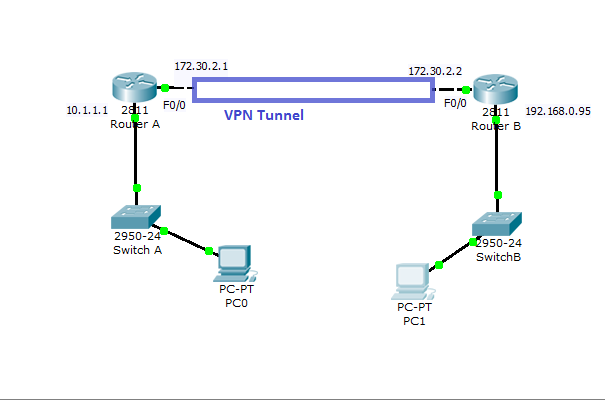
How to Configure VPN in Cisco Routers Virtual private network can be configured with most of the Cisco routers( 800 to 7500 series) with IOS version 12 or higher.VPN can be implemented in a number of ways--with various level of security measures and configuration. To determine the right VPN configuration for your network, you need to have a solid understanding in cryptographic … [Read more...] about Cisco VPN Configuration in IOS Routers
GSM BSC(Base Station Controller)Configuration Guide
How to Configure a base station controller(BSC) in GSM If you are interested to learn how to configure a BSC in a GSM network, then you use this step-by-step BSC configuration process to become familiar with BSC configuration process and procedures. Although this article aims for GSM BSC, but it will help you to get a concrete grasp of BSC configuration in general, … [Read more...] about GSM BSC(Base Station Controller)Configuration Guide
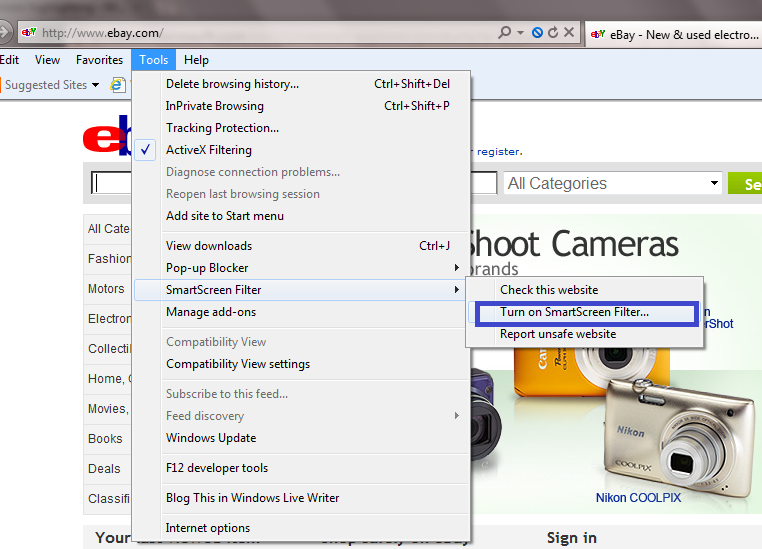
Internet Explorer Security Settings Configuration Guide
The foundation of safer browsing experience depends on how much secure your web browser is. When you install any web browser such as Internet Explorer, you get a default security setting, which may not be suitable for your web privacy and data integrity.This article aims to help you to learn a few useful security tips of Microsoft IE 9. With the new Internet explorer version 9 … [Read more...] about Internet Explorer Security Settings Configuration Guide
Facebook Security Issues| Checklists
Ever since Facebook has become an inevitable part of many of the Internet users, though not all, the cyber criminals are taking the advantage of Facebook users who does pay very little attention about the security of this giant social networking site. One of the most interesting thing is that many of the Face book users even has no knowledge about how much treats or what kind … [Read more...] about Facebook Security Issues| Checklists
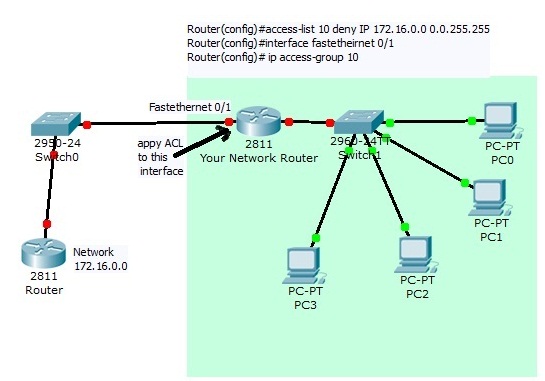
Access Control List Configuration on Cisco Router
What is ACL: Access control list or ACLs are a set of if-then rules set on a router to allow or deny a specific group of IP to send or receive traffic from your network into another network. When you apply an ACL to a route interface for incoming traffic then every incoming packets will be compared with your ACL first, if a match is found then either permit or deny action … [Read more...] about Access Control List Configuration on Cisco Router
Gmail Security Settings Checklist for Secure Login
Whether you are new Gmail User or not, one thing is true that you don’t like to lose your privacy or don’t want to your email security be compromised by any third party or by your business competitors. For making sure that your Gmail account is fully secure and no one is snooping your private emails, you need to follow several steps which are also recommended by Gmail … [Read more...] about Gmail Security Settings Checklist for Secure Login
Computer Security Essentials
The major threats a computer user may expect are – the damage of his stored data or software and stealing of confidential information. A computer can get infected with malicious programs like virus, Trojan, crimeware, spyware, malware or anything else, but the main challenge in front of you is to keep your all the data safe and also to keep your confidential information private … [Read more...] about Computer Security Essentials
CISSP Exam Domains
Computer security is getting more importance day by day due to exponential dependence of information technology. Our institutional education does not deal with how effectively we need to handle information security risk in real world scenario-that is why there are many information security certification course. Among all the most prestigious and recognized courses are CISSP … [Read more...] about CISSP Exam Domains
Screening Router Security Test
Much small-scale business does not use firewall as their first line of defense any web attacks to their internal network. Instead, they use a router between the Internet and Internal network to control incoming and outgoing traffic flow- this type of use of router is known as screening router. In fact, configuring ACLs inside a router can be a viable and effective solution … [Read more...] about Screening Router Security Test
CCNA-Best Networking Exam
CCNA (Cisco certified network associates) routing and switching is the most popular and sought after certification course in the networking industry. It is indeed the best course for anyone looking for entry into the networking area. If one can properly grasp the complete syllabus of CCNA then they should be able to maintain, configure and troubleshooting any small scale to … [Read more...] about CCNA-Best Networking Exam