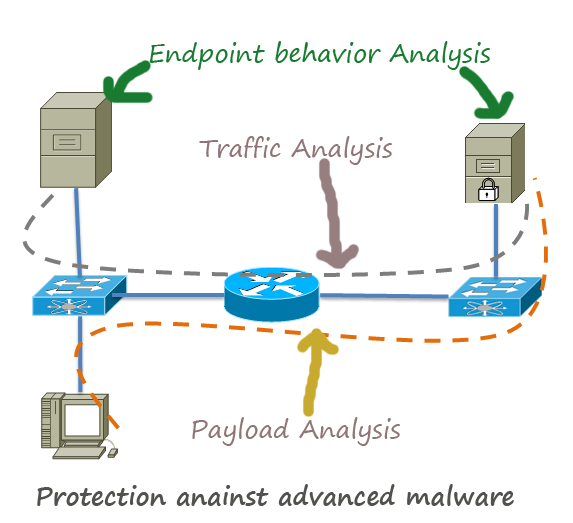
Advanced malwares are extremely stealthy and attack targeted protocols and applications. In most cases, the attackers use these malwares to steal sensitive information from the governmental institutes financial institutes, especially the credit card service providers . Major Concerns about Advanced Malware: They are discovered after the attack has been taken place. So, … [Read more...] about How to Protect Network Against Advanced Malware
protection
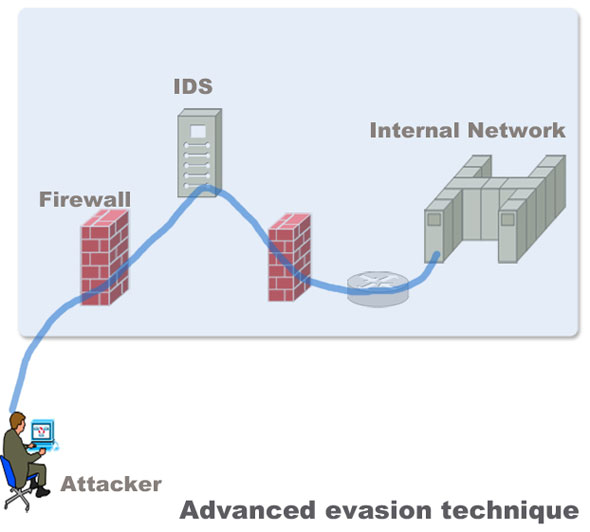
How to Protect Networks against Advanced Evasion Techniques(AET)
Evasion techniques evade the exiting network security devices such as signature based IPS and firewalls to enter the internal network to deliver exploits in servers. Most of the Intrusion detection and prevention system rely on attack signatures to identify malicious strings in the traffic. The strings used to evade the devices are not malicious themselves. Their main purpose … [Read more...] about How to Protect Networks against Advanced Evasion Techniques(AET)
Identity Theft Protection Explained
What is Identity Theft? You must have heard about ‘impersonation’ or identity fraud-the way one Internet user take on another user’s identity and gain illegal access of another user’s emails or data files. Annually almost 750,000 people are being affected by impersonation-the number one consumer complaint filed with FTC(Federal Trade Commission). The technical name of … [Read more...] about Identity Theft Protection Explained