What is ACL: Access control list or ACLs are a set of if-then rules set on a router to allow or deny a specific group of IP to send or receive traffic from your network into another network.
When you apply an ACL to a route interface for incoming traffic then every incoming packets will be compared with your ACL first, if a match is found then either permit or deny action will take place according to your configuration of the ACL. If there are more than one ACL and if there is no match after comparing the incoming packets with the first ACL, then the second ACL will be matched and so on. Remember there is an implicit deny after an ACL. That is why after permit or denies any IP or IP range you must add the command: access-list ip permit any any.
For example in your network you want that no computer or devices from 172.16.0.0 network can send traffic to your network. To implement this rule you need to write and ACL that will tell your router to discard all the traffic from 172.16.0.0. Now, let see how to implement this ACL into a router.
Rourter#configure terminal
Router(config)# access-list 10 deny ip 172.16.0.0 0.0.255.255
Router (config) #access-list 10 permits ip any any
(If you do not add the line “access-list 10 permits ip any “then all the traffic from any network will be denied. Since you only want to deny the IP from 172.16.0.0 network then you must allow IP from other networks.)
Now, you have written an access list that you must add into an interface. Remember if you write an ACL and do not add it into any interface then that ACL is of no use. For example, 172.16.0.0 network or any other network can connect your network via your router fastethernet 0/1 port. So, you just have to add the access control list into your fastethernet port 0/1 and want the all the incoming traffic this port from that specified network must be denied. To add this ACL in your router use the following commands.
Router (config)#access-group 10 in
the above example was the most simple form of access list known as standard access list.if you want to stop only a specific IP(e.g. 192.168.1.1) from sending data to your network then use the host command
Router(config)#ip access-list 15 deny host 192.168.1.1
Router(config)#ip access-list 15 permit any any
Types of access list: there are two types of access lists
A. standard access list
B. extended access list
Standard access list: this access list control IP allow or deny IP based on the source IP address of a packet and this kind of access control list must be implemented near the destination of an IP packet. You can create a standard access list by using the number 1-99 or 1300-1999(expanded range).
Command format of standard access control list:
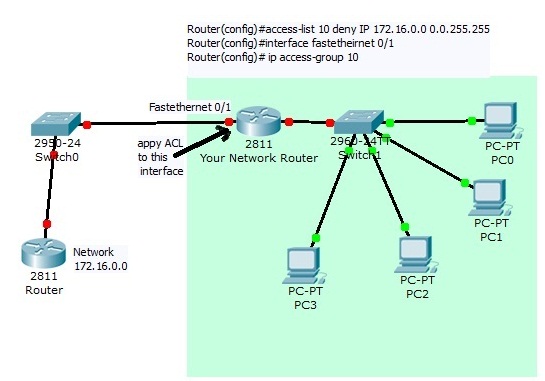
Router(config)#access-list (access list number) (permit/deny) (source IP) (wild card mask)
Router(config)#access-list 10 deny IP 172.16.0.0 0.0.255.255
Router(config)#interface fastetheirnet 0/1
Router(config)# ip access-group 10 ( applying the access list 10 in an interface)
Extended access list:
Unlike standard access control list, extended ACLs allow you to specify the source and destination IP address. Moreover, you can specify which protocols and service ports (www, telnet, and ftp) you want to deny in your router. You can use 100-199 and 2000-2699(expanded range) for specifying your extended ACL. For example you want to deny Telnet connection originating from outside to your host computer with IP 172.16.100.100, and to do that you have to write the following extended access control list on your router and then apply it to a interface that you expect to receive incoming Telnet request from outsiders.
Router(config)# access-list 120 deny tcp any host 172.16.100.100 eq 23 log
23 is the port number of telnet and the “log” command will log all the telnet attempts made to your host IP 172.16.100.100.
If you did not add the “eq 23” in the above access list, then your router would deny all the tcp packets irrespective of its destination port, which means if a person try to FTP to your host he would be denied.
How to configure your router for accepting Telnet from only a specific IP
Access list also is a great way to enhance your router’s security. If you want only a single IP can perform Telnet operation to your router, then you just have to create an ACL for the specific IP (172.16.16.16) and then just add the ACL to your “Line Vty”
Router(config)# access-list 20 permit 172.16.16.16
Router(config)#line vty 0 4
Router(config)#access-class 20 in
You might also be interested in learning how to implement Cisco VPN(virtual private network) and HSRP
