From security perspective, not all types of data of an organization are equally important for successful business operation. Depending on business criticality, some data need to be more secured. The enormous computing power of cloud attracts businesses to put their data in the cloud, but many of the businesses do not have any decisive policy that defines which data to put … [Read more...] about Top 10 Cloud Computing Security Issues
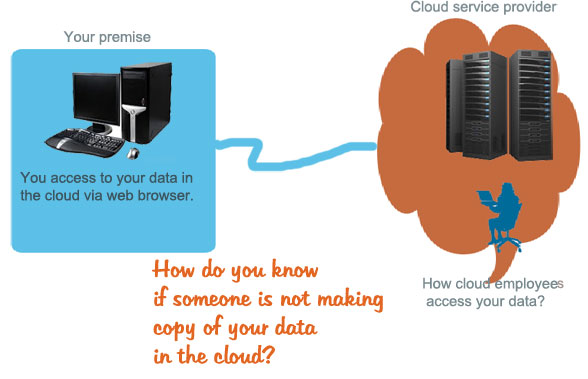
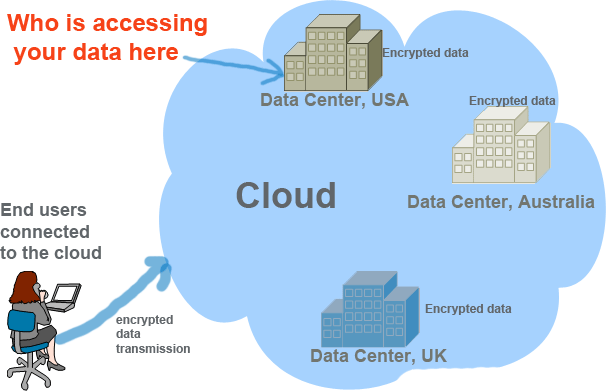
Cloud Privacy Issues and Questions for Users
Though various types of cloud are available to serve various types of customers, they all serve the same purpose-offer IT resources and services to customers accessible via web browser. The hardware and software powering the clouds always stay behind the customer’s eye-thus when we hear the term “cloud” it papers to some of us as an black box. The aim of this post to help you … [Read more...] about Cloud Privacy Issues and Questions for Users
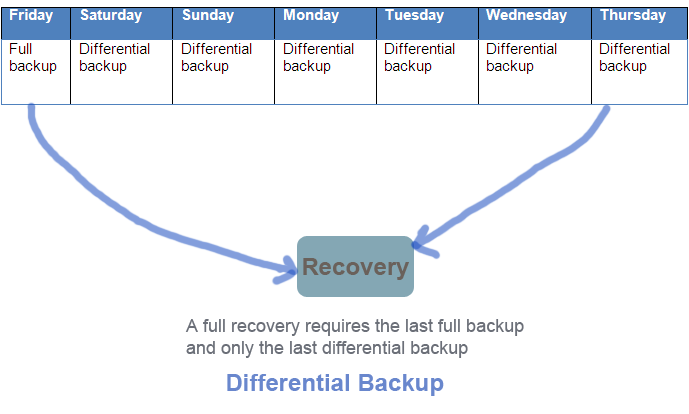
Types of Backup-Difference between full, incremental and differential backup
Data backup gives us a sense of assurance that our data can come back to online no matter what happens to our system. Whether you are a backup administrator or a IT auditor, having a clear understating of the backup types will help you develop a strong backup strategy for your critical data and system files. This post aims to distinguish the difference between the major types … [Read more...] about Types of Backup-Difference between full, incremental and differential backup
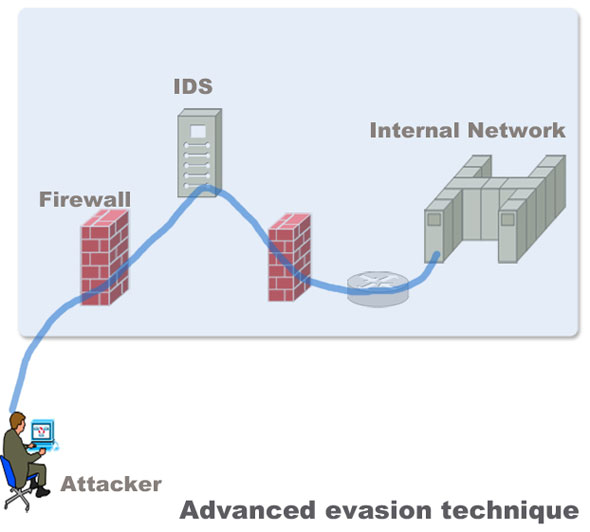
How to Protect Networks against Advanced Evasion Techniques(AET)
Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic. The strings used to evade the devices are not malicious themselves. Their main purpose … [Read more...] about How to Protect Networks against Advanced Evasion Techniques(AET)
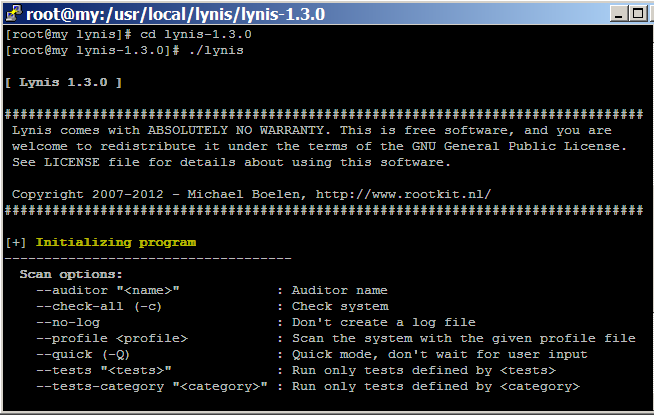
How to audit Linux CentOS Security with Lynis
Hardening Linux security may seem to be a daunting task for new Linux administrator and security auditor if they try to do it manually. Lynis automates the process of Linux security audit, which is widely used by system administrator, IT security auditor and security specialists. When you run Lynis to scan a system, it generates a report and suggestions that helps to patch up … [Read more...] about How to audit Linux CentOS Security with Lynis
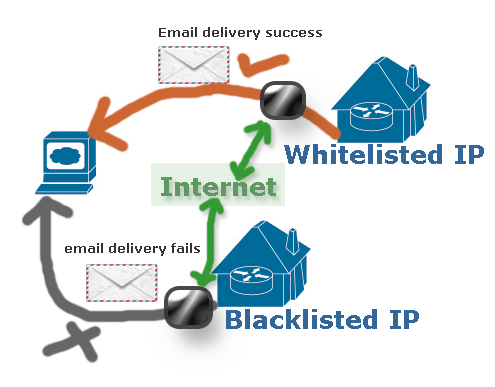
How to Check BlackListed IP of WebServer and Website
The purpose of this post is to show a layman how to check if a IP is in the blacklist of white list. You may need to buy a webhosting plan for your website, and after configuring your site you discovered that your site fails to deliver emails. If that is the case, you need to check if the IP address assigned to your site by your hosting provider is in white list or black … [Read more...] about How to Check BlackListed IP of WebServer and Website
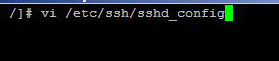
How to Disable Root Login Via SSH in Linux
Having the option of logging in to your server with SSH is essential for some web administrators, but logging in your server with root credentials via SSH is always unsafe. By the word root credentials, I mean that you should not remotely login with your server with root user name, rather use a less privileged user to login to your server and then use the "su" command to login … [Read more...] about How to Disable Root Login Via SSH in Linux
Steps to Check Windows Server Vulnerability with Nexpose Community Edition
There are only a handful of tools for checking Windows server vulnerabilities. If you are familiar with Microsoft security tools testing tools you may have noticed that their tools focus on the security configuration setting of the server. What if your server has a number of applications such as PHP, MySQL or any other database related extension. Rapid7 has a community … [Read more...] about Steps to Check Windows Server Vulnerability with Nexpose Community Edition
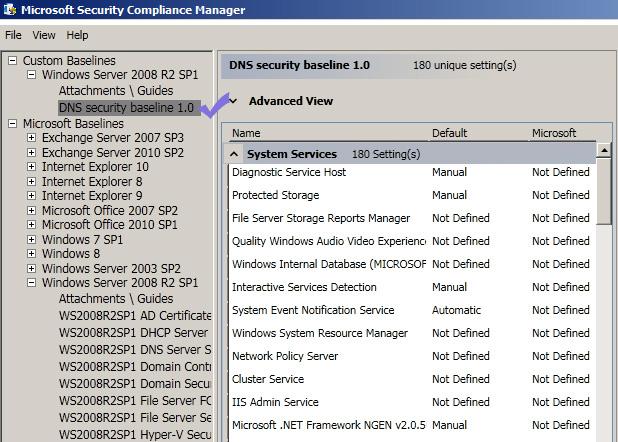
Windows 2008 Server Security Hardening with Automated Tools
One of the quickest and easiest ways to hardening your windows server 2008 r2 security is using automated tools to check the current security status of your server. Once you identify the security loopholes in the server, you can fix those security issues straight away. The good thing is that most of the tools can suggest a list of recommended settings that you need to use to … [Read more...] about Windows 2008 Server Security Hardening with Automated Tools
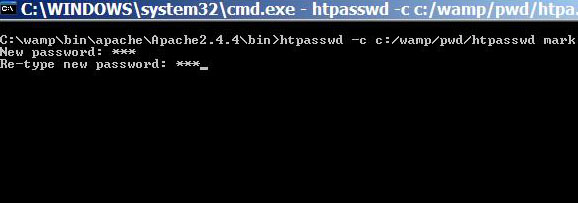
How to Control Directory Access with Htaccess and Htpasswd in Apache
Htaccess file is used to control access to directories in the web server. Normally, website administrators write htaccess file to put appropriate access control to files and pages stored in a specific directory. This method of directory access control is useful when you have a small number of users whom you want to give permission to view your contents. … [Read more...] about How to Control Directory Access with Htaccess and Htpasswd in Apache
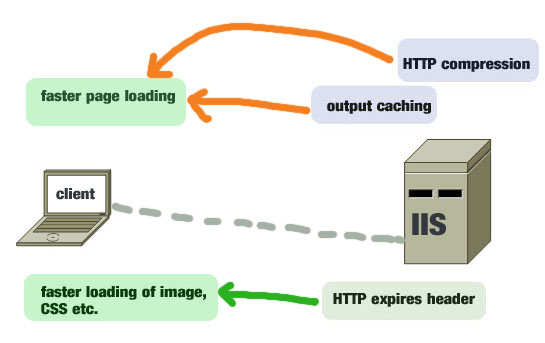
8 Effective Ways to Improve IIS 7.5 Performance
Like any other web servers, IIS 7.5 is capable of running web applications and sites blazing fast when you fine-tune some of its important performance parameters. This post will give you a list of effective methods that can make your Internet information server optimized for serving faster web pages to your users. … [Read more...] about 8 Effective Ways to Improve IIS 7.5 Performance