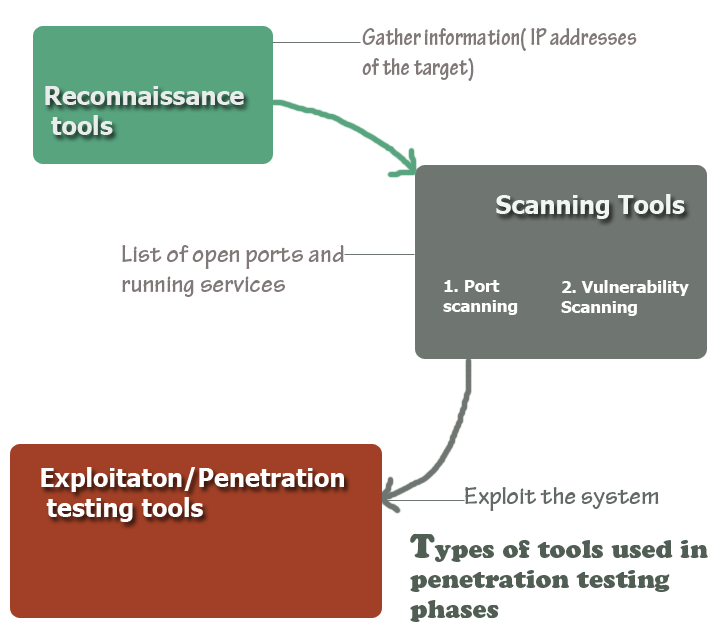
In footprinting or reconnaissance phase, a penetration tester collects as much information as possible about the target machine. The primary purpose of this phase is to gather intelligence so as you can conduct an effective penetration test. At the end of his phase, you are expected to have a list of IP of your target machine that you can scan later on.
Reconnaissance /footprinting tools
Reconnaissance can be either active or passive. In active reconnaissance you send traffic to the target machine while a passive reconnaissance use Internet to gather information. When you use active reconnaissance, you need to remember that the target machine may notice that you are planning a penetration test. In the case of passive test, target machine has no clue about who is gather intelligence and planning an attack. The following are the tools you can use:
- Google: use advanced Google search to gather information about the target’s website, webservers and vulnerable information. Sometimes, jobs posted in the companies’ websites reveal valuable information about the type of information technologies used in the target company.
- The harvester: you can use it to catalogue email address and subdomains. It works with all the major search engines including Bing and Google. This is a build in tool of Kali Linux.
- WHOIS: to get information about domains, IP address, DNS you can run whois command from your Linux machine. Just type whois followed by the domain name:
Whois yourdomain.com
Alternatively, you can visit whois.net and type the domain name of your target.
- Netcraft: they have a free online tool to gather information about webservers including both the client and server side technologies. Visit http://toolbar.netcraft.com/site_report/ and type the domain name.
- Nslookup: you can use it to query DNS server in order to extract valuable information about the host machine. You can use this tool both in Linux and Windows. From your windows machine, open the command prompt and the type ‘nslookup’ followed by the domain name.
- Dig: another useful DNS lookup tool used in Linux machine. Type dig followed by the domain name.
- MetaGoofil: it’s a meta data collection tool. Meta data means data about data. For instance, when you create word document in Microsoft word, some additional information are added to this word file such as file size, date of creation, the user name of the creator etc.-all these additional information is called meta data. MetaGoogle scours the Internet for metadata of your target. You can use it with both Linux (built in Kali Linux) and Windows.
- Threatagent drone: it is a web based tool. You need to signup at https://www.threatagent.com/ and type the domain name that you want to reconnaissance. Once the drone extracts all the information about your target, it will create a complete report about the target, which will include the IP address range, email address, point of contacts etc.
- Social engineering: it is perhaps the easiest way to gather information about an organization. You can find lots of free information about social engineering in the Internet. Depending on the types of information you need about your target organization, you need to choose the appropriate technique. But remember that this technique needs time to master and you need to plan it very carefully, otherwise your activity can easily trigger an alert.
After gathering solid information about the target, the next step is to start scanning the target system.
Scanning Tools
A pen tester scans the target machine in order to find the weakness in the systems. The two major activities of the scanning phase are port scanning and vulnerability scanning.
Port scanning helps to identify a list of opened ports in the target and based on the list of ports you can determine what types of services are running in the system.
The second step in scanning is to run a vulnerability scan to identify specific weakness in the software and services running in the servers.
At the end of port scan you will have the following information:
- Number and type of opened ports
- Type of services running in the servers
- Vulnerabilities of the services and software
10. Nmap
If you have doubt about which tool to use for scanning, use Nmap. This tool creates a complete list of opened ports in your target. You can use is both in Windows and Linux environment. The graphical interface for Windows is called Zenmap, which you can run without learning any command. But, for greater control and granularity for the output, you need to learn the commands.
11. Nessus
Once you find the list of open ports, the next step is start looking for vulnerability in the servers. One of the efficient tools to vulnerability scan is Nessus. Remember that Nessus is not a free tool.
12. Nexpose: if you are looking for a free vulnerability scanner, you can use nexpose community edition from rapid7.
Penetration testing/exploitation
This is the most important phase of a penetration test, which is also known as exploitation because a pen tester makes real attempts to gain access to the target system at this phase.
13. MEDUSA: you can use it to gain to the authentication services in the target machine. Medusa can authenticates with a number of popular services such as FTP, HTTP, IMAP, MS SQL, MySQL, PCAnywhere, POP3, RLOGIN, SMTPM, Telnet, SSH, VNC etc. before using Medusa you need to have several information in your hand such as username, target IP address, a password file( a dictionary file containing a list of popular and widely used passwords).
14. Hydra: this is another useful tool like Medusa used to break authentication system.
15. Metasploit: it can be considered one of the finest open source exploit in the world. The best thing about Metasploit is that it is free. If you are planning to become an open tester and what to learn exploitation, you can start using metasploit without any hesitation. But remember that exploitation tools are not vulnerability scanner. When you use a vulnerability scan, it will report you about the weakness in the system without causing any damage in the system. In that sense, a vulnerability scanner in a passive tool. On the other hand, an exploitation tool like Metasploit is a real exploit. When an exploitation tool discovers any vulnerability, it exploits it immediately, which may cause severe damage to the system or can cause network disruption. So, take extra care when playing with any such tools.
Words of Caution: never try to use the above mentioned tools in a network or system without authorization from the proper authority. The intention of the post is to help the IT professional who also wants to learn and develop a career in penetration testing.