What is ransomware? Ransomware belongs to the family of malware used to take control of users’ machines and the users get back control of the machine when the victim pays a ransom to the attackers. There are a number of preventive steps that a user can take to avoid ransomware attacks. But before delving depth into the ransomware prevention techniques, you need to know a bit … [Read more...] about Top 12 Effective Ransomware Protection Tips
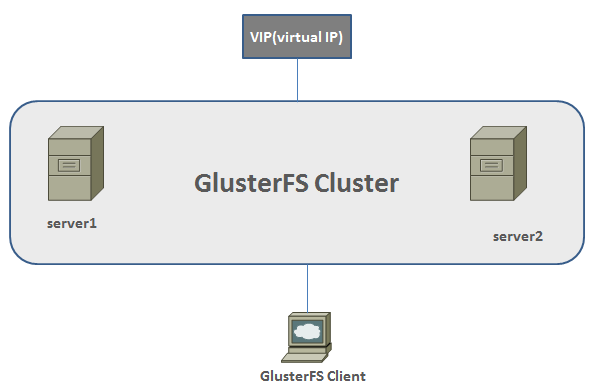
How to Build High Availability Web Server with GlusterFS on Debian
Scenario- this post aims to help you build a high availability cluster for websites using GlusterFS on Debian server. In this installation there will two servers-forming a cluster for web contents- that will replicate each other and the third one will be a client server. If you want to add anything in the cluster you have to add it in the client machine, which will be … [Read more...] about How to Build High Availability Web Server with GlusterFS on Debian
Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
Both children and adults are vulnerable to various types of cybercrimes. If you ever become a victim of such crime you may do a number of things, from reporting to the stop using online activities unless the threat is neutralized, in order to deal with the problem. The ways to deal with cybercrime has been given below: … [Read more...] about Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
11 Symptoms to Identify if Someone has Internet Addiction
Only a handful of research has been undertaken so far about the symptoms of Internet addiction. I have gathered a few major points that may give you a clear signal if someone is addicted to the Internet. You can use the following points as a reference to identify if you, your kids or anyone you care about have fallen victim to the Internet addiction. … [Read more...] about 11 Symptoms to Identify if Someone has Internet Addiction
Top 6 Side Effects and Health Risk of Gaming Addiction for Kids
If you are a parent, it is essential for you to be aware to the consequence of excessive using of computer playing games.This post aims to highlight a number of major issue that may cause harm to your kids if they play video games too long. … [Read more...] about Top 6 Side Effects and Health Risk of Gaming Addiction for Kids
Top 10 Things You Should not Post and Share Online via Social Media
Interesting contents shared in the social media attracts everyone and that is one of the reasons of social media’s popularity. But if you want to stay safe online you need to know which information is not safe sharing on social media and on others websites, forums etc. The following are the list of things you should not share online via social networking websites or any other … [Read more...] about Top 10 Things You Should not Post and Share Online via Social Media
How to Configure Cisco Private VLANs in 4 Easy Steps
Concept of private VLAN A VLAN allows unrestricted traffic flow among the hosts within the VLAN. When a packet is sent from a host to a destination machine within a VLAN, the switch sends that packet only to the destination host machine, not to every other host in the VLAN. But when a broadcast traffic is sent by a host machine, all other hosts in the VLAN receive the … [Read more...] about How to Configure Cisco Private VLANs in 4 Easy Steps
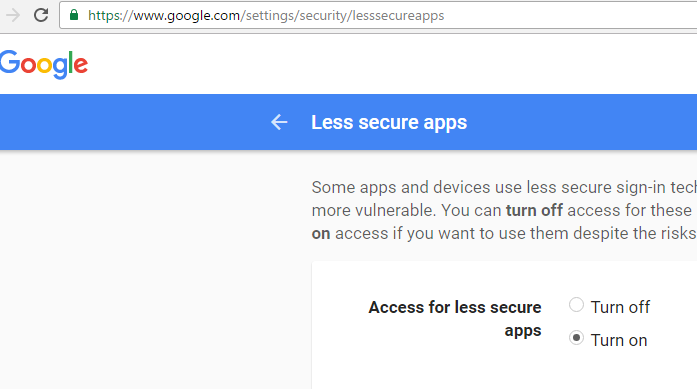
How to setup Gmail SMTP relay to send email from your domain?
Scenario: you have your own domain and have setup an email address in your server using, say, roundcube. Now, you want to send emails using a reliable free third party SMTP relay. What steps you need to follow to use Gmail SMTP? You have to have postfix installed in your server. This post will show you how to configure postfix to use Gmail SMTP relay. But you to … [Read more...] about How to setup Gmail SMTP relay to send email from your domain?
20 Types of Database Security to Defend Against Data Breach
In today’s cyber security, landscape database is considered to be the most important asset of an organization, which holds sensitive information about the business and employees . Having installed and configured firewalls, IDS and end point security, one should not expect that the database is secure and there is no way anyone can breach data. Most of the major data breach … [Read more...] about 20 Types of Database Security to Defend Against Data Breach
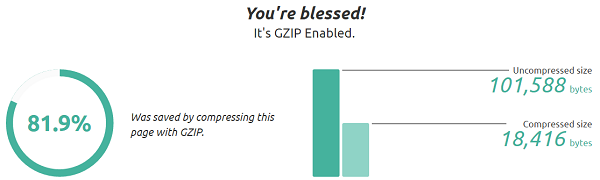
How to Check and Enable Gzip Compression in CentOS for WordPress?
Gzip compression is used to zip or compress webpages in the webserver before serving it to the users’ web browser. Thus it saves network bandwidth because the server sends the compressed form of your webpage over the network. Another advantage of Gzip compression is faster page loading time. When the users’ machines receive the compressed format of webpages, it only takes a few … [Read more...] about How to Check and Enable Gzip Compression in CentOS for WordPress?
5 Open-Source Host Based IDS Software to Detect Intrusion
This post is to help you learn about five effective open-source host-based intrusion detection software.The success of a host-based intrusion detection system depends on how you set the rules to monitor your files integrity. So, while configuring you need to remember that if you do not include the directories that you want to protect, the IDS will not detect anyting and a … [Read more...] about 5 Open-Source Host Based IDS Software to Detect Intrusion