If you know some simple and easy-to-use methods to check that if your computer has been hacked you can confidently work online or visit any site without much worrying about your data privacy. The good news is that there are some simple ways to check that if your system has been hacked, which works well in most of the cases.At first you need to know the ways that can be used to access your PC, from a perpetrator’s perspective. A person can enter your computer directly in your absence or he can use the Internet or network connection to connect to your system.Before reading the following tips, make sure if any of the access route to your system was vulnerable.If your answer is yes, then there is a possibility that your computer might be compromised.Take a look at the following tips to check if anyone is secretively controlling your computer.
- First of all make sure that how many users’ accounts are there in your computer. Find out if there are any unknown accounts with higher privileges. Someone may create a user account without your knowledge and can use that account to access your system from a remote location. From your control panel, open the user accounts and check if the guest user is turned off and if there is any other account that you did not create. Delete any unknown account except your own administrative account and known accounts.
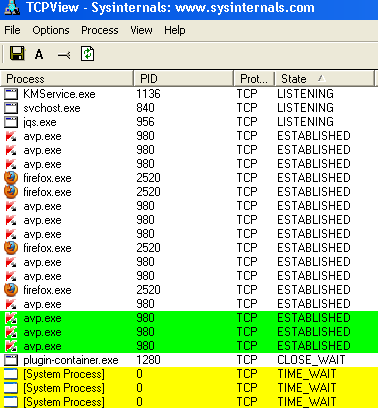
- A port can be opened in our system to snoop down on your computer. To monitor the establish TCP connection on your PC, download TCPview from Microsoft site. This is a free tool that you can use to view the established TCP and UDP connection. After downloading this software just run the tcpview file and then check how many established connections are there. You can see the list of connection under the ‘state’ bar. To check how this piece of software performs, you visit a website and then see how the status bar is updating its connection status. Once you close all the websites opened in your browser all the established TCP connection should be gone. If you have antivirus installed in your PC you will always see a list of establish connection , ignore those and check if there are any unrecognizable processes running which has established TCP connection. If you find anything suspicious then right click on the connection and click “end connection”.
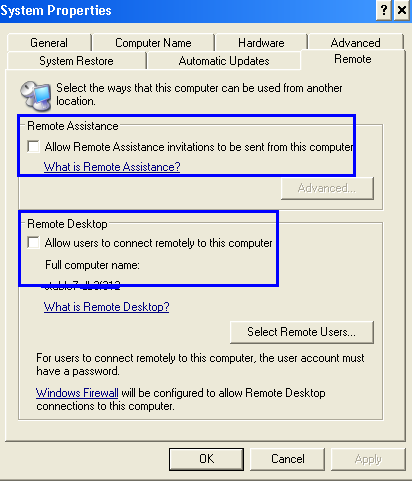
- Check for remote desktop settings. You must keep it turned off. To disable these settings, right click on My Computer and the click ‘remote’ and uncheck both remote assistance and remote desktop.
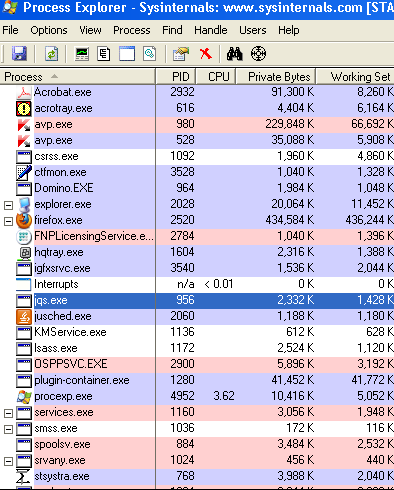
- Check for processes that are using your system. You can use either Process Explorer or Windows’ own process monitor to check for unknown processes. If there is any unknown or suspicious processes then kill it. You can read articles from Microsoft to learn more about processes. For the time being you can check this post to find if you have any illegal processes running on your computer. http://www.labnol.org/software/windows-process-or-virus/18008/
- If you have any IRC or Internet relay chatting program that you do not use for communication, then you better delete it.
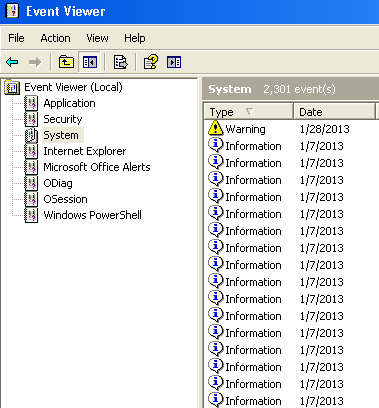
- Check the security warnings in the event viewer. The events come as warnings, errors and information. Go through all the event options including security. You can use the filter option to sort the events in terms of their severity. Filter option is on under the view tab of event viewer window.
- Checks add/remove programs. If there are any unknown programs that you have not installed then try to find out what that application do in your computer.
- Check your browser has any newly installed plugins or extensions that you do not recognize. If you are using Firefox then click on Tools and then click Ad-ons. Check both the extensions and ad-ons tab to find any suspicious plugins.
- Another useful way to check suspicious activity is to check if your latest security updates or patches or service pack has been uninstalled. To exploit a known vulnerability, a hacker may uninstall your security updates and then use his backdoor programs or any other means to take control of your computer.
- Scan your computer for backdoors and spyware since both of these software can work as a Trojan horse which most of the hackers use to get remote access to your computer.
- If possible try to find out network usage report of your computer. If anybody is sneaking on your PC, then your network card will be consuming more bandwidth than your usual bandwidth usages.
- Always use the monitoring features of your Internet security software. Almost all of the paid version of the security software generate threat reports and warnings about unusual activities in your computer. Never undermine the power of social engineering.in your absence anyone can install a backdoor program in your system to gain remote access-so never leave your PC unlocked.
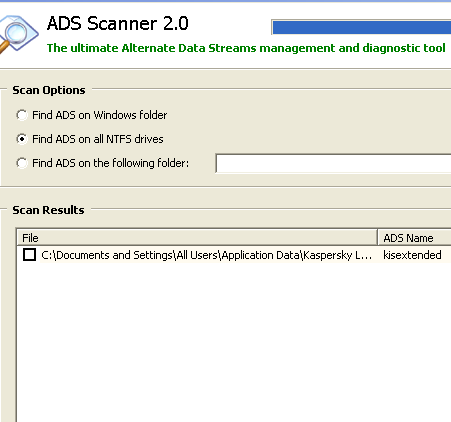
- There are ways that can be implemented to hide malicious program in your windows system. One such way is using alternate data stream. If your computer has a NTFS volume then it supports ADS. Alternate data stream was created to support Macintosh Hierarchical Files system (HF) in Windows machine. With the help of ADS anyone can hide malicious programs including executable files in your Windows computer. Fortunately, there is a free tool called ADS Scanner that can help you detect the existence of ADS files in your system.
- There are advanced hacking techniques that can break the ring 0 or kernel level security and ring 1 or device driver level security of your operating system. If this is the case, you will have two options-either to take help from the professionals or reinstall your OS.
Mcafee has a useful page that offers free tools for forensic analysis of our PC. Mcafee Tools
You might also be interested to read about: