A digital certificate is a way to confirm the identity of a public key owner. Normally, a third party organization, known as CA (certification authority), is responsible for confirming or binding the identity of a digital certificate owner. It is used to establish secure communication between two parties who are unknown to each other or have lack of trust. Digital certificate can assure that the person who you can want to establish communication is actually the person who he claims to be.
So, the main reason of using digital certificate is building trust between two parties who want to communicate securely.
How trust is build using digital certificate?
We can verify an unknown person’s identify when a well-known organized endorse the identity of that person. In case of digital certificate, the CA or certificate authority endorses the identity of the certificate owner, in simple words, a CA offers notarization server to give reasonable assurance that the owner of the certificate is authentic.
A digital certificate contains encrypted form of the public key of the certificate owner.
Practical application of digital certificate
Ecommerce websites use digital certificate to assure its buyers that they are who they claim to be.
Basic components of digital certificates
Encrypted public key of the certificate owner, owner’s identity information.
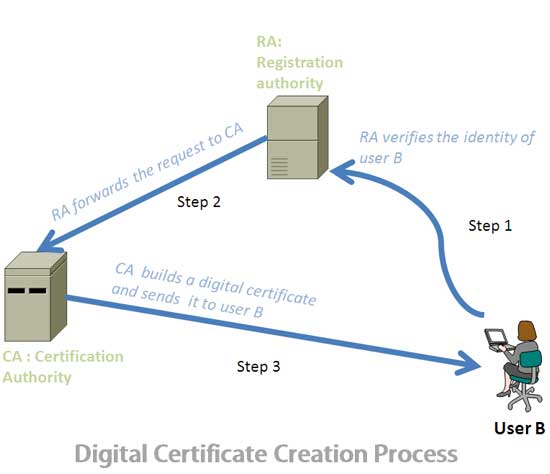
How digital certificate is created
For example, user A wants to communicate with user B securely. And user B needs a digital certificate for secure communication. At first, user B needs to acquire a digital certificate from a CA (certificate authority). In order to receive a certificate user B use the following process:
- In order to obtain a digital certificate, for the first time, user B sends a request to RA (registration authority). RA is responsible for verifying the requester’s identity; it does not issue any certificate. B may use its driving license, business document or any other identity information to prove its identity to the RA. Once the RA is satisfied with B’s identity information, it sends the request to the CA, on behalf of user B, for issuing a digital certificate.
- CS creates the digital certificate using B’s public key and other identity information. The standard used to create this certificate is x.509. The public/private key pair can be create either by the CA or by the user B. When the CA created the public key on behalf of the user, then it needs to send the private key securely to B. if B creates public and private key pair, it needs to send the public key securely to the CA in order to create the digital certificate.
- The CA signs the certificate with its own private key in order to ensure the authenticity, integrity and non-repudiation of the digital certificate. Finally, the CA sends back the certificate to B, which can be used to establish secure communication.
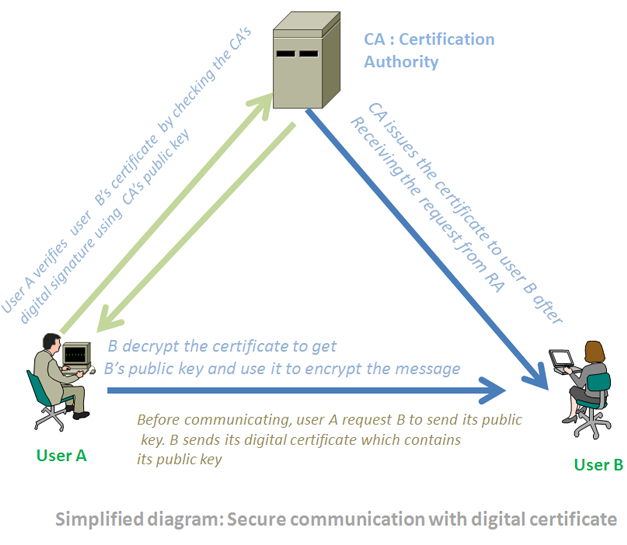
The above steps make sure the user B has a digital certificate that another user A can use to start communicating with B. To start a communication suing B’s digital certificate, A uses the following steps:
- A sends a request for B’s digital certificate to a certificate repository, also known as public directory, which is a part of CA.
- When A receives B’s certificate it verifies it with the help of web browser by checking digital signature of the CA using the public key of the CA. Then A uses the B’s public key supplied by the certificate to encrypt the message.
- When B receives the encrypted message, it uses its own private key to decrypt the message. Remember that no one except A will be able to decrypt this message because A’s private key is not shared with anyone.
Some well-known certificate authorities:
- VeriSign
- Thawte
- Comodo Limited
- DigiCert
- Network Solutions, LLC
How to verify a digital certificate?
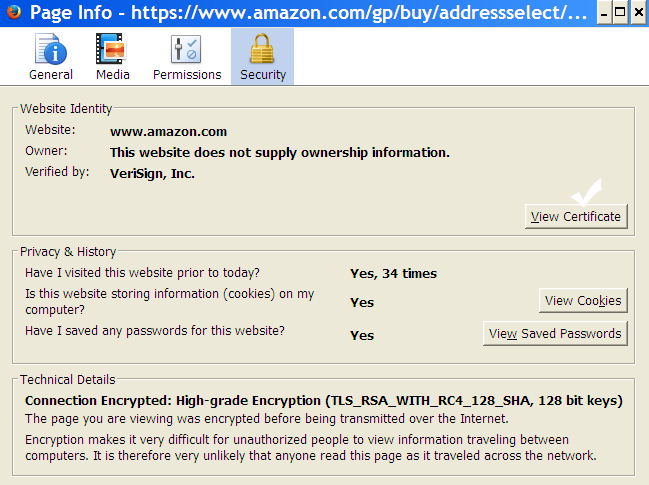
For example, you are using Firefox Mozilla to browse an ecommerce site, and you want to purchase a product. When you go to the checkout page, right click on that page and select “view page info”.
 Next, click on the ‘security’ tab and then click on “view certificate”. Check the “issued to” and “issued by” and other useful parameters that must show the website address and the name of the CA. make sure that the visited site’s domain name match with the name of the CN name mentioned in the certificate. Also check the validity period of that certificate.
Next, click on the ‘security’ tab and then click on “view certificate”. Check the “issued to” and “issued by” and other useful parameters that must show the website address and the name of the CA. make sure that the visited site’s domain name match with the name of the CN name mentioned in the certificate. Also check the validity period of that certificate.
Important points to remember:
CA: a certification authority only endorse the public key, which means authenticate the owner of the certificate to prevent the man of the middle attack.
RA: registration authority only verifies the identity of the user who wants to obtain a certificate. After verification the RA sends the request to CA for issuing the certificate. RA can never issue any certificate, instead it ease off the validation burden of the CA.
x.509: it is a standard to create a digital certificate, which has several fields such as the issuer’s name (CA’s name), version, serial number, digital signature, validity period etc. The CA uses x.509 template to create a certificate.