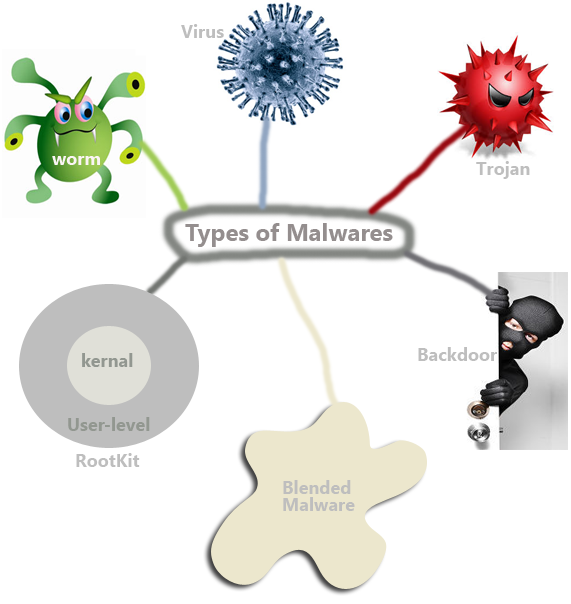
Though malware may take many forms, they have only one purpose to -disturb your computing environment. We can broadly classify malware depending on how the replicate and function. Remember that any codes that have evil intentions can be called a malware. That is why a virus, worm or even a backdoor program can be considered as a malware. But there is a distinct difference … [Read more...] about Definition of 7 Types of Malware
Top Antivirus Buying Tips for Home Users
Just like the viruses, antivirus software is also very competitive. There are fierce battle among the premium antivirus makers such as Norton, Kaspersky, McAfee, Trend Micro system, Bit defender and a few more to increase their market share. People easily get caught up when they decide to buy a premium antivirus because they cannot differentiate between two vendors. … [Read more...] about Top Antivirus Buying Tips for Home Users
32 Effective Home Security Checklist
Massachusetts Crime Watch has developed a useful home security list that helps to enhance home security. If you are looking for simple tips to make your home safer than before, have a look at the following list. Remember that you do not need to implement all the recommendations. Have a look at the list at first and then decide which recommendation fits your needs. … [Read more...] about 32 Effective Home Security Checklist
10 Major Types of DDoS Attacks and Prevention
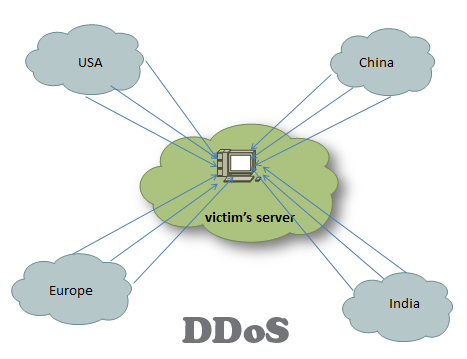
Despite the differences in the mechanism, the purpose of the DDoS (distributed denial of service attack) is the same- to deplete the resources on the victim’s network. DDoS can be broadly divided into two types: bandwidth depletion and resource depletion. This post aims to give you a broad overview of the various types of DDoS attacks and their prevention techniques. … [Read more...] about 10 Major Types of DDoS Attacks and Prevention
15 Ways to Stop DDoS Attacks in your Network
To stop DDoS (distributed denial of service) attack, one needs to have a clear understanding of what happens when an attack takes place. In short, a DDoS attack can be accomplished by exploiting vulnerabilities in the server or by consuming server resources (for example, memory, hard disk, and so forth). … [Read more...] about 15 Ways to Stop DDoS Attacks in your Network
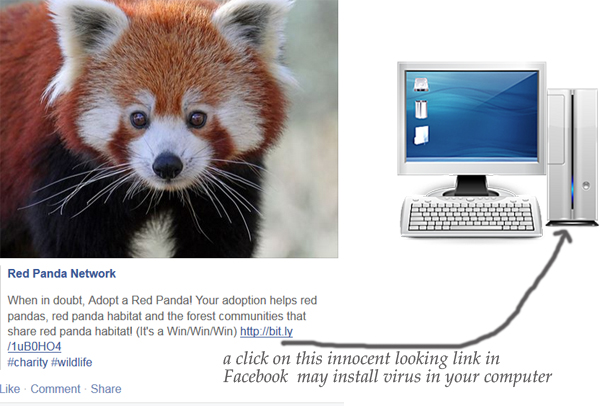
How to Remove Annoying Facebook Virus
What is Facebook virus?Facebook virus is just like any other virus that gets installed in a computer when a user clicks on a link shared from his friends’ news feeds or shares. So, the two most common ways that can infect your computer from Facebook viruses are: … [Read more...] about How to Remove Annoying Facebook Virus
How to Respond to Network Intrusion Detection
When your intrusion detection system triggers an intrusion alarm, you need to respond quickly to minimize the effects of the intrusion. The longer it takes to respond the higher the chances that your system will be damaged severely. If you do not have proper plan and concepts of what you have to do when you detect or suspect an intrusion, you will only panic for nothing and … [Read more...] about How to Respond to Network Intrusion Detection
Top 10 PHP Security Tips
This is a list of top 10 PHP secuirty tips that you can follow when developing your PHP based web applications. Restrict access to administrative page Most of the web based software have administrative page that is used to configure and to manage the software. When you install PHP based software, remember to change the script’s default directory name and also remove the … [Read more...] about Top 10 PHP Security Tips
How to Create SSH key login with PuTTY in Windows
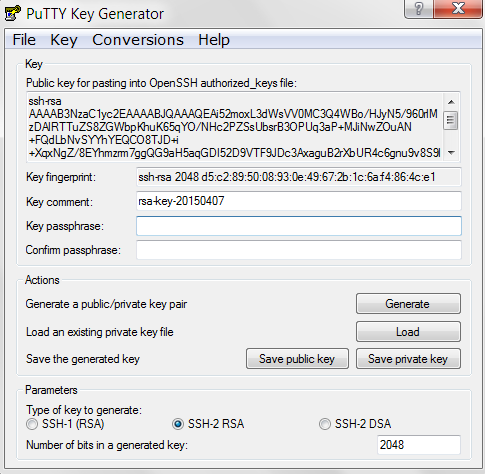
Though it is always possible to login in your server using username and password, but you always remain vulnerable to brute force attack. You will always feel that someone may break your password and get privileged access to your server. Are there any better ways to make your server access more secure? The answer is positive. You can make your server access more secure by … [Read more...] about How to Create SSH key login with PuTTY in Windows
Top 10 Ways to Prevent Data Leak
Who wants to lose his sensitive and confidential data? The answer is everybody wants to avoid embarrassing situation and to keep his data safe. Fortunately, you can avoid losing your data by following a few tips. What you have to do it to remember the following tips by reading it 38 times. Yes you heard it right. … [Read more...] about Top 10 Ways to Prevent Data Leak
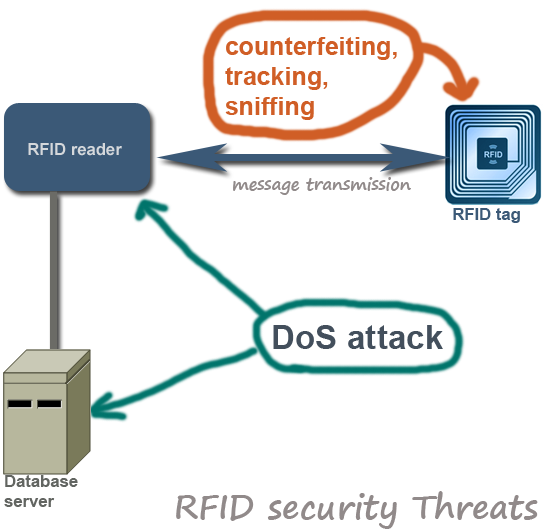
Top 10 RFID Security Concerns and Threats
Like any other security devices and mechanism RFID is not flawless. Despite its widespread application and usage, RFID poses security threats and challenges that need to be addressed properly before deployment. This post aims to highlight several important RFID related security issues. … [Read more...] about Top 10 RFID Security Concerns and Threats