What is data breach insurance?
As more and more people are getting accustomed to cyber life, the more money is pouring into the Internet and internet-related business. As a result, we are witnessing more incidents of data breach incidents each year. The fact about Internet security is that no business is secure when they go online and the threat landscape is getting more complicated as we are developing complex applications to meet customer needs.
The main purpose of data breach insurance is to secure your business against the harm caused by any cyber-attacks or any other criminal activities that involve data breach.
A data breach may occur in the following forms:
- The leak of personal data, personal identification information (employees’ information).
- Defacement of business website.
- Credit card data breaches.
- Tempering of existing data in order to disrupt or manipulate normal business operations.
- Disclosure of sensitive business data
What is at risk?
Though it is easy to replace damaged IT assets and restore damaged data from backup servers, you may never regain the lost reputation due to data breaches. Will you feel safe to transact with a business that has a number of previous records of data breaches.
Types of data that are at risk
- Customers’ credit card information.
- Patient’s medical records.
- Social security numbers.
- Sensitive business data, bidding information etc.
Who wants their reputation to be on the line because of data breaches?
The answer is only the competitors of your business.
Planning for cyber insurance
Though cyber insurance is around for a couple of years, many security professionals do not have a clear concept of it when it comes to buying a cyber-security policy. When you plan to insure your organization with cyber insurance, make sure that you have clearly identified all the major and sensitive IT ASSETS INCLUDING data that are critical for business operation. No matter how IT plays its role in the proper function of a business, one thing is always vulnerable and one of the main reasons of cyber-crime is your DATA. Data has been the primary target because cyberspace is all about data. An incident of a data breach may cost you millions regardless of the loss of reputation; you may be in the damage of out of business in the long run. Instead of trying to avert the risk with insurance, you need to have a decisive plan for your cyber defense and measure how strong you are to countermeasure the prevalent threats. Think about the following questions?
- How strong your Internet security mechanism?
- Have you implemented any information security and management standard?
- How is the situation of your security team?
- How often do you conduct a security audit?
- When did you last conducting penetration testing?
- Do you have any previous records of cyber mechanism?
- How confidant are you about your own IT personnel’s integrity?
Third-party vs. first-party insurance
In general, there are two types of insurance that can help you with data breach incidents. The first one is first-party insurance and the second-one is third-party insurance. Non-IT firms are suitable for first-party insurance. By non-IT we mean where data does not function as the main element of the business. When a non-IT firm experience a data breach incident, they can file a claim for the damage. Of course the amount of compensation will be based on the policies, the coverage and the type of industry.
Generally, first-party insurance covers the followings:
- The expenses for notifying the customers about the breach. It is obligatory to notify every customer affected by a data breach.
- Cost for credit monitoring service. When an incident occurs, the customers’ accounts may need to be monitored. Imagine you have 100 million customers and expecting data breaches in 20% of those accounts.
- Payment for business interruption. Because of a data breach, the normal business operation may come to a halt and lose revenues.
- Public relation cost. Every cyber incident weakens the reputation of the company. As a result, both the customers and other businesses feel unsafe doing business with the affected company. If your organization does not have a strong and experience public relations team, with a previous record of dealing with such incidents, you may need to hire a PR team to recover your business reputation.
- Cyber attackers may threaten you to cause severe damage or may do so or can ask for extortion. Make sure you are covered for cyber extortion as well.
- If you have a public limited company, make sure if you want to cover for the fall in stock price due to the attack incident.
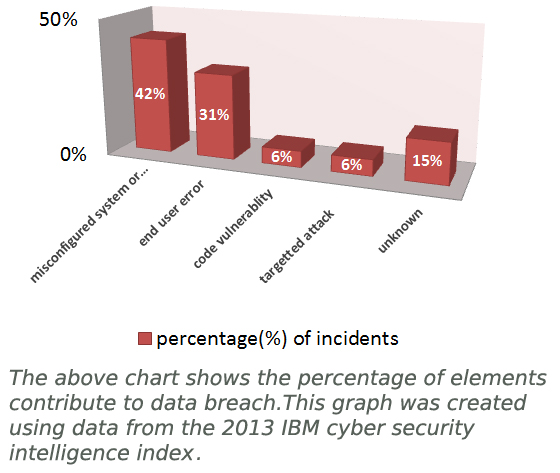
Third-party insurance
Most of the core IT service providers either design or manage data and infrastructure for other organizations. Some even deal with sensitive data of the clients. Think about clouding services where customers keep their data on the service providers’ premises. If you are a cloud provider, you may be sued for customers’ data breach. If you are an IT designer, a customer may sue you for a data breach because of your faulty design. To protect yourself and your business in such scenarios, you need third party insurance.
How to save on insurance?
To save on premiums you need to prove that your business falls into a low-risk profile category, and you are already in compliance with well-recognized and proven IS (information security) standards, have strong IT security monitoring, and the audit team. What insurer love to see is that you have a little chance of filing a claim for a data breach.
Before making a decision to buy data breach insurance, make sure you have proper expertise in your organizations, who understand the pros and cons of every term of the insurance policy. It is advisable to consult with a proper cyber insurance broker who can advise you on the appropriate solution for you.
