Social media platforms have evolved into central hubs for communication, entertainment, information dissemination, and commerce, impacting billions of lives globally. However, this influence comes with significant responsibilities and challenges that necessitate governance in several key areas: … [Read more...] about Beyond Likes and Shares: Critical Governance Issues in Social Media
Internet Security and Safety
Top Youtube Channels Championing Media Decency and Promoting Good Behavior Online
Welcome to our review on YouTube channels dedicated to media decency and good behavior. In today's digital age, where content can influence thoughts and actions, these channels stand out by promoting ethical media consumption and encouraging positive conduct online. We'll explore which creators are leading the way in fostering a community of respect, integrity, and media … [Read more...] about Top Youtube Channels Championing Media Decency and Promoting Good Behavior Online
Top 10 Paid Email Services to Protect Your Privacy and Secure Your Messages
A paid and secure email service offers enhanced privacy and security features not typically found in free email providers. These services often include end-to-end encryption, zero-access encryption, and no data logging, ensuring that only the sender and recipient can read the messages. They provide protection against surveillance and data breaches. Providers like ProtonMail, … [Read more...] about Top 10 Paid Email Services to Protect Your Privacy and Secure Your Messages
NIST 800-53 Simplified: Key Takeaways and Summary
NIST Special Publication 800-53, "Security and Privacy Controls for Federal Information Systems and Organizations," provides a catalogue of security and privacy controls for all U.S. federal information systems except those related to national security. Here's a summary: … [Read more...] about NIST 800-53 Simplified: Key Takeaways and Summary
9 Types of Digital Security Risks
Having an overall understanding of the existing digital security risk can help to design a decisive risk mitigation plan. Both small and large businesses are exposed to similar types of digital risk, which can cause serious damage to businesses unless handled carefully. The list below explains the nine types of digital risks you need to stay alert of. 1. Data risk- as you … [Read more...] about 9 Types of Digital Security Risks
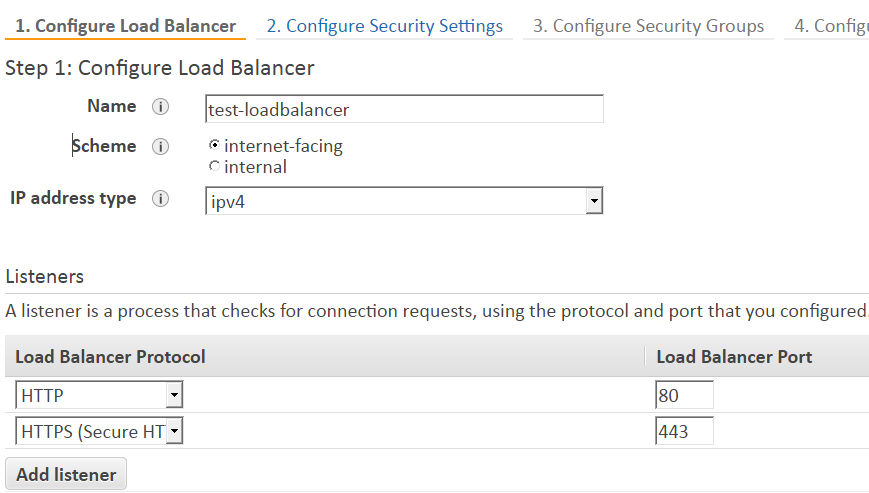
How to Setup SSL in AWS application load balancer for WordPress
How to setup SSL in AWS application load balancer for WordPress. AWS application load balance helps to off load the web server by taking the responsibility of encrypting and decrypting the SSL connection. To implement SSL in WordPress you need to apply the SSL certification only on the load balancer. However, you still need to add the certificate in the server if you want … [Read more...] about How to Setup SSL in AWS application load balancer for WordPress
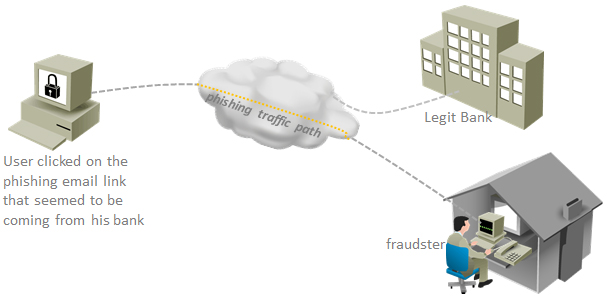
5 Ways to Prevent Online Banking Fraud
If you are a frequent user of online banking, you may take a few necessary steps to protect against online banking fraud. Online banking fraud is all about gaining access to your online bank account by stealing sensitive information. The most important element to protect your online account is to become aware of the ways your account information may fall into the hand of the … [Read more...] about 5 Ways to Prevent Online Banking Fraud
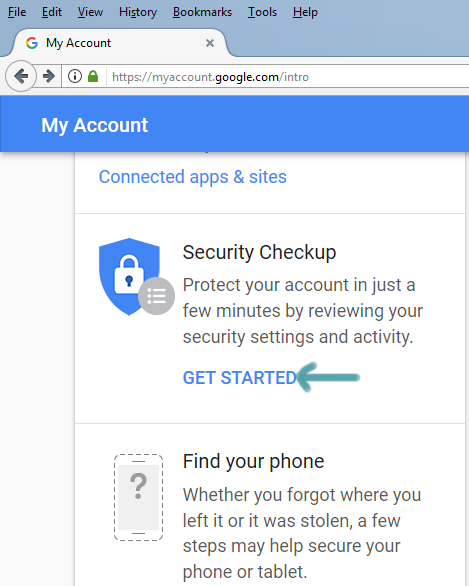
3 Simple Steps to Secure Gmail Account from Hackers
There can be various reasons why hackers want to gain access to your account. Once they gain access to your Gmail account, hackers can use it for various purpose and they post aims to help you secure Gmail account so that you can regain access to your Gmail even if your account password get compromised. … [Read more...] about 3 Simple Steps to Secure Gmail Account from Hackers
Top 12 Effective Ransomware Protection Tips
What is ransomware? Ransomware belongs to the family of malware used to take control of users’ machines and the users get back control of the machine when the victim pays a ransom to the attackers. There are a number of preventive steps that a user can take to avoid ransomware attacks. But before delving depth into the ransomware prevention techniques, you need to know a bit … [Read more...] about Top 12 Effective Ransomware Protection Tips
Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
Both children and adults are vulnerable to various types of cybercrimes. If you ever become a victim of such crime you may do a number of things, from reporting to the stop using online activities unless the threat is neutralized, in order to deal with the problem. The ways to deal with cybercrime has been given below: … [Read more...] about Top 5 Tips Dealing with Cyberbullying/Cyberstalking and Cybercrime
11 Symptoms to Identify if Someone has Internet Addiction
Only a handful of research has been undertaken so far about the symptoms of Internet addiction. I have gathered a few major points that may give you a clear signal if someone is addicted to the Internet. You can use the following points as a reference to identify if you, your kids or anyone you care about have fallen victim to the Internet addiction. … [Read more...] about 11 Symptoms to Identify if Someone has Internet Addiction