VOIP saves money if you can deploy and manage it properly, but there are certain risks that you need to take into account. As you know that VOIP is ip based voice solution and IP network is always vulnerable and point of interest to the intruders. … [Read more...] about 32 Proven VOIP Security Best Practices
Tips for Foreign Travel Risk Assessment and Management
You may be subject to intelligence espionage while you travel in foreign countries. There can be a number of reasons whey you can be a target. You can be government officials or may be a business person. If the intelligence agency in the foreign country thinks you possess valuable information, you can be a victim. This post helps you identify the clues that may suggest that … [Read more...] about Tips for Foreign Travel Risk Assessment and Management
12 Things to Remember when Handling Classified Information
When a piece of information is crucial and can cause serious damage to the national security can be considered classified information. Based on the severity of the damage, classified information can be categorized as top secret (if leaked can cause highest level of damage), secret and confidential (will not cause significant damage if confidential information get leaked). … [Read more...] about 12 Things to Remember when Handling Classified Information
List of Popular IT Security Standards
The good news for IT security professionals is that there are a number of IT security standards that they can use as a guideline when developing or implementing IT projects. Remember that these standards are well thought out and proven practices that can improve information security goals of your organization. Only the popular and globally recognized IT security standards have … [Read more...] about List of Popular IT Security Standards
63 Web Application Security Checklist for IT Security Auditors and Developers
As you know that every web application becomes vulnerable when they are exposed to the Internet. Fortunately, there are a number of best practices and coutner measures that web developers can utilize when they build their apps. This post will list some proven counter measures that enhance web apps security significantly. … [Read more...] about 63 Web Application Security Checklist for IT Security Auditors and Developers
Simple Ways to Prevent Cyberbullying -What Parents Should Know?
A study conducted by UK based charity Beatbullying showed that almost 73% of the people knew who was sending them bullying messages. If you are a parent of a teenager, remember that cyberbullying is more common among teenagers and keep reading this post in order to get a few insights on protecting your kids from the cyber neurotics. … [Read more...] about Simple Ways to Prevent Cyberbullying -What Parents Should Know?
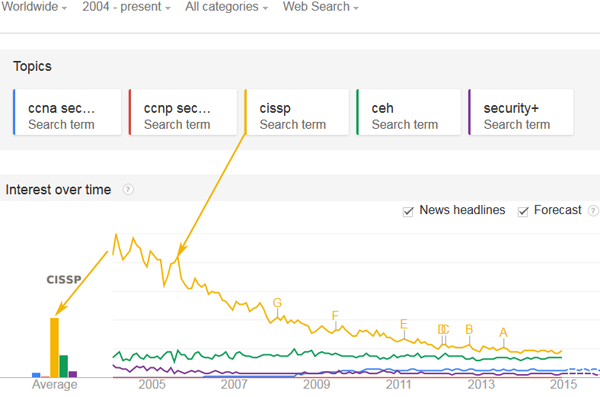
Top 5 Network Security Courses
Fortunately, there are a number of network security courses out there that meet the current needs for security expertize. This post will discuss about the top five network security courses that are both highly sought-after and popular among the IT professionals.The following graph shows the current demand and forecast for all the five network security courses discussed in this … [Read more...] about Top 5 Network Security Courses
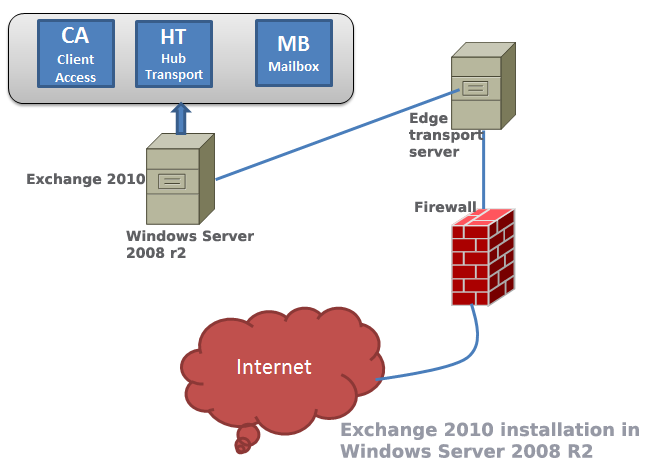
12 Steps to Install Exchange Server 2010
Among all Microsoft’s solution Exchange is considered a bit tough to master in. But your learning curve will be much more smoother if you follow a few simple steps described in the following paragraphs. … [Read more...] about 12 Steps to Install Exchange Server 2010
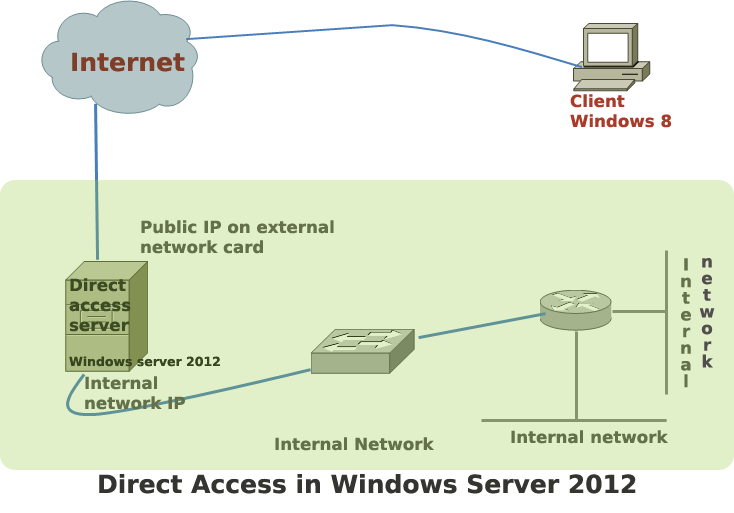
Steps to Configure Direct Access in Windows Server 2012
Direct access is the commercial name of Windows 2012 server’s remote access solution. In earlier versions of Windows, remote access offered limited features to the remote users. Windows 2012 is the first Microsoft server that makes remote access users feel like working within the corporate network. … [Read more...] about Steps to Configure Direct Access in Windows Server 2012
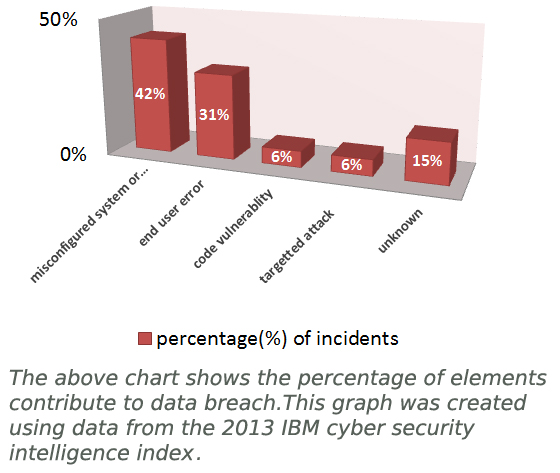
Data Breach Insurance Explained
What is data breach insurance? As more and more people are getting accustomed to cyber life, the more money is pouring into the Internet and internet-related business. As a result, we are witnessing more incidents of data breach incidents each year. The fact about Internet security is that no business is secure when they go online and the threat landscape is getting more … [Read more...] about Data Breach Insurance Explained
8 Open Source Web Application Security Testing Tools
Web application security testing might seems intimidating and esoteric to many web administrator, especially to the new ones. Have you ever asked yourself why so many IT professionals ignore the security aspects of the applications? We seem to have a tendency to ignore things that is unperceivable. You become concern when something breaks or any security breach occurs in our IT … [Read more...] about 8 Open Source Web Application Security Testing Tools