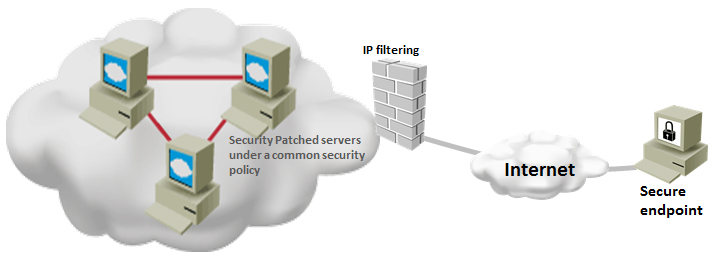
By following windows server security best practices, you can ensure that your server is running under the minimum required security settings. Implementing security best practices does not mean that your systems do not have any vulnerability. But, it gives a sense of security that your system will not be easily compromised and it least will perform better when it has to fight … [Read more...] about Top 20 Windows Server Security Hardening Best Practices
security
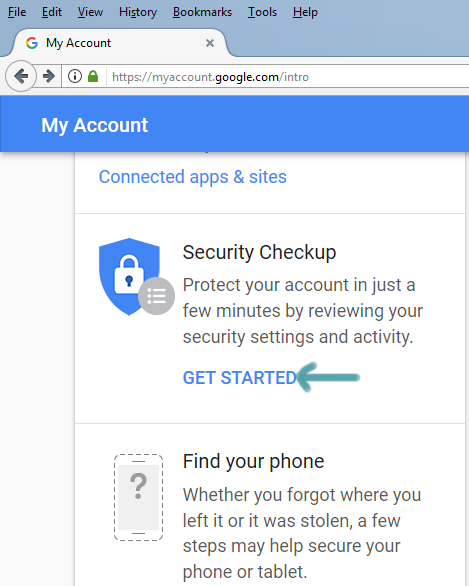
3 Simple Steps to Secure Gmail Account from Hackers
There can be various reasons why hackers want to gain access to your account. Once they gain access to your Gmail account, hackers can use it for various purpose and they post aims to help you secure Gmail account so that you can regain access to your Gmail even if your account password get compromised. … [Read more...] about 3 Simple Steps to Secure Gmail Account from Hackers
20 Types of Database Security to Defend Against Data Breach
In today’s cyber security, landscape database is considered to be the most important asset of an organization, which holds sensitive information about the business and employees . Having installed and configured firewalls, IDS and end point security, one should not expect that the database is secure and there is no way anyone can breach data. Most of the major data breach … [Read more...] about 20 Types of Database Security to Defend Against Data Breach
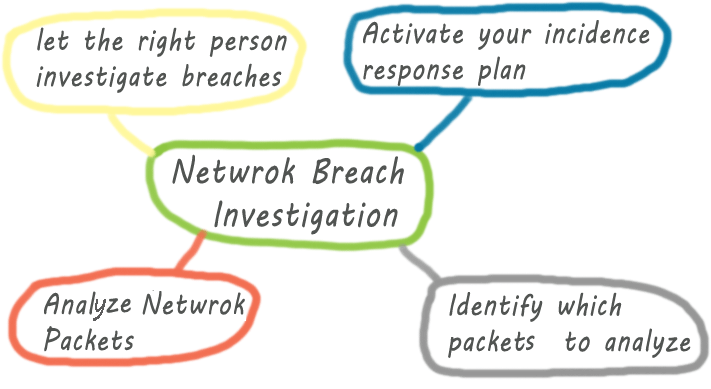
Tips for Network Security Breach Investigation
Investigating network security breach may seem to be a daunting task to someone who has no prior experience of security breach investigation. Like any other IT disciplines, you can handle and investigate network security breach better if you have are well-equipped with the necessary tools and techniques used by the professionals. No matter if you are a network engineer or a … [Read more...] about Tips for Network Security Breach Investigation
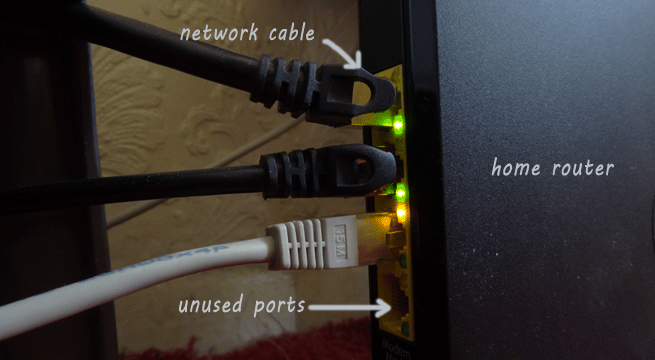
20 Ways to Secure Home Network
Almost every Internet user has their home network that every family member use to Internet access.For your home network security you can follow a few simple steps to eliminate the chances of your network being compromised. Before diving deep into the home network security issues, you may have a look at the vulnerability points in your network, including your client machine. … [Read more...] about 20 Ways to Secure Home Network
Top 15 Network Security Vulnerabilities that System Administrators Must Know
This post aims to help you familiarize with the top 15 commonly known network and system security vulnerablitis. If you are a new administrator, you can have a look at the following list. ACLs on the border router The ACLs you place in your router, especially in the border router, should not allow inadequate access to your other devices connected to your router. A few … [Read more...] about Top 15 Network Security Vulnerabilities that System Administrators Must Know
Top 10 Tips to Prevent Data Exfiltration
What do we mean by data exfiltration? First of all we need to realize that data breach and data exfiltration are two different things. In simple words, data exfiltration means unauthorized transfer of data Your data can be transferred without your knowledge using data exfiltration techniques used by both external and internal actors and tools used by companies. … [Read more...] about Top 10 Tips to Prevent Data Exfiltration
32 Effective Home Security Checklist
Massachusetts Crime Watch has developed a useful home security list that helps to enhance home security. If you are looking for simple tips to make your home safer than before, have a look at the following list. Remember that you do not need to implement all the recommendations. Have a look at the list at first and then decide which recommendation fits your needs. … [Read more...] about 32 Effective Home Security Checklist
Top 10 PHP Security Tips
This is a list of top 10 PHP secuirty tips that you can follow when developing your PHP based web applications. Restrict access to administrative page Most of the web based software have administrative page that is used to configure and to manage the software. When you install PHP based software, remember to change the script’s default directory name and also remove the … [Read more...] about Top 10 PHP Security Tips
32 Proven VOIP Security Best Practices
VOIP saves money if you can deploy and manage it properly, but there are certain risks that you need to take into account. As you know that VOIP is ip based voice solution and IP network is always vulnerable and point of interest to the intruders. … [Read more...] about 32 Proven VOIP Security Best Practices
List of Popular IT Security Standards
The good news for IT security professionals is that there are a number of IT security standards that they can use as a guideline when developing or implementing IT projects. Remember that these standards are well thought out and proven practices that can improve information security goals of your organization. Only the popular and globally recognized IT security standards have … [Read more...] about List of Popular IT Security Standards
63 Web Application Security Checklist for IT Security Auditors and Developers
As you know that every web application becomes vulnerable when they are exposed to the Internet. Fortunately, there are a number of best practices and coutner measures that web developers can utilize when they build their apps. This post will list some proven counter measures that enhance web apps security significantly. … [Read more...] about 63 Web Application Security Checklist for IT Security Auditors and Developers
8 Open Source Web Application Security Testing Tools
Web application security testing might seems intimidating and esoteric to many web administrator, especially to the new ones. Have you ever asked yourself why so many IT professionals ignore the security aspects of the applications? We seem to have a tendency to ignore things that is unperceivable. You become concern when something breaks or any security breach occurs in our IT … [Read more...] about 8 Open Source Web Application Security Testing Tools
Android Security Issues and Prevention
This post about android security intends to give the Android users as holistic view of the phone security. Apps: since android is an open platform and anyone can write apps and publish it in Google apps, the apps itself can contain malicious which may steal data and sensitive tips from your phone. So, when installing any app, try to check if the app has any security issues. … [Read more...] about Android Security Issues and Prevention
Is It Worth Doing Online Master Degree in Information Security?
As online degrees is getting recognised and accepted by the employers, many students prefer to take online courses. If you are from IT background and considering to take an online master degree in IT security, this post may help you determine whether taking online master degree help you achieve your goal. If you put yourself in an employer's shoes and think about recruiting an … [Read more...] about Is It Worth Doing Online Master Degree in Information Security?
Webhosting Security-Best Practices and Concerns
To many IT professionals, webhosting security means protecting websites from hackers and malicious codes. But most of the time we forget to consider that websites security depends on a number of components such as server , application , database, scripts etc. One of the most important aspects of webhost security is to ensure continuous operation and disaster recovery of web … [Read more...] about Webhosting Security-Best Practices and Concerns
Top 10 Cloud Computing Security Issues
From security perspective, not all types of data of an organization are equally important for successful business operation. Depending on business criticality, some data need to be more secured. The enormous computing power of cloud attracts businesses to put their data in the cloud, but many of the businesses do not have any decisive policy that defines which data to put … [Read more...] about Top 10 Cloud Computing Security Issues
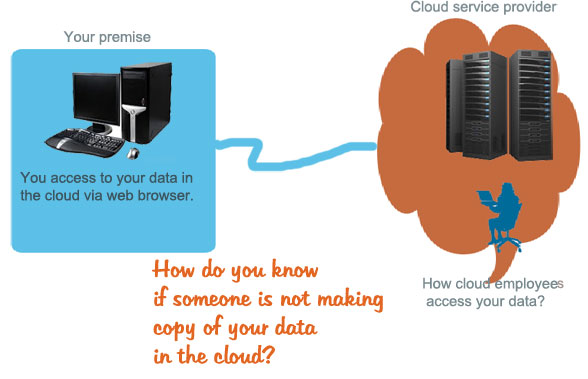
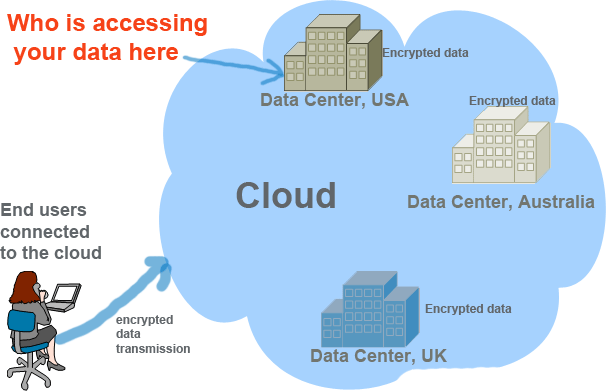
Cloud Privacy Issues and Questions for Users
Though various types of cloud are available to serve various types of customers, they all serve the same purpose-offer IT resources and services to customers accessible via web browser. The hardware and software powering the clouds always stay behind the customer’s eye-thus when we hear the term “cloud” it papers to some of us as an black box. The aim of this post to help you … [Read more...] about Cloud Privacy Issues and Questions for Users
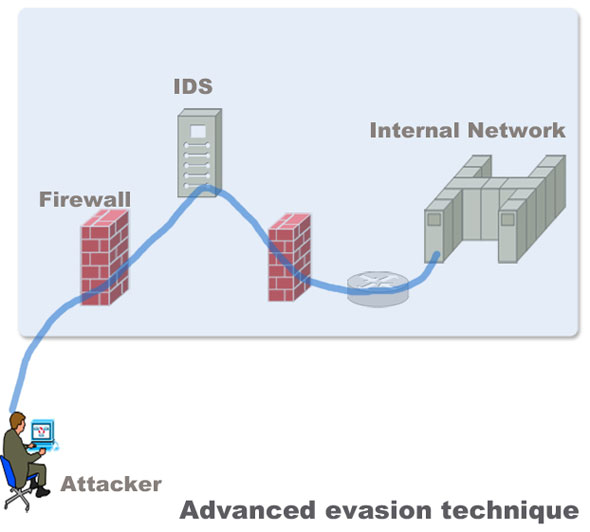
How to Protect Networks against Advanced Evasion Techniques(AET)
Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic. The strings used to evade the devices are not malicious themselves. Their main purpose … [Read more...] about How to Protect Networks against Advanced Evasion Techniques(AET)