Though various types of cloud are available to serve various types of customers, they all serve the same purpose-offer IT resources and services to customers accessible via web browser. The hardware and software powering the clouds always stay behind the customer’s eye-thus when we hear the term “cloud” it papers to some of us as an black box. The aim of this post to help you decide how to choose a cloud service provider, irrespective of the size of your business. The following are the list of questions that you might ask to your cloud vendor:
Data encryption: Cloud data resides in both encrypted format or decrypted format. Service provider should keep your data in encrypted format. Ask your provider if they decrypt data for any reason, if so, then why.
Security key: Do not lease your security key to the your service provider who might ask you do so for cloud backup and deduplication or optimization of your data. so, try to avoid cloud vendor who ask you to give them your security key.
Encryption algorithm: make sure your data is encrypted with AES(advanced encryption standard), which is also recommended by US federal government for classified document. Next, pay attention to how encryption is complied, are they in compliance with NIST FIPS, which is a agency for US department of commerce who provide security framework to legal entities for security and privacy of cloud computing. Ask your cloud vendor that if they comply with NIST FIPS.
Make sure you data are encrypted when it is in your source computer, in transmission as well as when they are in the cloud.
Data monitoring: Ask your cloud provider how they monitor the security of your data? learn about their security monitoring procedures, strategy. Ask them how they respond when they find a potential breach in data.
Networking device management: How they manage their virtual routers and switchers. Some vendor specific router is well known for security break. So, try to learn which networking products and software version they are using, and search in Internet to investigate if that product has any known security vulnerabilities.
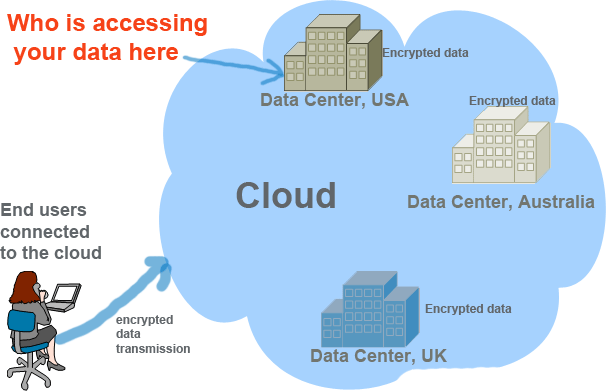
Access to data: Who is accessing your data when they are in the cloud data center? How they control access and at what level?
Physical security: learn about the physical security of the servers? What measures they take to ensure physical security? Ask about the how and who upgrade their server hardware and software? Try to know if they inform their customers when they change hardware or migrate data.
Is the vendor compliance? check If your provider have any of the following certifications?
- SASE 16-compliant
- SAS70 type I and II
- ISO 27001
- FIPS
- HIPPA
Privacy of data against big brother: What your cloud provider do when the governmental agency want access to your data? can they protect your data from them?
Disaster recovery and business continuity: Can they manage to make your data available during the disaster time? In how many location they have cloud data centers? Are their data centers located in the disaster prone areas? What is their guaranteed RTO ( recovery time objective).Test the disaster recovery and business continuity plan with the cloud provider.
Remember that Data centers need to be geographically dispersed in order to keep your data available and safe.
Summary
- Understand the cloud. Not all clouds are created with equal technology and with equal design principles. So, test
- Pay attention to SLA(service level agreement)
- Develop a plan for Testing and auditing your cloud