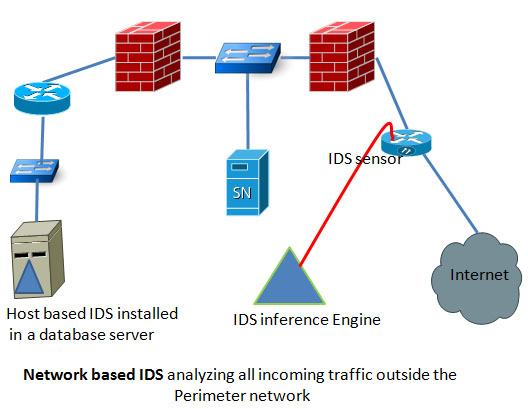
Based on the location in a network, IDS can be categorized into two groups. One is host based IDS and the other is network based IDS. Both have its own advantages and distant ages. Before you decide which IDS suits your network environment the best you need to have a clear concept of both types of IDS.
Network based IDS: these types of IDS are strategically positioned in a network to detect any attack on the hosts of that network. To capture all the data passing through the network, you need to position your IDS at the entry and exit point of data from your network to the outside world. You can also position some IDS near the strategic positions of your internal network, depending on the level of security needed in your network. Since a network based IDS need to monitor all the data passing through the network, it needs to be very fast to analyze the traffic and should drop as little traffic as possible.
Depending on how they function, network based IDS can be divided into two types:
- Statistical anomaly IDS
- Pattern matching IDS
In statistical based IDS model, the IDS try to find out users’ or system’s behavior that seem abnormal. Actually, IDS make a profile of every user and system during the normal operation time. When the deviation of this normal behavior is detected the IDS trigger its alarm for intrusion. One of the main advantages of this type of IDS is that they can detect the type of intrusion that has no records of its previous occurrence. In that sense, statistical anomaly can detect new type of attack patterns. A large number of false alarms are the main problem with this system.
In pattern based system, the IDS maintain a database of known exploits and their attack pattern. During the analysis of network packets if it finds any pattern match to one of those known attack patterns then it triggers alarm. For operation of this type of IDS need to analyze every packet in the network to look for known attack patterns. Since this type of IDS mainly looks for patterns they have a very quick deploy and implementation time, unlike statistical based IDS. Another advantage is that they produce less number of false positives. The main problem with pattern based IDS is that they cannot detect anything that is unknown to them or that of which they have no data in their pattern matching database. Since there are many network based exploits coming on each month, the need to be updated frequently.
Some popular Network based IDS are:
- Real Secure
- SecureNet
- Snort
Host based IDS: they are installed in a host and they can monitor traffics that are originating and coming to that particular hosts only. If there are attacks in any other part of the network, they will not be detected by the host based IDS.. apart from monitoring incoing and outgoing traffic, a host based IDS can also analysis the file system of a host, users’ logon activities, running processes , data integrity etc. some of the advantages of this type of IDS are:
- They are capable of verifying if an attack was successful or not, whereas a network based IDS only give an alert of the attack.
- They can monitor all users’ activities which is not possible in a network based system
- They are capable of identifying attacks that originate from inside the host.
- A host based system can analyze the decrypted traffic to find attack signature-thus giving them the ability to monitor encrypted traffic.
- They do not require any extra hardware since they can be installed in the existing host servers.
- They are cost effective for a small scale network having a few hosts.
The main disadvantages of this system are they can be compromised as soon as the host server is compromised by an attack. In addition, they eat up extra computing power from the host where it resides. They can be ineffective during the denial of service attacks.
Examples of host based IDS:
- PortSentry
There are not straightforward way to decide which type of IDS will work best for your network since both types of IDS has its plus and minus points. You can find that in some cases, deploying both types of IDS can be beneficial such as network based IDS can provide security to your overall network, while you can deploy host based IDS to your hosts with sensitive data.