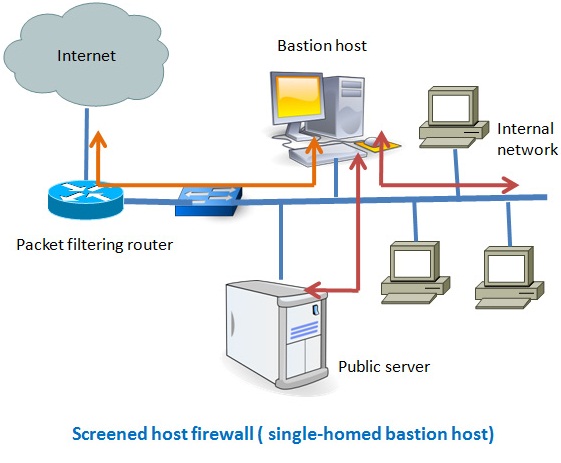
There are several types of firewalls that work on different layers of the OSI model. Depending on the kind of service and security you need for your network, you need to choose the right type of firewall. The following are the list of seven different types firewalls that are widely used for network security. Screened host firewalls Screened subnet firewalls Packet … [Read more...] about 7 Different Types of Firewalls
Laptop Security Devices and Tips
Providing physical security to your laptop is your primary concern if you are a frequent travel or on the move. There are a number of devices and precautions that you can take to secure your laptop and even can get back your laptop if it gets stolen. The following are a list of devices and suggestions the you may consider as a solution to your laptop security. … [Read more...] about Laptop Security Devices and Tips
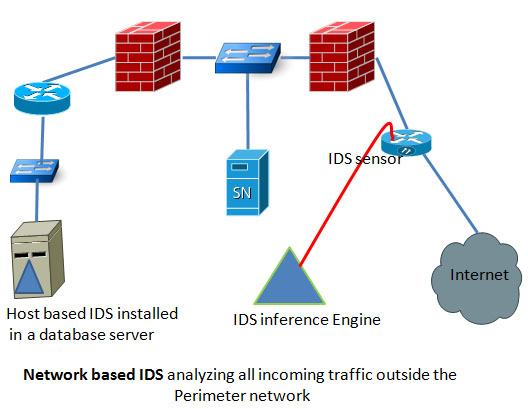
Host Based IDS vs Network Based IDS
Based on the location in a network, IDS can be categorized into two groups. One is host based IDS and the other is network based IDS. Both have its own advantages and distant ages. Before you decide which IDS suits your network environment the best you need to have a clear concept of both types of IDS. Network based IDS: these types of IDS are strategically positioned in a … [Read more...] about Host Based IDS vs Network Based IDS
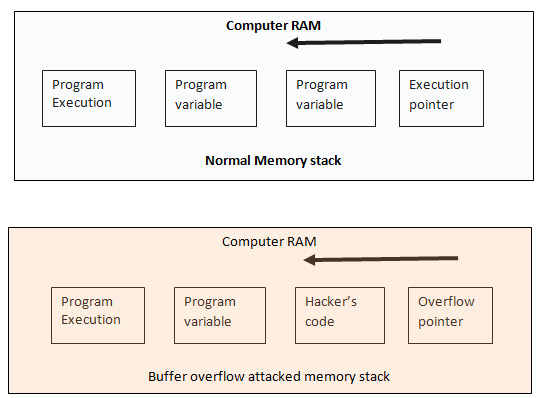
Buffer Overflow Protection Tutorial
When you write a simple program, for example, to print user name with greetings. For this program to run you assign character string 38 in the following way Char name (38) Here “name” is the variable name. The above code specifies that you name or users’ input would not be more than 38 characters long because you have already assigned only 38 bit of data into the buffer. … [Read more...] about Buffer Overflow Protection Tutorial
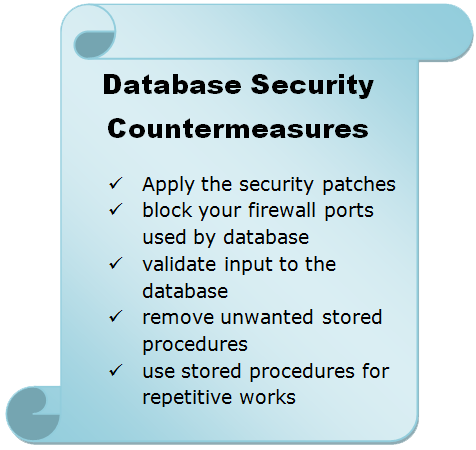
Database Security Issues and Countermeasures
One of the least prioritize part in data base security is not taking countermeasures against database access. Some solid measures that you can take to secure the access methods in your database are: Whether you use Oracle database or Microsoft SQL database, both the organization releases their security patch almost regular basis. So, make sure that you visit the security … [Read more...] about Database Security Issues and Countermeasures
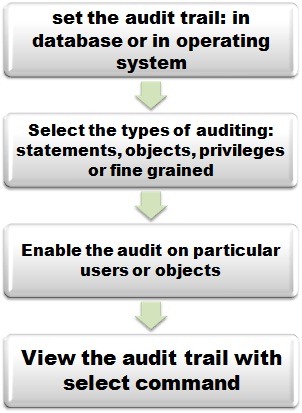
Oracle Audit Setting Commands
An auditor needs to check the Oracle database in order to gather some useful and important information to conduct his audit. In fact, an auditor will ask the system administrator to run the commands and collect the information on behalf of him. The following are the basic commands that you need to know before starting the proper audit of the audit trail. To get a list of all … [Read more...] about Oracle Audit Setting Commands
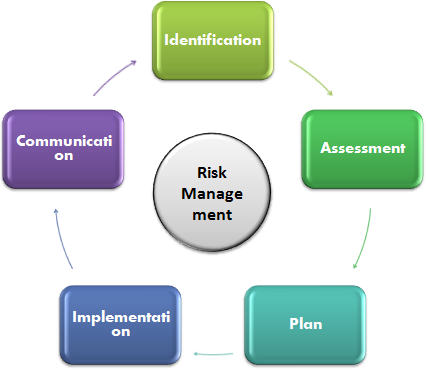
Risk Management Process Simplified
Risk is the possibility of happening unknown or known events that can affect the main objectives of a project. It is not necessary that all the risk will cause disruption in achieving objectives of a goal because a risk can come in the form of a threat or an opportunity. If it comes as an opportunity that it will help the project to get benefit out of it. If you want to keep … [Read more...] about Risk Management Process Simplified
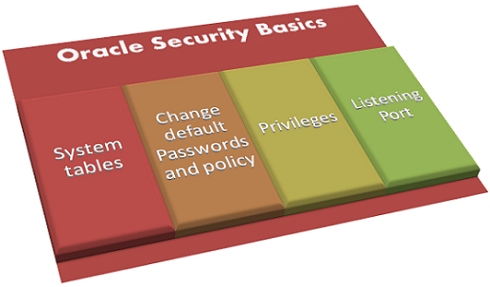
Oracle Security Basics
Popularity has a price to pay since everything on this world has its face value. And Oracle database software is no different than that. In this post, you may expect to have some basic idea on Oracle security and its risks. The features of Oracle that has security risks are: System tables Passwords Privileges Oracle Listener … [Read more...] about Oracle Security Basics
Audit Charter Explained
What is an Audit charter? An audit charter is the base of an audit because every auditor starts his audit with an audit charter. In simple words, an audit charter defines the responsibilities, authority and accountability of an auditor along with the scope of the audit. Normally, a charter also specify the management’s responsibility and their delegation of authority to the IS … [Read more...] about Audit Charter Explained
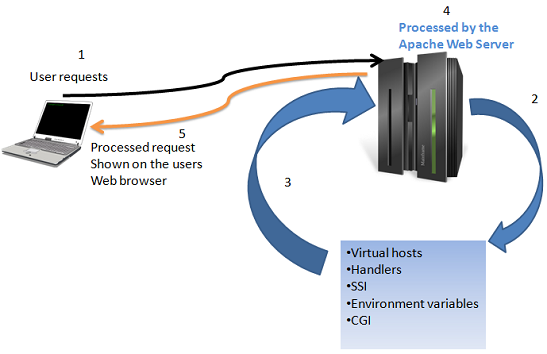
Apache Server Features with Vulnerabilities
Apache is one of the prevalent web servers because of its expandability with features, support community and cost. If you consider using Apache as a solution to your web server and want to implement the most basic security requirements, then you need to have clear understanding of some of the most ubiquitous features of Apache and those features are: Virtual hosts Server … [Read more...] about Apache Server Features with Vulnerabilities
11 Essential Skills of an IT Auditor
Without proper knowledge of the information technology and systems that you are going to assess, it is almost impossible to audit IT systems.to find the flaws in a system you must know, at least, how it works and its potential vulnerabilities. So, the essential skills an IT auditor need are database, operating systems, web technologies, networking and business processes. The … [Read more...] about 11 Essential Skills of an IT Auditor