When an IT organization relies on a single DevOps engineer for managing infrastructure without redundancy in that role, several significant risks emerge: … [Read more...] about Why IT Organizations Should Consider Having At Least Two DevOps Engineers or Equivalent Roles?
Off Track
Six Easy Steps to Create a Self-Signed Certificate on Ubuntu Server
A self-signed certificate is an SSL certificate that is signed by the person or organization creating it, rather than a trusted Certificate Authority (CA). You can use a self-signed certificate for testing purposes, or to provide encryption within internal networks. If you are looking into renewing a self-signed SSL, please take a look at How to Renew Self-Signed SSL … [Read more...] about Six Easy Steps to Create a Self-Signed Certificate on Ubuntu Server
What Elon Musk Needs Doing to Make X.com(Twitter) Great Again?
As of mid-2024, X (formerly Twitter) has undergone significant transformation under Elon Musk's ownership. The platform has rebranded to X, aiming to become an "everything app" similar to WeChat. It has introduced longer posts, video content enhancements, and is working on integrating payment services. Yet, many users still think that Elon Musk could improve it even further by … [Read more...] about What Elon Musk Needs Doing to Make X.com(Twitter) Great Again?
Top 10 Cloud Based Threats
Cloud-based threats refer to security risks and vulnerabilities that are specifically associated with cloud computing environments. These threats target cloud services, platforms, and infrastructure, as well as the data and applications hosted in the cloud. As organizations increasingly adopt cloud technologies for storage, computing, and other services, understanding these … [Read more...] about Top 10 Cloud Based Threats
3 Steps to setup SSH remote Access to EC2 from Cloud9
When you need to connect securely to an already running EC2 instance via SSH from a Cloud9, you need to prepare the instance for Cloud9. AWS Cloud9 generate a SSH public key to connect securely to your EC2 server. To start a secure connection from Cloud9 via SSH you need to setp the the SSH key, generated by Cloud9, to EC2. … [Read more...] about 3 Steps to setup SSH remote Access to EC2 from Cloud9
3 Steps to Setup EC2 EBS Volume Disk Space Monitoring using Cloudwatch
The default monitoring of Amazon EC2 does not track the EBS disk space. To monitor disk space in EC2 instance, you need can either manually installed Cloudwatch Agent or can use SSM to install the agent. After installing you Step 1. Instal cloudwatch agent sudo yum -y install amazon-cloudwatch-agent Step 2. create a config.json file in the following … [Read more...] about 3 Steps to Setup EC2 EBS Volume Disk Space Monitoring using Cloudwatch
How to Create a Helm Chart in Windows for Minikube
Helm package manager is used to deploy applications in the Kubernetes cluster. By packaging your app using helm allows to deploy it with one command instead of using “kubectl create/apply” command. Another benefit of using helm is that you can easily upgrade and rollback your apps when required because helm uses version control. Follow the three simple steps creating … [Read more...] about How to Create a Helm Chart in Windows for Minikube
5 Steps to Auto-Create Helm Charts and upload to S3 Using Jenkins
After packaging the helm charts, you need to store it in a repository so that it can be easily deployed using helm in the Kubernetes or Minikube. This post aims to show you how to set up the AWS S3 bucket as a Helm chart repository. Using the steps below you will be able to setup Helm S3 repo for both Minikube and KOPs created cluster hosted in AWS. Scenario: we will create … [Read more...] about 5 Steps to Auto-Create Helm Charts and upload to S3 Using Jenkins
3 Steps to Install Kubectl, Helm 3 and S3 Plugin in Ubuntu to Store Charts in S3 Bucket
This post aims to show you how to install Kubectl, Helm 3 and S3 plugin so that you can easily store the chart in a S3 bucket form your Ubuntu machine. Though I always use an automated approach to create and store the helm chart, I had to create a helm chart in Ubuntu in order to identify and Helm S3 plugin compatibility issue. 1. Install kubectl To install kubectl in … [Read more...] about 3 Steps to Install Kubectl, Helm 3 and S3 Plugin in Ubuntu to Store Charts in S3 Bucket
How to Run MySQL Database Anonymize Script from Linux Bash Shell
How to run mysql annoymise scripot from bash shell. To anonymize the production database for using in the test environment, you can create a simple script that can run from the Linux Bash shell with a single command. At first download a sample database: # wget https://github.com/datacharmer/test_db/archive/master.zip Next, unzip the file # unzip master.zip … [Read more...] about How to Run MySQL Database Anonymize Script from Linux Bash Shell
How to Mount Amazon EFS in EC2-CentOS Instance
With Amazon EFS(elastic file system)mounted in the EC2, you can signifincalty reudce cost of storge becaues you pay only for the storgrage used by your applications/data. EFS supports NFS In the AWS console, search for EFS and then create a volume. When you attahce a security group in the EFS, make sure it allows traffc on port 22 from the EC2 instance. Also, take note of the … [Read more...] about How to Mount Amazon EFS in EC2-CentOS Instance
How to Schedule AWS EC2 Start and stop time using Lambda and Cloudwatch
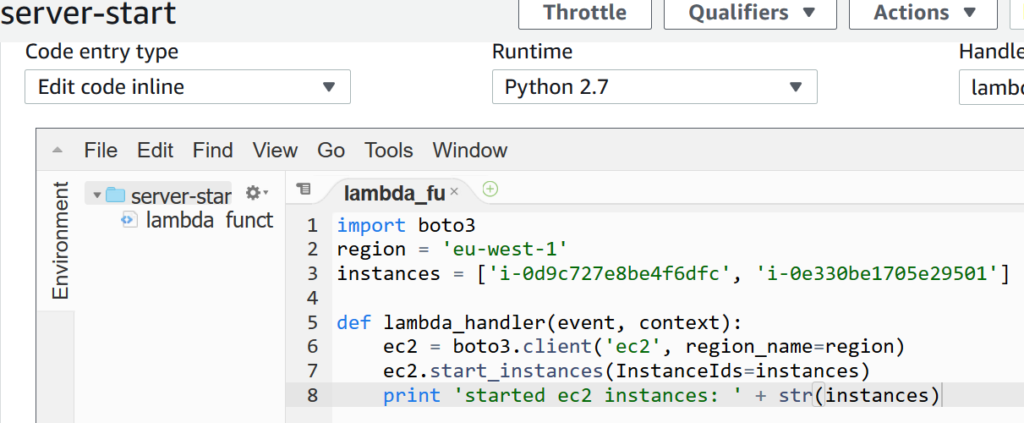
To save your AWS cloud operational cost, you can schedule EC2 instanes' start and stop time using Lambda function. When you define a lamda function, you need to setup a trigger, which specifies the event that can invoke the lambda fucntions. In this post, we will use the a specific UTC time as a trigger . For example, you want to start EC2 instances at 06:30 UTC and want to … [Read more...] about How to Schedule AWS EC2 Start and stop time using Lambda and Cloudwatch
Docker Command List with Examples in Linux
Spinning up a docker container takes a few seconds with a simple command.Once the containers is up and running you need to customize and manage it to fit for the apps and other requirements. I have put together a number of useful command with examples that a beginner will find handy. Docker MySQL container installation commands docker container run -d -p 3306:3306 --name … [Read more...] about Docker Command List with Examples in Linux
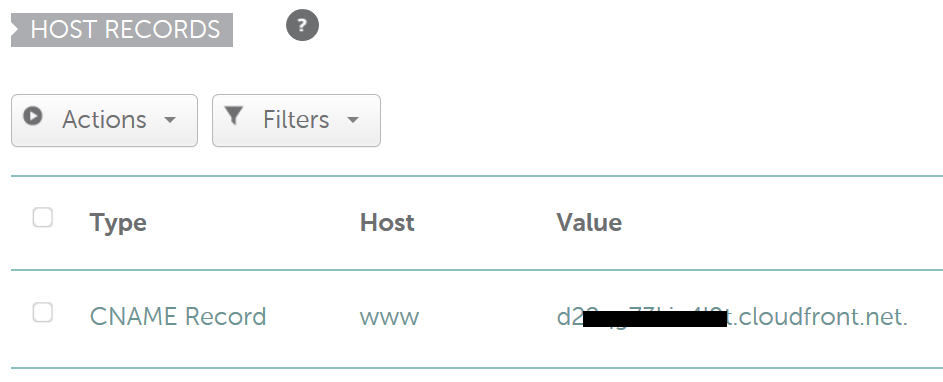
How to Setup AWS CloudFront for Externally Registered Domain Name
If you do not want to transfer your domain to Amazon DNS(Route 53) and want to use AWS CloudFront to deliver your content, you can use the instructions below to set up your content delivery network. Scenario 1: you are using an external DNS for CloudFront and do not want to create a hosted zone in Amazon route 53. For example, your domain is registered with Namecheap and you … [Read more...] about How to Setup AWS CloudFront for Externally Registered Domain Name
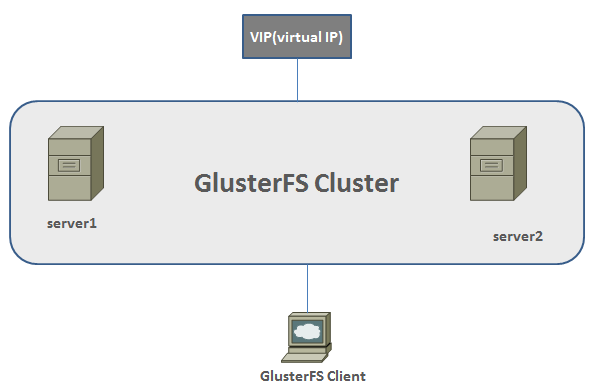
How to Build High Availability Web Server with GlusterFS on Debian
Scenario- this post aims to help you build a high availability cluster for websites using GlusterFS on Debian server. In this installation there will two servers-forming a cluster for web contents- that will replicate each other and the third one will be a client server. If you want to add anything in the cluster you have to add it in the client machine, which will be … [Read more...] about How to Build High Availability Web Server with GlusterFS on Debian
9 Advantages and Disadvantages of Cloud Computing for Business
Deciding to move on to a cloud means moving your data into somebody’s computers. To develop your computing facilities without investing in hardware and infrastructure is what cloud computing all about. In an organization, you may be the decision maker thanking about whether to put your data in a third party cloud or in your own cloud. You can have a look at the following … [Read more...] about 9 Advantages and Disadvantages of Cloud Computing for Business
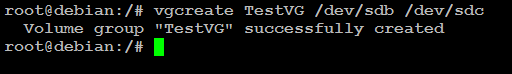
How to Extend Linux LVM by Adding a New Hard Disk
You may need to add new disk to your Linux LVM for various reasons such as for adding capacity for your existing applications or new applications. This post aims to show you how you can add a new disk to your existing LVM as well as to a new LVM. The difference between adding a new disk to a new LVM and to an existing LVM is that in the latter case you do not have to create a … [Read more...] about How to Extend Linux LVM by Adding a New Hard Disk
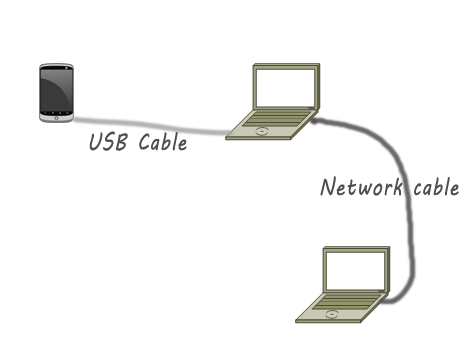
How to Share Internet Connection using Android Mobile Tethering
This post aims to help learn how to connect an android mobile to laptop for sharing Internet connection. For USB tethering, you must need to your mobile’s USB cable to connect to the computer or can use wireless connection. … [Read more...] about How to Share Internet Connection using Android Mobile Tethering
32 Effective Home Security Checklist
Massachusetts Crime Watch has developed a useful home security list that helps to enhance home security. If you are looking for simple tips to make your home safer than before, have a look at the following list. Remember that you do not need to implement all the recommendations. Have a look at the list at first and then decide which recommendation fits your needs. … [Read more...] about 32 Effective Home Security Checklist