One of the least prioritize part in data base security is not taking countermeasures against database access. Some solid measures that you can take to secure the access methods in your database are:
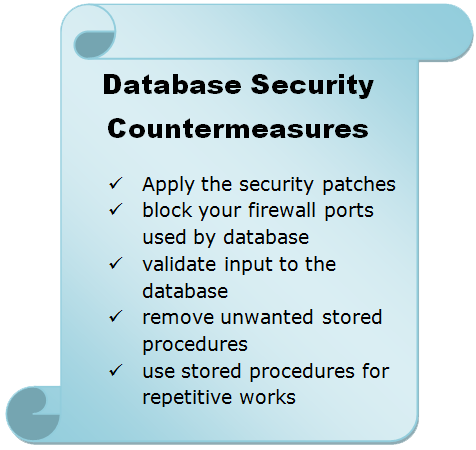
- Whether you use Oracle database or Microsoft SQL database, both the organization releases their security patch almost regular basis. So, make sure that you visit the security patch pages of your vendor’s website and apply the recommended patch as soon as they are released. Remember to test the patch in a test environment before applying in the production environment.
- Always block the well known database ports in your firewalls. Microsoft SQL use UDP port number 1434 and oracle’s listening port is 1521 to 1530. Make sure both the ports are blocked in your firewall if you are using the both Oracle and MS SQL in your networks.
- Input checking is another great way to secure your database. If you have a dynamic site and you allow your users to input data to query your database then you need to check the type of input data. Under any circumstances, you should not allow to input any type of data. First make a rule for input type or data type and then stripped off any unwanted data from the users’ input, which will only send the specified query strings to your database server.
- Stored procedures are a set of SQL statements, which has a unique name and can be used by various programs in order to help the users’ query process. Remove all the unwanted stored producers that do not help you to control users’ access or help to validate data type, including the extended stored procedures.
- If you have to run a similar type of queries frequently, then convert those statements into stored procedures. By doing this you will limit the number of SQL statements in the server side scripts and also reduce the exposure of input data validation attacks.
- Most of the time, database server may not reside on the web server. To process a dynamic query web server need to communicate with the data server. Be sure to make this communication to take place in encrypted format such as using IPSec.
- Another commonly mistake is to allow user unnecessary privileges. Turn off all the default users and give the operators privileges that are necessary to do their job, nothing more.
Finally, never forget to check your log files for unwanted log on attempts on a regular basis and regularly visit the security pages of your product and also try to visit and join forum dedicated to database securities.