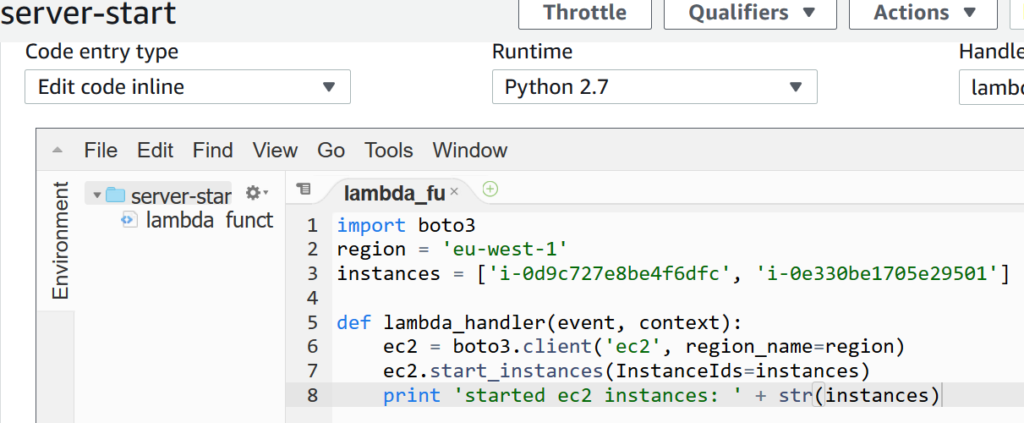
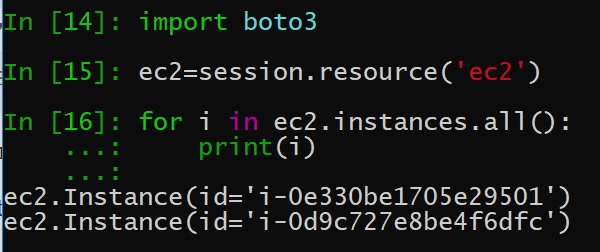
To save your AWS cloud operational cost, you can schedule EC2 instanes' start and stop time using Lambda function. When you define a lamda function, you need to setup a trigger, which specifies the event that can invoke the lambda fucntions. In this post, we will use the a specific UTC time as a trigger . For example, you want to start EC2 instances at 06:30 UTC and want to … [Read more...] about How to Schedule AWS EC2 Start and stop time using Lambda and Cloudwatch
Docker Command List with Examples in Linux
Spinning up a docker container takes a few seconds with a simple command.Once the containers is up and running you need to customize and manage it to fit for the apps and other requirements. I have put together a number of useful command with examples that a beginner will find handy. Docker MySQL container installation commands docker container run -d -p 3306:3306 --name … [Read more...] about Docker Command List with Examples in Linux
How to Install Boto3 for AWS SDK using Anaconda in Windows
Boto3 allows the python developers to create and manage AWS services such as EC2. You may need to install boto3 in your windows machine for AWS cloud based services development and automation. The easiest way to configure boto on your machine is to install anacond at first. You can download anaconda at https://www.anaconda.com/distribution/. … [Read more...] about How to Install Boto3 for AWS SDK using Anaconda in Windows
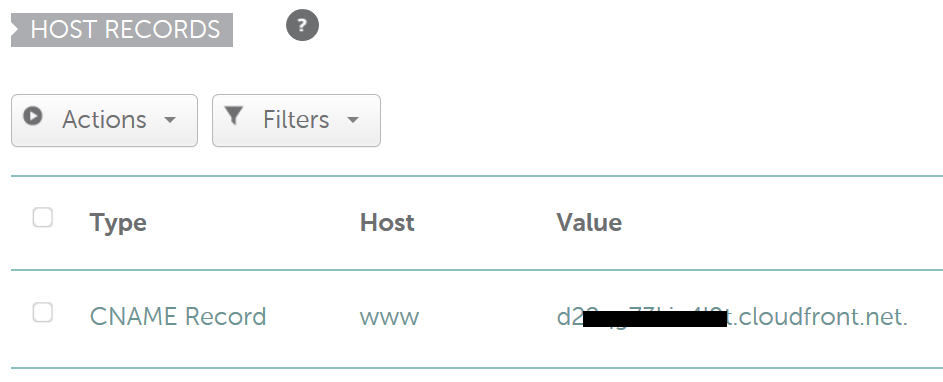
How to Setup AWS CloudFront for Externally Registered Domain Name
If you do not want to transfer your domain to Amazon DNS(Route 53) and want to use AWS CloudFront to deliver your content, you can use the instructions below to set up your content delivery network. Scenario 1: you are using an external DNS for CloudFront and do not want to create a hosted zone in Amazon route 53. For example, your domain is registered with Namecheap and you … [Read more...] about How to Setup AWS CloudFront for Externally Registered Domain Name
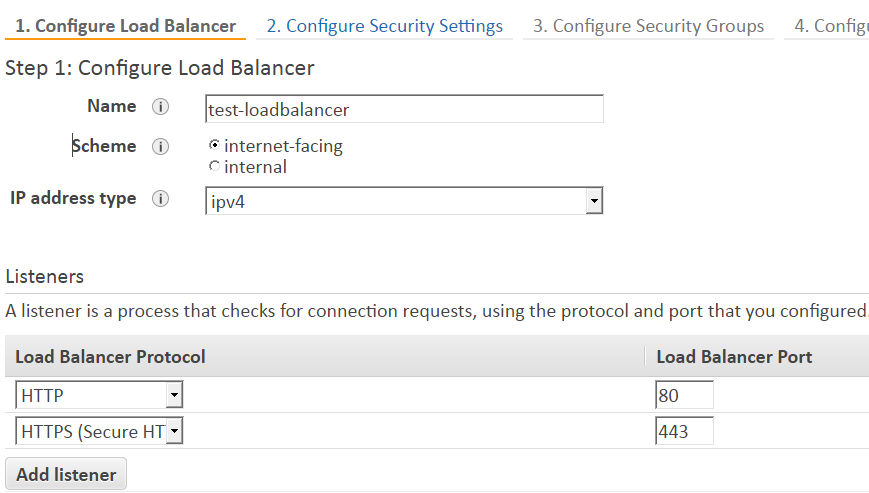
How to Setup SSL in AWS application load balancer for WordPress
How to setup SSL in AWS application load balancer for WordPress. AWS application load balance helps to off load the web server by taking the responsibility of encrypting and decrypting the SSL connection. To implement SSL in WordPress you need to apply the SSL certification only on the load balancer. However, you still need to add the certificate in the server if you want … [Read more...] about How to Setup SSL in AWS application load balancer for WordPress
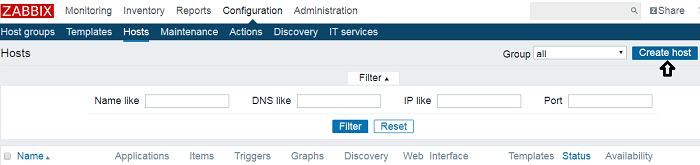
How to Configure SNMP in Zabbix Server (Debian) to monitor Cisco Switches
To monitor SNMP(simple network management protocol) enabled cisco switches and routers in Zabbix server, you need to configure the server for SNMP. In this post, I have used a Debian 8 server running zabbix and setup SNMP in a cisco switch for monitoring its interfaces and bandwidth. The configuration will be in three parts. In the first step, we will install SNMP on the … [Read more...] about How to Configure SNMP in Zabbix Server (Debian) to monitor Cisco Switches
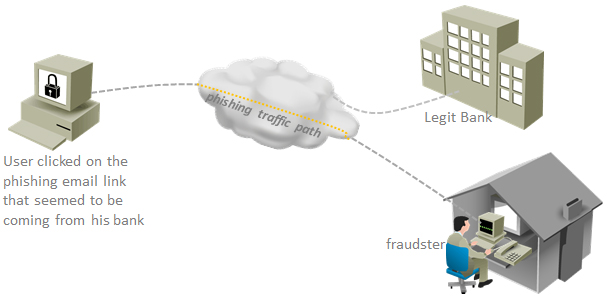
5 Ways to Prevent Online Banking Fraud
If you are a frequent user of online banking, you may take a few necessary steps to protect against online banking fraud. Online banking fraud is all about gaining access to your online bank account by stealing sensitive information. The most important element to protect your online account is to become aware of the ways your account information may fall into the hand of the … [Read more...] about 5 Ways to Prevent Online Banking Fraud
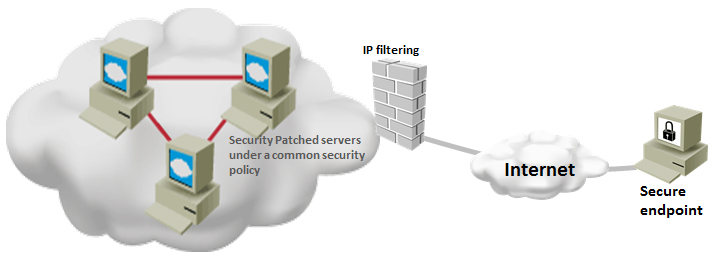
Top 20 Windows Server Security Hardening Best Practices
By following windows server security best practices, you can ensure that your server is running under the minimum required security settings. Implementing security best practices does not mean that your systems do not have any vulnerability. But, it gives a sense of security that your system will not be easily compromised and it least will perform better when it has to fight … [Read more...] about Top 20 Windows Server Security Hardening Best Practices
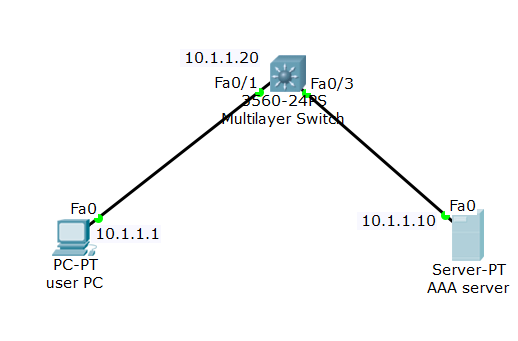
How to Configure AAA (TACACS+) on Packet Tracer for User Authentication
AAA functionality in Cisco switch can be used as a centralized solution to secure and control user access to switches. Cisco switches are capable of implementing AAA functionality with either TACACS+ protocol (Cisco proprietary) or RADIUS protocol. To use AAA you need to enable it and then connect it to an AAA service hosted in a server. … [Read more...] about How to Configure AAA (TACACS+) on Packet Tracer for User Authentication
3 Simple Steps to Secure Gmail Account from Hackers
There can be various reasons why hackers want to gain access to your account. Once they gain access to your Gmail account, hackers can use it for various purpose and they post aims to help you secure Gmail account so that you can regain access to your Gmail even if your account password get compromised. … [Read more...] about 3 Simple Steps to Secure Gmail Account from Hackers
Top 12 Effective Ransomware Protection Tips
What is ransomware? Ransomware belongs to the family of malware used to take control of users’ machines and the users get back control of the machine when the victim pays a ransom to the attackers. There are a number of preventive steps that a user can take to avoid ransomware attacks. But before delving depth into the ransomware prevention techniques, you need to know a bit … [Read more...] about Top 12 Effective Ransomware Protection Tips