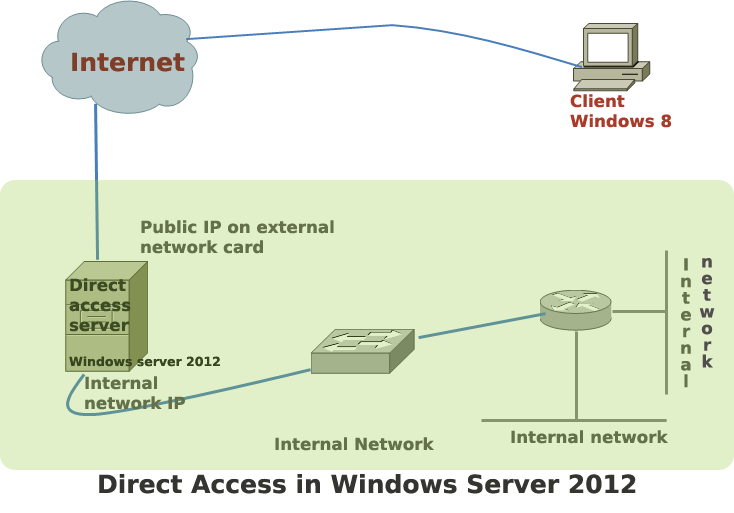
Direct access is the commercial name of Windows 2012 server’s remote access solution. In earlier versions of Windows, remote access offered limited features to the remote users. Windows 2012 is the first Microsoft server that makes remote access users feel like working within the corporate network. This post aims to show you how to install direct access in a Windows 2012 server in order to allow clients to access, and use the internal network from the Internet. Before starting the installation process, you need to meet a number of prerequisites that can be broadly divided into:
- Software requirements.
- Location of the server.
- Creating a GPO to DA clients.
OS and Software requirements
- Windows server 2012: it can be either standard or datacentre edition and the server must be joined to an active directory domain. Although you can install direct access in Windows 2012 essentials, we will not discuss this in this post.
- Client side OS: windows 8 enterprise offers full capabilities for direct access. If you choose to install it in widows 7 ultimate or enterprise edition, you will not be able to enjoy the full functionality of DA such as geographical load balancing.
- In the client machine you will need to download and install direct access connectivity assistant v2 from Microsoft.
Location of direct access server
The server can be in the edge of the network or behind a firewall in a DMZ.
If you want to install direct access in the edge network you need the following:
- Two network cards-one for internal network and another external( for Internet access).
- One IPv4 public IP assigned to the external network card.
- Additional IPv4 public IP to support teredo tunnel. This IP need to be consecutive IP of the first public IP assigned to the external network card. For example, if you assign 211.1.1.1 in the external card, the additional IP should be 211.1.1.2 for teredo. This additional IP should be added to the same external network card using the advanced feature in network connection.
For deploying direct access in the DMZ:
- One public IPv4 address.
- One or two network cards.
- Configure NAT in the border router. If there is any firewall, allow port 443 for https.
Group Policy
Configure a security group policy for client computers that will use the direct access service. For teredo, you need to configure another group policy to allow ICMP for the internal hosts.
If you want to use a self-signed certificate, you do not need to have PKI (public key infrastructure). Remember that if you do not use PKI, you may not use some advanced features such as supporting windows 7 client, two factor authentication, and multisite deployment of direct access.
You also need a dedicated network location server (NLS) if you want to use network load balancing for your host servers.
You need to configure DNS only if you use ISATAP instead of IPv4to6 or teredo.
Configuration Steps for Edge Deployment.
- Make sure your server has already joined an active directory domain.
- Install two network cards in windows 2012-one for internal and the other for external.
- In the internal network card, add the IP address and mask. Do not add any default gateway since you will add a default gateway in the external network card. Also, add the IP of your corporate DNS server in this internal card. If you have more than one subnet in your internal network, which is more likely to have in a large network, you need to add a static route pointing to that subnet. Use the command prompt to configure a default gateway for your internal network.
Route add –p 10.1.1.1 255.255.255.0 192.16.1.1 ( )
Note: 192.16.1.1 is the default gateway for the internal network.
- In the external network card, disable everything except IPv4 and IPv6. Set the public IP, subnet mask and default gateway provided by your ISP. If your ISP does not provide you any DNS information, you do not need to add anything in the DNS settings. Also, disable any DNS and WINS settings from the advanced TCP/IP settings of your external network card. Click on advance in your network setting, and add the additional public IPv4 address to support teredo tunnel.
- Open network connections from control panel and press on the ALT key in your keyboard to the advanced menu visible. Choose advanced from the drop down menu of advanced. Make sure your internal card is listed at the top under “adapters and bindings”. If it is not at the top,take it to the top by clicking the little green arrow.
- Now, go to your DNS server to configure a few things to support both ISATAP and manage-out capabilities. Manage out means you will be able to access the remote computer from your internal network. Open the forward look up zone, and right click on the right side of the panel. Select “New Host (A or AAAA) record”. Type ‘ISATAP’ under host and type IP of the internal network card of the direct access server. Next, click on “add host.”
- Type dnscmd /info /globalqueryblocklist in your power shell in the DNS serve to check if the isatap is in the blocklist. Normally, you will see wpad and isatap in the blocklist. If you see that both isatap and wpad in the blocklist you have to remove isatap from the blocklist by redefining it. To remove isatap from block list type:
Dnscmd /config /globalqueryblocklist wpad
Next,press enter. This will remove isatap from the blocklist and block only wpad.
Now type “nslookup isatap” to see that if your DNS is resolving isatap to your internal ip of DA server.
Allow ICMPv4 to internal host
You need to allow ICMPv4 using group policy object in order to teredo use it. Open group policy management console, and right click on group policy object and click new. Name it and click ok. Now, right click on this new policy and click edit. Select computer configuration>windows settings>security settings> windows firewall>inbound rules. Right click on inbound rules and choose new rules. Click custom and click Next. Again, click on Next. From the protocol type, select icmpv4. Select ‘specific icmp types’ and then select ‘echo request’ and click ok. Click on Next. Select any ip address for both local and remote and click Next. Select ‘allow the connection’ and click Next. Then, select domain, public and private. Finally, name it and click on Finish.
Now, create another inbound rule for ICMPv4 the same way you create the inbound rule for ICMPv4.
Next, right click on the first rule and select advanced and then select allow edge traversal under the edge traversal. Do the same for the second inbound rule.
Link the new policy to the domain.
Create security group in active directory.
- Open active directory users and computers.
- Create a security group.
- Open the new group and select members.
- Click ADD.
- Click object types and select computers.
- Type the client name that will access the direct access.
Configure direct access in the server
Since you have prepared the network for direct access, you can now install the direct access role to your server. The broad process that you have to follow are:
- Install the direct access role in your server
- Restart the server.
- Logon to your server and run the getting started wizard. Select topology information, define a public hostname and change remote clients.
- Configure operation status
- Test direct access connectivity from the client machine.
The detailed procedure for direct access configuration.
- Open the server manager in your direct access server.
- Click on ‘manage’ and select “add roles and features.” Click Next.
- Select “role based or feature based” installation and choose Next.
- Select “select a server from the server pool” and then select the server that you want to install the DA role. Choose ‘Next.’
- Select “remote access” and choose “add features” that are required for remote access. Also, select “include management tools.”
- You will see a list of supporting features that has been selected. You do not have to do anything, just click on Next.
- Select Next.
- Select “DirectAccess and VPN (RAS)” under “Role Services” and choose Next.
- You will be presented with a list of role services. Just click on Next.
- Select “restart the destination server automatically if requested.”
- Click on ‘Install’ to confirm the installation.
Note: after installation the server will restart automatically.
Logon to your server and follow the following steps:
- Add roles and features wizard will pop up automatically. Click on “open the getting started wizard”.
- Select “Deploy direct access only.”
- Select the appropriate network topology such as EDGE. You need to select edge if you server’s external adapter is directly connected to the Internet. Type the FQDN for the public IPv4 address that is set in the external net card of this server. Make sure that this FQDN resolves to the IP of the external IPv4.
- Choose Next and click on ‘here’ to the edit the wizard settings.
- Click ‘change’, which is next to Remote client. By default the DA getting started wizard apply all the settings to all domain computers in a specific domain. Also, it enables DirectAccess for mobile computers only. Click on remove to remove all computers to add only the selected computers. In this example, we are going to add only a single client that will access this server from the Internet. Next, click on ‘ADD’ to add the direct access client that we already linked to our GPO. Also, uncheck “enable DirectAccess for mobile computers only” if you do not want mobile computers to use direct access.
- Click Next.
- Add email address of the helpdesk of your organization.
- Click Finish.
- Ok
- Finish
Wait a few seconds to allow the configuration complete. Check the DirectAccess dashboard to see if there are any missing elements in the configuration. If everything seems OK, logon to your DA server using the client machines to test whether DA is working properly.
To check whether GPO has been applied to the client machine, run the following command in the power shell:
Gpresult /r /scope:computer
Note: rememeber that when you logon to the client machine, it needs to be connected to the internal network so as the GPO can take effects on it.
If the GP result of the above command shows that direct access has been applied properly to the client computer, you can take your computer out of the corporate network and connect it to the Internet to see if it can access the Direct Access server and can use the all the services of your network.