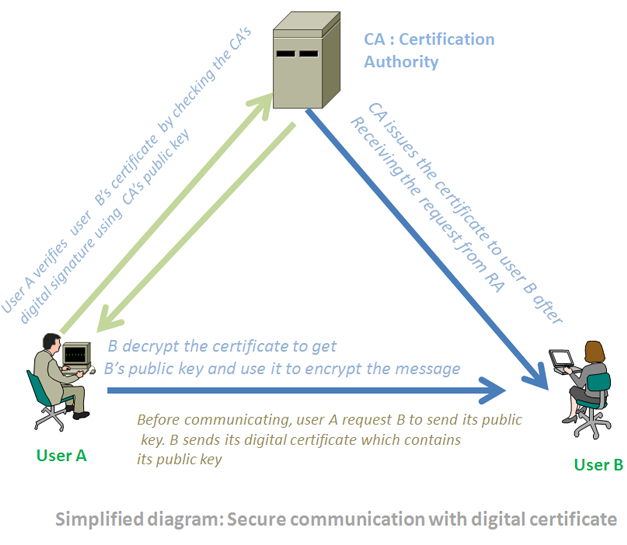
What is Digital Certificate?How it Works?
A digital certificate is a way to confirm the identity of a public key owner. Normally, a third party organization, known as CA (certification authority), is responsible for confirming or binding the identity of a digital certificate owner. It is used to establish secure communication between two parties who are unknown to each other or have lack of trust. Digital certificate … [Read more...] about What is Digital Certificate?How it Works?
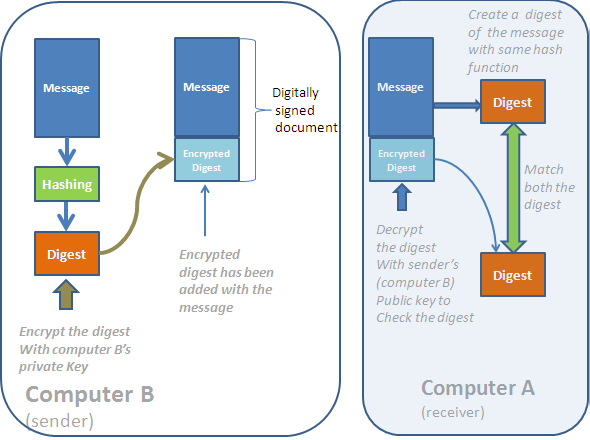
What is Digital Signature and How it Works?
A digital signature is an electronic equivalent of a physical signature. Just like the way a signature in a paper authenticates the signer, the digital signature also confirms the authenticity of the owner. Besides, it ensures that integrity of the data and non-repudiation. Non-repudiation means that the sender cannot later deny that he did not send the message. So, if you have … [Read more...] about What is Digital Signature and How it Works?
Webhosting Security-Best Practices and Concerns
To many IT professionals, webhosting security means protecting websites from hackers and malicious codes. But most of the time we forget to consider that websites security depends on a number of components such as server , application , database, scripts etc. One of the most important aspects of webhost security is to ensure continuous operation and disaster recovery of web … [Read more...] about Webhosting Security-Best Practices and Concerns
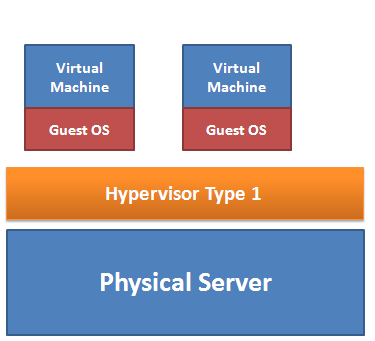
Types of Virtualization Technology-Advantages vs. Disadvantages
Virtualization helps to integrate several servers into a physical server in such a way that every server appears as a standalone server to the users. The three types of popular server virtualizations are OS virtualization, hardware emulation and paravirtualization. … [Read more...] about Types of Virtualization Technology-Advantages vs. Disadvantages
20 Forensic Investigation Tools for Windows
To investigate Windows system security breach for any potential security breach, investigators need to collect forensic evidence. Microsoft has developed a number of free tools that any security investigator can use for his forensic analysis. This post will give you a list of easy-to-use and free forensic tools, include a few command line utilities and commands. … [Read more...] about 20 Forensic Investigation Tools for Windows