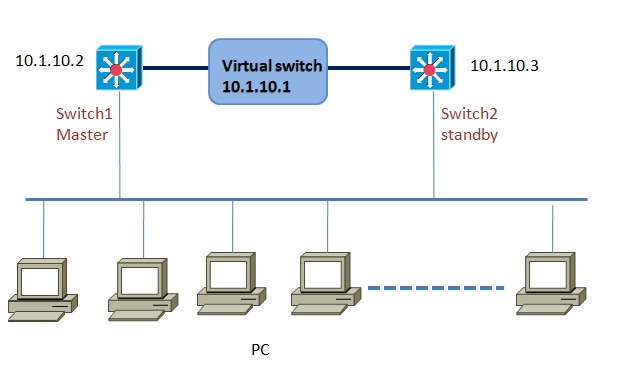
VRRP or virtual router redundancy protocol provides router or switch interfaces failover and failback facility for seamless operation of a network. VRRP almost similar to HSRP in terms of operations and functions, but with a few added features such as VRRP supports up to 255 groups. Just like HSRP, VRRP also support a number of routers to form a virtual group which acts like … [Read more...] about VRRP Configuration(virtual router redundancy protocol)
Network Security Tips
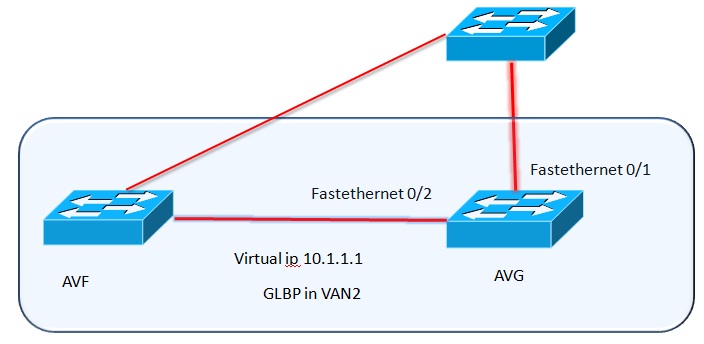
GLBP-Gateway Load Balancing Protocol Configuration
What is GLBP: Gateway Load balancing protocol is a Cisco proprietary protocol for both redundancy and load balancing in Cisco switches and routers. Although VRRP or HSRP provides a network link redundancy to router traffic in a or a number of routers in case of failure to the main active routes, but they do not allow to fully utilizing the available network resources. GLBP … [Read more...] about GLBP-Gateway Load Balancing Protocol Configuration
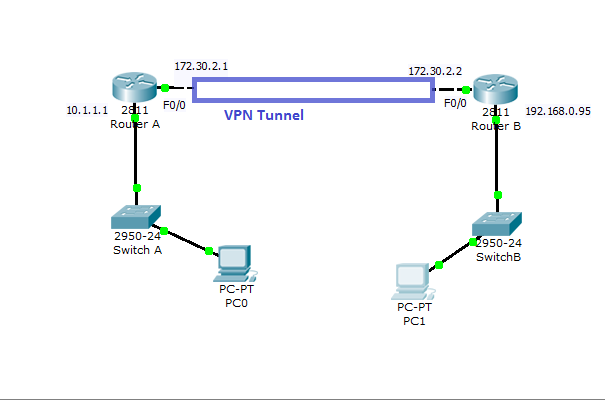
Cisco VPN Configuration in IOS Routers
How to Configure VPN in Cisco Routers Virtual private network can be configured with most of the Cisco routers( 800 to 7500 series) with IOS version 12 or higher.VPN can be implemented in a number of ways--with various level of security measures and configuration. To determine the right VPN configuration for your network, you need to have a solid understanding in cryptographic … [Read more...] about Cisco VPN Configuration in IOS Routers
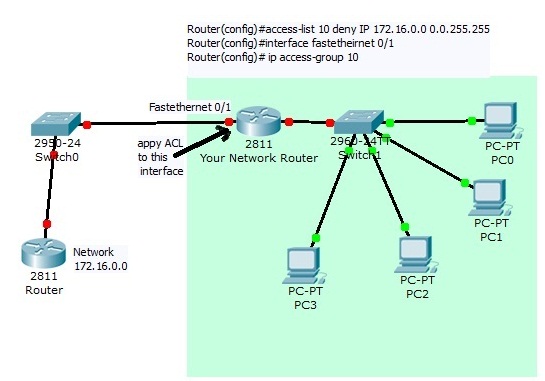
Access Control List Configuration on Cisco Router
What is ACL: Access control list or ACLs are a set of if-then rules set on a router to allow or deny a specific group of IP to send or receive traffic from your network into another network. When you apply an ACL to a route interface for incoming traffic then every incoming packets will be compared with your ACL first, if a match is found then either permit or deny action … [Read more...] about Access Control List Configuration on Cisco Router
Screening Router Security Test
Much small-scale business does not use firewall as their first line of defense any web attacks to their internal network. Instead, they use a router between the Internet and Internal network to control incoming and outgoing traffic flow- this type of use of router is known as screening router. In fact, configuring ACLs inside a router can be a viable and effective solution … [Read more...] about Screening Router Security Test