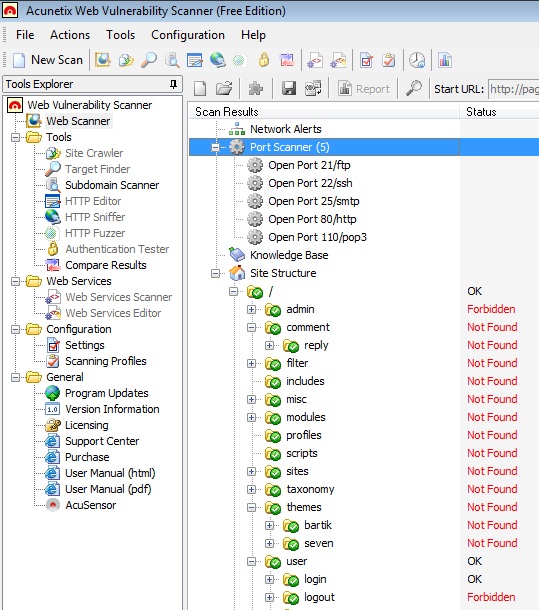
Acunetix web vulnerability scanner help to find vulnerability in a website so as you can make your site or blog as secure as possible. Acunetix has a free version that you can use to find some of the common vulnerabilities of a website.In this article I will show you how you can use the free version of acunetix to figure out how much secure you blog is.Although Acunetix has a … [Read more...] about Acunetix Web Vulnerability Scanner to Detect your Website’s Security Loopholes
Domain Name Registration Law:You cannot Choose any Trademark name
Literally you can buy any domain name that is available for registration. But that does not mean that you can legally have that domain because if there is any trademark registered for that domain name then you have to give it to that company’s owner when they claim for that domain name. Though most of the new companies try to buy a domain name first before choosing their … [Read more...] about Domain Name Registration Law:You cannot Choose any Trademark name
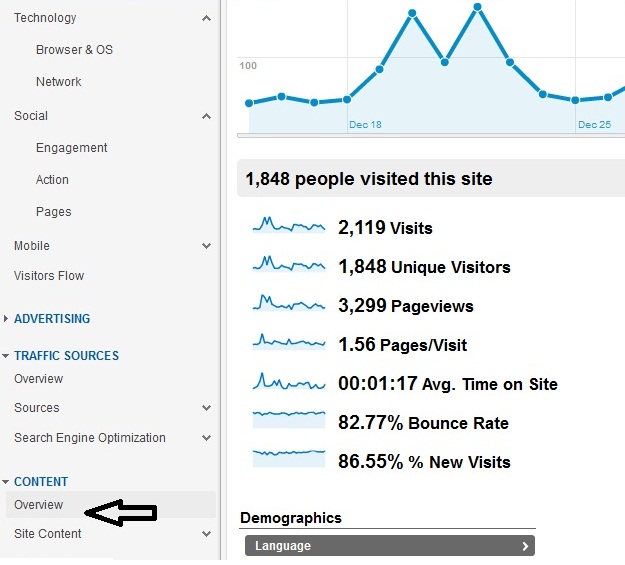
Google Analytics for IT Security Professionals
What is Google Analytics? In short Google analytics is a website statistics tracking tool that you can use to track how your users are interacting with your WebPages such as which pages are being visited the most and where the visitors came from or what keywords he used to find your pages. Who should use Google Analytics? IT professionals( both in operation and security) … [Read more...] about Google Analytics for IT Security Professionals
What are Cookies in Web Browser
What are cookies Cookies are a small piece of software or codes that is used by websites to track its users. When you go to a website for the first time then it send a small file to its user’s computer, which tracks the user’s behavior while they visit a website. … [Read more...] about What are Cookies in Web Browser
WordPress Security Best Practices
With every update, WordPress improves its security capabilities and fix the vulnerabilities. As you know that the default configuration is always risky. To secure a site you always need to customize your security settings, which means apply the best security practices for your blogging platform. If you are a new WordPress user, you might go through a steep learning curve … [Read more...] about WordPress Security Best Practices
What is IDS?Basics of Intrusion Detection Systems
The full form of IDS is: Intrusion Detection System. How many of you have heard about burglary? I guess everyone including children. How the burglar is so successful in intruding men's safe heaven? The answer is when there is no system exists to control the access to your house or office, and then ample of opportunities might arise to misuse or steal your valuable belongings. … [Read more...] about What is IDS?Basics of Intrusion Detection Systems
Identity Theft Protection Explained
What is Identity Theft? You must have heard about ‘impersonation’ or identity fraud-the way one Internet user take on another user’s identity and gain illegal access of another user’s emails or data files. Annually almost 750,000 people are being affected by impersonation-the number one consumer complaint filed with FTC(Federal Trade Commission). The technical name of … [Read more...] about Identity Theft Protection Explained
Cisco Router Security Check for Auditor
Since router is the key to access an organization's network from the outside world, the maximum security priority should be given to routers that are connected to the Internet and to the important application servers. ISO-27001 has already defined standard router security checklist, which any organization can use to improve their router securities. This post aims to … [Read more...] about Cisco Router Security Check for Auditor
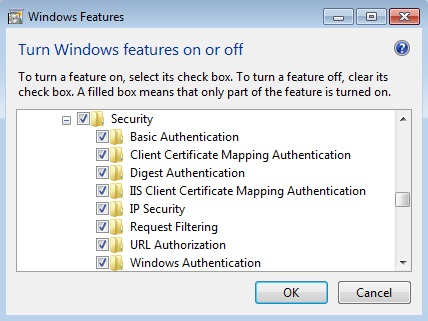
IIS Security Settings
The version of IIS is all about its modules and functions. If you are just learning IIS then before reading this article, it is better to take a closer look at the IIS manger on your server and then go through the following instructions. To secure your IIS server you need to put some extra care to the following settings of IIS server IIS authentication IPv4 and domain … [Read more...] about IIS Security Settings
Active Directory Security Checklists
As you know that in a Windows based domain system, active directory is the central management tool that provides access controls to users to the servers or to use any services offered by any specific servers. So, security in Windows based infrastructure should start with securing the active directory. Though most of the part of securing an active directory process focus on … [Read more...] about Active Directory Security Checklists
Linux Security Basics
The purpose of the Linux security checklist is to help the Linux users, entry-level, to become familiar with the most common security vulnerability of Linux operations systems. As you know security checking needs to be verified against well established practices, the following steps are necessary to following before starting your Linux security checking. Version number of … [Read more...] about Linux Security Basics