When you write a simple program, for example, to print user name with greetings. For this program to run you assign character string 38 in the following way
Char name (38)
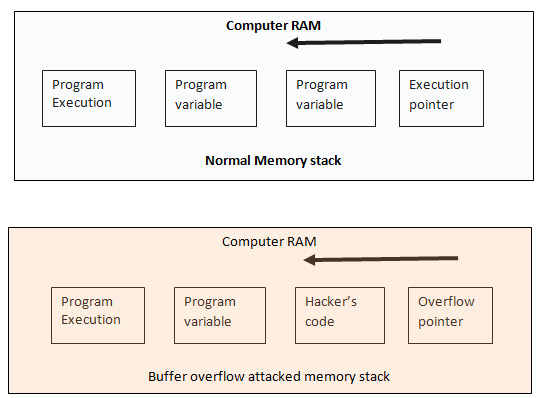
Here “name” is the variable name. The above code specifies that you name or users’ input would not be more than 38 characters long because you have already assigned only 38 bit of data into the buffer. So, buffer overflow is such type of attack where the buffer memory is bombarded with more data than it can actually handle.
There are two types of buffer overflow attacks:
- Stack based
- Heap based
A stack or heap is used to store users input until a program needs it to run an application. For storing data in static memory stacks are used whereas for storing dynamic data heaps memory is used. In a buffer overflow attack a perpetrator send a large amount of data to exhaust the storing capacity of stack memory. This is done with the help of a malicious program, which can be a pre-written codes or exploits.
What can be done to protect a system against buffer overflow?
- First of all, you need to remember that buffer overflow occurs due to poor coding practices or programming vulnerabilities. So, you make sure that the source code of your application does not have any inherent vulnerability.
- One of the common reasons for this type of attack is the lack of input validation. Before sending the data to the memory a program should sanitization the data by making sure that the length and format of the input satisfy the requirements of the input declared by the program. An example of input validation is website’s feedback or contact form, where the input must meet the criteria specified by the programs; users should not be allowed to send data of any length and any format.
- Programmers should avoid using built-in functions such as strcpy (), strcat (), which are prone to butter overflow attacks.
- If possible you can use JAVA to replaces the use of C/C++ because JAVA cannot be exploited by buffer overflow attack.
- Whenever possible remove the cmd.exe, ftp.exe and tftp.exe from your operating systems. If you need to keep those executable files for a specific purpose then restrict their usage with access control list.
- Isolate core JAVA servlets from the application servlets in JAVA application servers. If you place the core servlets with the application servlets in the same physical place, an attacker can use the servlets invoker to invoker.
- If there are servlets that are physically present in your server, but are not registered then remove them or do not let them to be executed.
- Always disable the direct invocation of application servlets by not mapping your servlets with URL because they are capable of invoking any arbitrary servlets.
- Normally, JAVA application servers are shipped with many unnecessary example servlets. If you JAVA machines has such servlets then simply unregistered them as a counter measure to buffer overflow attacks.