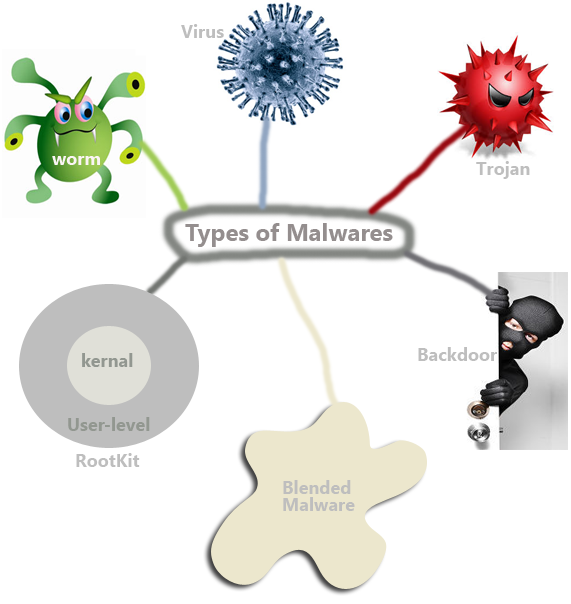
Though malware may take many forms, they have only one purpose to -disturb your computing environment. We can broadly classify malware depending on how the replicate and function. Remember that any codes that have evil intentions can be called a malware. That is why a virus, worm or even a backdoor program can be considered as a malware. But there is a distinct difference between a malware and an exploit that we will discuss in another post.
- Virus– it can replicate itself and can attach to another program. The program to which the virus attaches itself is known as host. And viruses get activated when a user interact with the host program. Normally, a virus cannot update themselves with newer versions released by its creators.
- Worm- you must have heard of Code read, Storm, Blaster or SQL Slammer-all of them is worms. Worms are also self-replicating codes like viruses. The main differnce between viruses and worms is that the later one can self-replicate and propagate without human interaction; some worms can even update its codes. Worms target systems and applications that have well-known vulnerabilities.
- Backdoor-A backdoor is a program that has the ability to bypass a system’s security control, allowing an attacker to access the system stealthily. Backdoors are usually installed by the attackers or by a malware program. Whenever you suspect that you system is compromised you may look for backdoor program because attackers installed this sort of program in a compromised system so as they can access the system remotely.
- Trojan Horse– as the name suggest, the purpose of a Trojan horse is to make a malicious program appear like a legitimate program. Trojan can monitor users’ action, steal users’ data and can open backdoor for the attackers. When you download a well-known open source program from a download site you need to be aware that that piece of software may have a Trojan version as well. For example, tcpdump has a Trojan version as well. So whenever you download tcpdump, make sure you download it from an authentic site.
- User-level Rootkit-This type of malicious code can modify operating systems’ components used by the users. The purpose of user-level rootkit is to give attacker access to the system with administrative or root level privilege. It can successfully hide its presence by modifying the user level component of the OS. Though it can successfully hide its presence from the process lists, it cannot modify the root of the OS.
- Kernel-level Rootkit–It can modify the operating system’s kernel and can intercept system calls while remaining hidden to the users. Kernel-level rootkits are so difficult to detect the even the tools used by investigators cannot detects its presence.
- Blended Malware–Lion and bugbear are great examples of blended malware. This type of malware has the characteristics of several types of malware discussed above. A blended malware can be installed as a Trojan and then it can spread like worms or viruses and open backdoors for the attackers in the victim’s machine.